only allow access to Internet via single gateway
-
I am attempting to only allow access to the Internet via a single WAN connection.
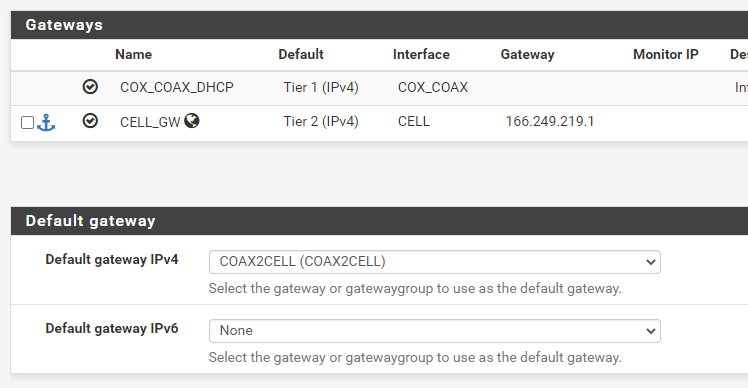
I have the default gateway set to use a group with two circuits to ensure that the firewall itself always has a connection.
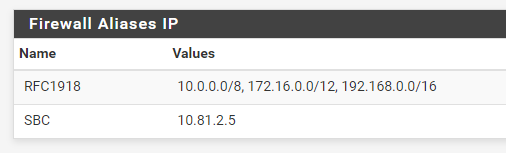
I created an "RFC1918" alias that should represent internal traffic.
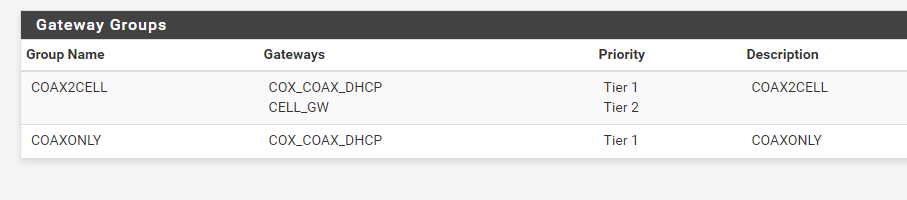
I have a Gateway group that only has my primary circuit in it.
And a rule that should (in my mind) match any Internet bound traffic and force it to go over said gateway.
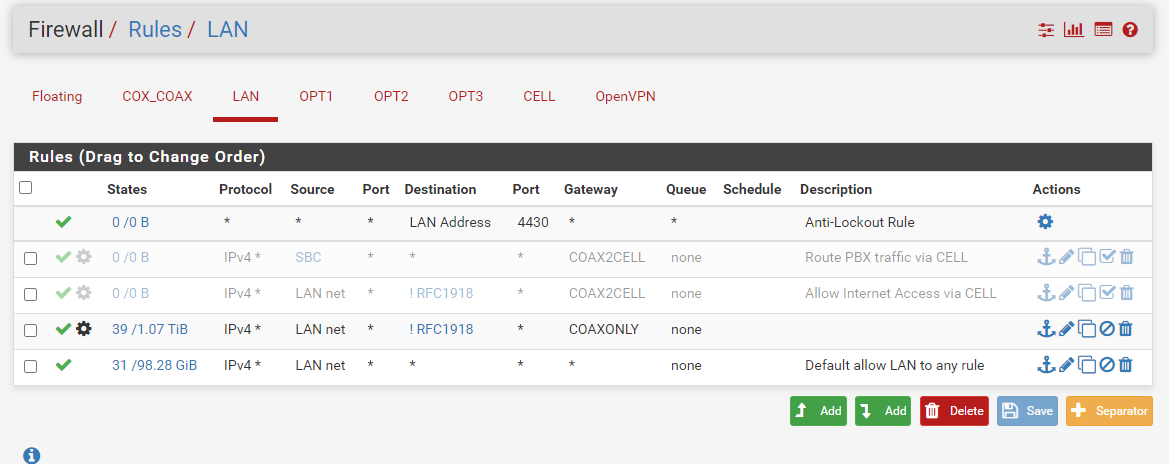
Unfortunately, this doesn't seem to work, and a number of devices on the internal network are able to make outbound connections over the backup circuit.
What am I missing? Is there a better way to do this?
-
@coreybrett I think you're missing the block rule:
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#enforcing-gateway-use"LAN to any" will also pick up traffic from LAN to other interfaces or pfSense itself.
-
Wow, not sure how I missed that in the docs. Thanks!
-
@coreybrett disable your last rule which gateway any any
or coaxonly do not use rfc1918 traffic use any any
-
I'm using the RFC1981 alias to block Internet traffic, without blocking traffic for other LAN networks
-
@coreybrett so on last rule set your specific gateway route
thanks
-
@coreybrett RFC is mostly uses on WAN side not on lan side due to some issues like syslog or other reporting gateway on LAN
thanks
-
@ahsunh said in only allow access to Internet via single gateway:
@coreybrett so on last rule set your specific gateway route
thanks
I've tried that in the past, but it breaks inter LAN traffic. Using the suggested fix from SteveITS seems to have done the trick for me.