IPSec local network subnet size and NAT size error
-
Hello,
We are getting this error when trying to save our IPSec phase 2.
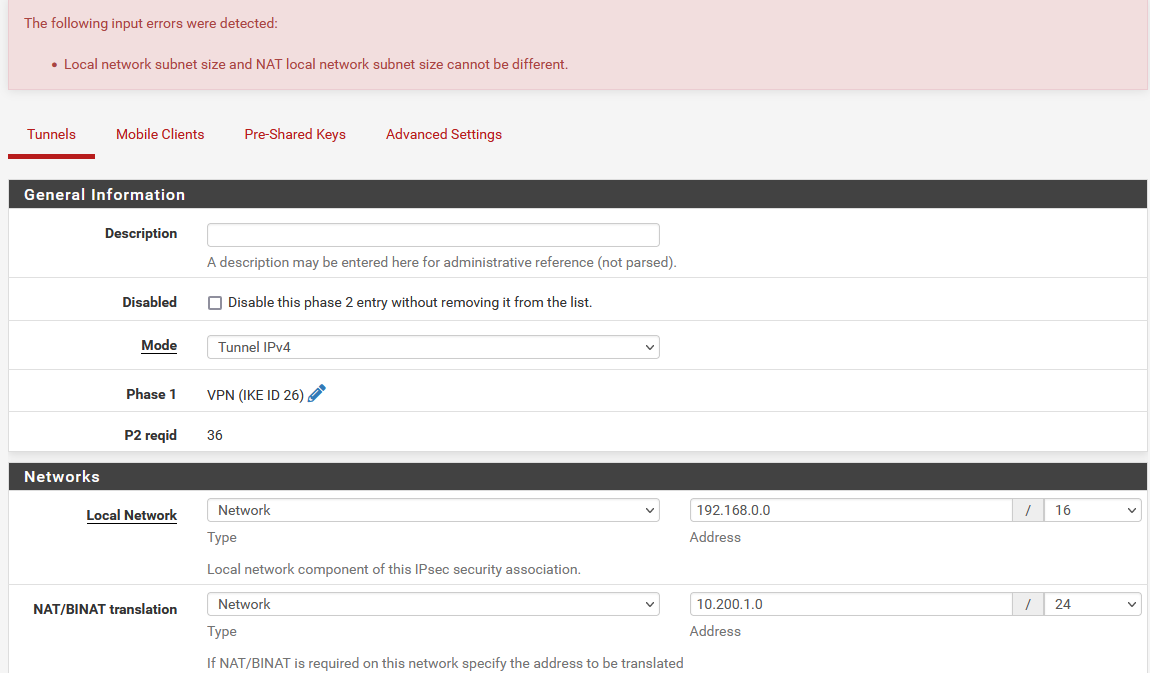
I found this on the bug-tracker: https://redmine.pfsense.org/issues/12851
Like the author of #12851 we heavily used IPSec phase 2 entries like this in Pfsense 2.5.x but now with 2.6 we can no longer create new phase 2 entries like this.
My questions are,
- Why was this not working propperly as stated by Jim Pringles?
- What should i do as workaround, disable the check in the php code since we never have had any issues with this setup (40+ ipsec tunnels working great)?
Edit: Additional background.
We use several local networks inside 192.168.0.0/16 (for example 192.168.4.0/24, 192.168.236.0/24, 192.168.238.0/24 etc) and we want all of these to be able to use the ipsec phase 2 to reach the other side. The other side does not allow us to use a /16 block so we are forced to use /24 as NAT. -
@ceaxe said in IPSec local network subnet size and NAT size error:
[...]- What should i do as workaround, disable the check in the php code since we never have had any issues with this setup (40+ ipsec tunnels working great)?
I used NAT/BINAT translation type Address with success.
With some VPN peers it is possible to open a phase 2 using only a single address instead of a whole subnet. If this does not work, you have to renegotiate with the admin of the VPN peer that your side of the VPN traffic selectors shall be only one address. -
@mamawe As far as I know that type of NAT has never been valid on an IPsec tunnel. You can do 1:1 or Many:1 but not Many:Some_Other_Size_Many.
If it worked for you it was simply by coincidence/accident.
WebGUI validation of the same was added here:
https://github.com/pfsense/pfsense/commit/253b9b62f9f0454550dc8b829e3cbc0b05e6b9e7
The proper solution is to use either a subnet of the same size for 1:1 NAT or use an address.
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/phase-2-nat.html#nat-types
-
Thanks for the replies.
We have previously done different subnet sizes and then manually added BNAT 1:1 NAT rules to get the routing correct.For example this Phase2,
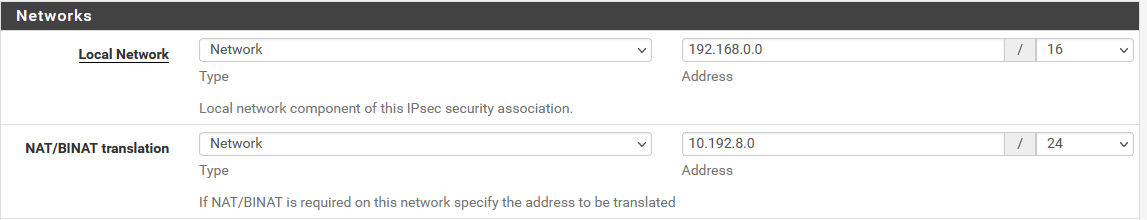
With these 1:1 nat rules NAT our local networks.
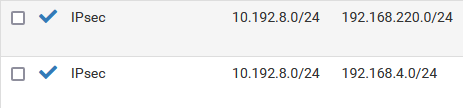
I understand now that our setup only worked since we manually created BINAT 1:1 rules for our different subnets.
Is it possible to tell ipsec phase 2 we manually want to create the nat rules?
For example changing my initial setup to this,
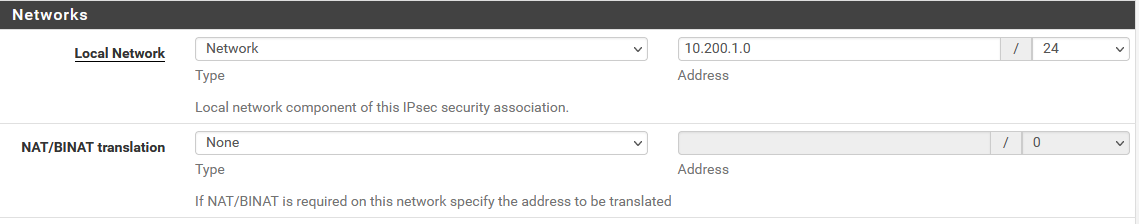
Would i be able to manually create BINAT 1:1 NAT rules for 10.200.1.0/24 <=> 192.168.4.0/24 ?
-
@ceaxe You can do anything you like but the NAT in the IPsec tunnel definition has to be 1:1 BINAT or Many:1 (Overload).
If the NAT entry is not set in the Phase 2 definition the traffic is not interesting to IPsec so that NAT rule in the second example will not work.
-
@derelict ok so if i understand your reply correctly i have to set a Ipsec NAT/BINAT translation or else ipsec will not process any additional NAT rules i may create in Firewall -> NAT?
-
@ceaxe Right. Because without the NAT set in the IPsec P2, traffic in at least one direction will not match the traffic selector and will not be placed into IPsec.
-
@derelict said in IPSec local network subnet size and NAT size error:
@mamawe As far as I know that type of NAT has never been valid on an IPsec tunnel. You can do 1:1 or Many:1 but not Many:Some_Other_Size_Many.
Maybe it wasn't clear from my answer.
I used Many:1-NAT and 1 address for our side of the VPN traffic selector.The last two sentences referred to the peer VPN gateway.
Some implementations allow to negotiate a smaller traffic selector in phase 2 as was configured (1 address instead of a subnet). With these you don't have to change anything at the peer VPN gateway.
If the peer VPN gateway insists on using the correct traffic selector, you have to have the peer VPN configuration changed.