pfSense with OpenWRT Guest logon with VLAN
-
For anyone following I'm not sure how I didn't see this earlier:
https://forum.openwrt.org/t/what-happened-to-eth1-now-that-we-are-using-dsa/89807
That's exactly what I was querying in this thread previously. The take-away being:Yes, the DSA framework currently only supports a single CPU port; eth1 -while present- is ignored by the kernel for the time being.So you can only use a single NIC queue. That's pretty much the difference between our own 1100 and 2100 and the performance difference there is huge.
At least at some point it will probably be restored. Still no idea how the user is expected to configure it though.

Steve
-
@stephenw10 Thanks for posting that here Stephen. Everything is still working smoothly on this end. The "stable" release of v21 still doesn't support what we found/fixed, but it still works fine in the snaphost version we used. I'm testing the rc6 of v22 and will be rolling my configs to whatever the release of v22 will be. Keep your ears on, I'm stirring up a new esoteric stew on the ethernet side this time.
-
Yes, it seems like a solid device. I've been updating snapshots periodically. Bit of a PITA having to reinstall Luci every time but....
The only thing that doesn't work are the LEDs. A number of the defined LEDs do not work at all or do something unexpected. Are you seeing that? Not really a huge deal.Steve
-
@stephenw10 I've not experienced any issue with LEDs (edit see PS)... and I used that device for about 6 rotations of bench test vs. live network test mules. hmmm. I do use the System/LED Configuation drop down to change the WAN connection to an amber, but otherwise leave it alone. That's only because the power LED does weaken but works substantially better as amber.
Yes, after changing snapshots 4 or5 times, reloading LuCI got to be a pain - especially since I don't like putting unconfigured machines on the network. I'd been following the 22.03 development so when they put out rc4, I just switched over to 22.03. Fortunately those builds do come with LuCI pre-installed.
I do take a config backup, reset to defaults, then update from a squashfs-factory image each time. Then all I have to reload are WPAD and the ip-bridge diagnostic.
PS: on these 3200s the LEDs for the two radios seem much, MUCH more durable than the older 1900s and 1200s. The constant flicker of the 2 radio band LEDs weakened them to a point you could only see them in a pitch black room. I have a hand full of surface mount LEDs left from replacing mine on the older boxes. Let me know if you need a couple.
-
@stephenw10 Thanks again for all your help, I really didn't feel like putting the Ver 21 snapshots into full use on my Dumb-APs then they stopped development on V21 and V22 RCs started coming out. I did testing with rc 4, 5, and 6 and they all looked promising so I just sat on rolling out the VLAN guest network on the WRT3200ACMs I have. Finally, Ver 22.03.0 (stable) was released so I have upgraded all my Dumb-APs and implemented the Guest network delivery via VLAN. I also had a need to have an ethernet IOT network pushed out over the backhaul connections to the remote routers. Again, your help made that easy to provision as well. I now have Guest network running on a separate network IPv4 with client isolation and a IOT network hard wired through another VLAN to run IP cameras at the out buildings on my property. All is well.... well, not quite.
The new provisioning is getting IP addresses via the VLANs and DHCP servers on pfSense. The configured OpenWRT Network on the WRT3200ACMs seem functional. Web pages load just fine. But, I came across something early this week I can't get to work. Whether the Guest network WiFi or the IOT ethernet, neither will allow a Speedtest (ookla) to run. The devices, WiFi or ethernet on the primary networks do. Whether using the Speedtest.net website or their App, once you get it up, when you hit start it says connecting and just pinwheels until it stops and says "Test failed to complete. Check your internet connection and try again". Any Ideas??
-
Hmm, that's curious. Any other sites that fail?
Do you have captive portal running on either?
Speedtest doesn't require anything special usually.
-
@stephenw10 If I had to guess maybe 8080 is blocked.. If can not talk on 8080, it can not find a server to test to, and would fail to start..
If I block 8080 I get this.
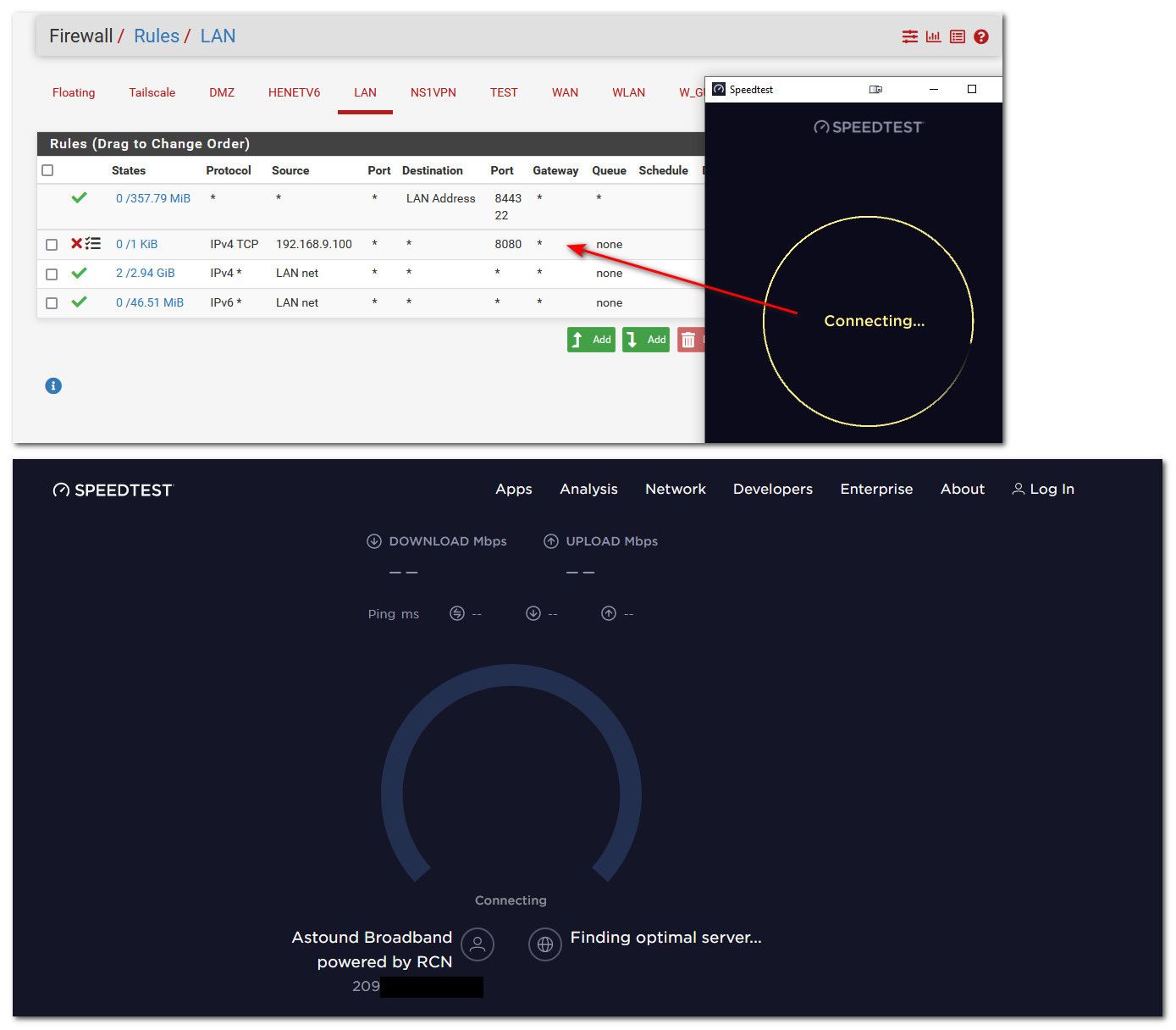
-
Oh, nice! Yeah, almost certainly that. Learned something today.

-
I learned that lesson earlier myself.
And just to let you know, maybe take a look at FreshTomato and if your device is supported. It is much easier to set up.
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Hmm, that's curious. Any other sites that fail?
Do you have captive portal running on either?
Fail, not that I am aware of. Just Speedtest so far. Oddly, devices (even iOS) on the WiFi connections are unaffected.
No, don't run captive portal. I'm really rural and my guest count is single digit.
-
@johnpoz Yep, that's the exact indication I get. I do not have any rules blocking 8080. My rules on the VLANs block all of them from accessing LAN and accessing each other. LAN has access to all the VLANs. I don't run any rules, routing or dhcp on the blue box routers. They are all just Dumb-APs on a physical backhaul,
Observation: on an iOS wifi client on the routers, I can see this same result. But, if I play around with the test server I can get it to work.
So....
I know there is some scuttlebutt around the net about some (especially streaming) services playing games with Starlink clients since they often have out of state POPs. It would have to be unfortunate timing on my part that this problem cropped up just as I implemented the VLAN isolation to my routers. I'm very rural and did a lot of the early Beta testing for Starlink and it is a game changer for rural so I won't be switching. But there are factions out there with disdain for Musk so I'm not saying it isn't possible. If I use the speedtest util built into the Starlink software, it works every time.I don't think this is a pfSense problem but that is just a gut feeling. I can't seem to find the real reason.
And yes the little "John Poz" voice in my head keeps whispering "the solution starts with U"
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
I do not have any rules blocking 8080.
But do you have rules limiting to only specific things? Simple thing to do would be to sniff the traffic and then fire up the speedtest web or app, and see where it tries to go..
If it works with specific servers - some of their servers don't use 8080, etc..
Are you routing traffic on these vlans out a specific gateway, like a vpn or something?
-
So, I just let this stew and used the Speed Test available with the Starlink console... which worked fine. Quite a few people came up with the same issue and a few posted information to show that some (not all) ISPs and hosts were definitely blocking direct Starlink traffic via the Ookla website or app. You could use a VPN and get around the blocks too. Anyway, it all seems to be working without a VPN now. So, yep, it was just a coincidence this happened as I turned up some VLANs. I thought I'd done wrong... but with all you guys helping... how could I??
-
The more I learn the more I discover I don't know.

-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
The more I learn the more I discover I don't know.
So freaking true!
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
The more I learn the more I discover I don't know.

You have learned that valuable lesson early.
As a retired development engineer, I look back and can honestly say my best take on your statement and of modern technology is that the more I know about something, the worse the product was from the beginning.
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
the more I know about something, the worse the product was from the beginning.

-
@stephenw10
Is there any chance to make step by step guide about connecting openwrt dump access points to pfSense using vlans to isolate insecure devices such as phones cameras guests...
Thanks/
Nikos -
Right now is a terrible time to write such a guide because depending on which architecture the openwrt device is it may or may not have been converted to DSA. And that changes the way ports and interfaces are handled significantly!
In pfSense you just create a VLAN interface on the parent NIC the AP(s) is connected to and assign that as a new interface with the appropriate firewall rules.
You would have to add that VLAN to any switches in between pfSense and the AP(s).
In OpenWRT you would:
Create a VLAN device on the appropriate eth device.
Create a bridge that includes that new VLAN device.
Assign that bridge as a new interface.
Create a new SSID and set that as attached to the new interface.Doing that replicates the pre-configured br-lan interface but for the new VLAN.
That assumes an OpenWRT device that doesn't have a switch or at least isn't connected via the switch.
Steve
-
Thanks a lot.
Nikos