How do I forward GIF interface traffic?
-
I double-natted (full cone) a connection that used to be delivered over PPPoE and I'm struggling getting the GIF tunnel interface from Hurricane Electric back up.
I attempted 1:1 NAT with an allow anything rule, with one of this:
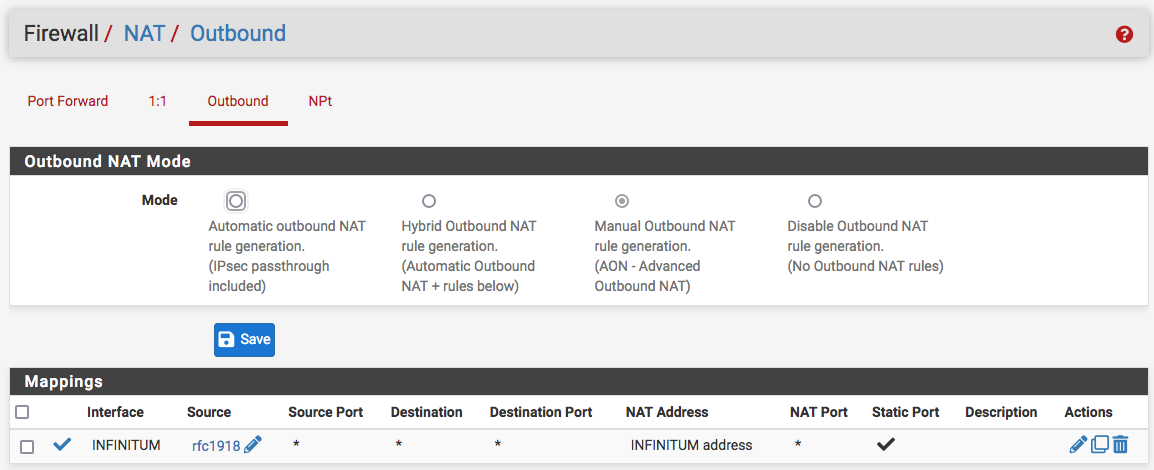
…to cover all my bases. No luck. Don't know how scattered brain and all I remembered about this (largely unreferenced) bit:
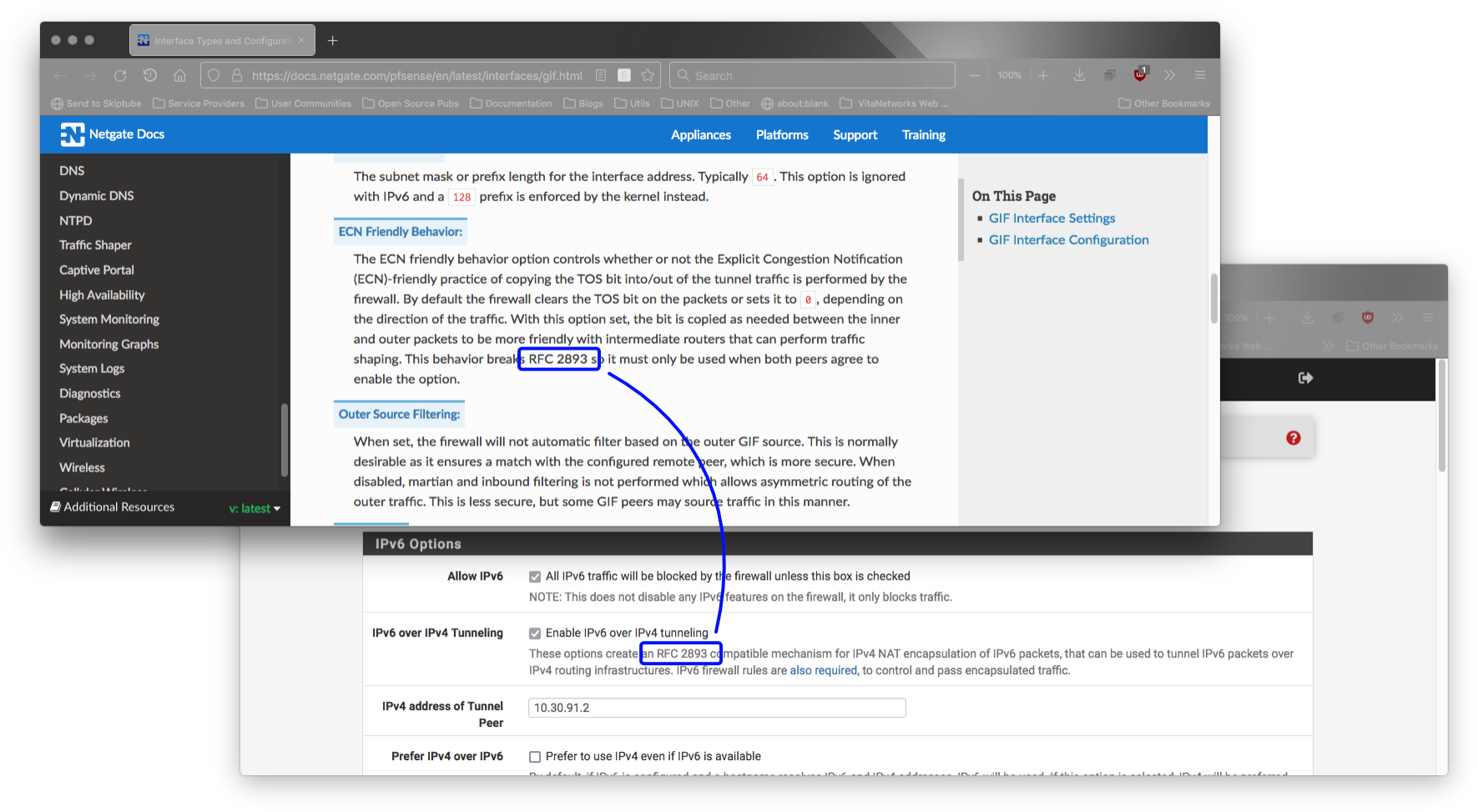
So I read carefully…

"…to a host behind this firewall instead of handling it locally." My cue.I did not need firewall rules; because of the free-for-all rule and the 1:1 NAT, it should be fine, I
assumeddeducted* ️
️ ️ and it worked. I just came to brag.
️ and it worked. I just came to brag.End of thread, thanks for reading—JK.

I switched off 1:1 NAT and natted by proto instead:
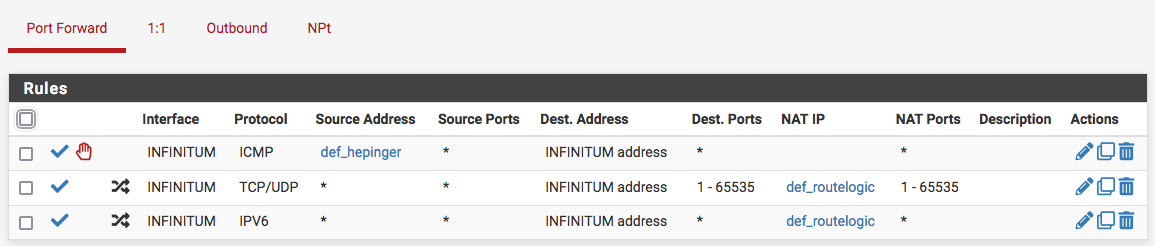
At first, there wasn't the IPV6 NAT rule because I thought specifying that in the Advanced System settings would take care of that, when that didn't happen I added the NAT rule and made it create its own associated firewall rule to make sure I was avoiding as many mistakes as possible, then deleted the manually created "IPV6" protocol firewall rule afterwards:
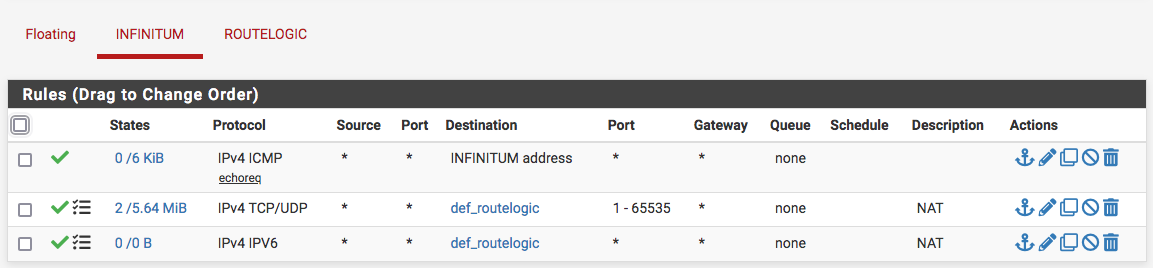
It left essentially the same results but with the twisting arrows icon next to the rule.Last thing I noticed after all of this, is that the outtermost firewall doesn't even acknowledge the traffic:
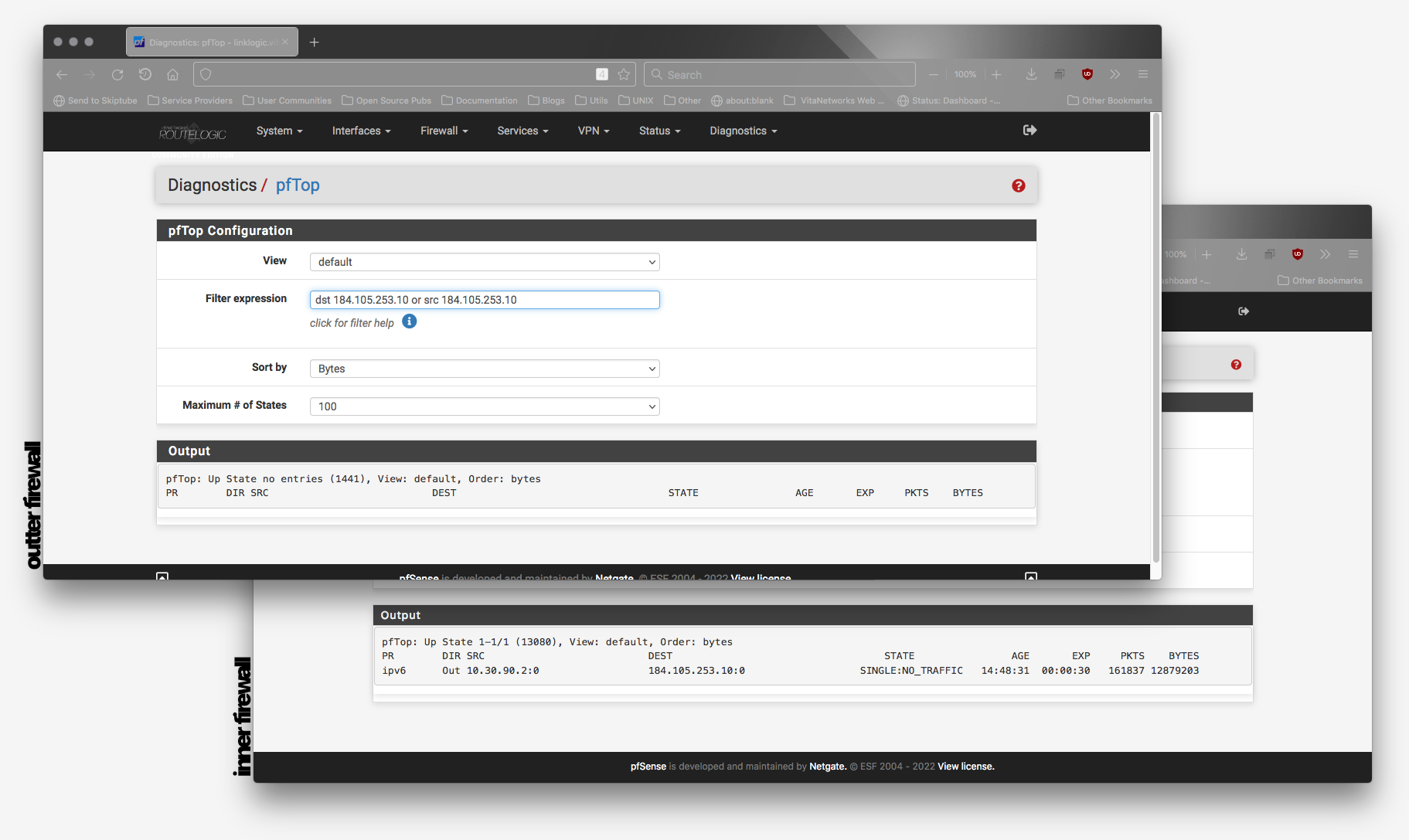
…but there's the rule:
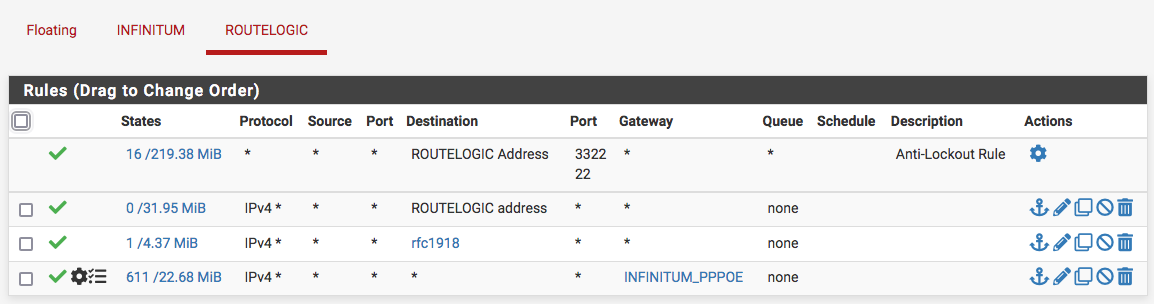
The gateway in the rule was just added while I double-checked before posting this. Speaking of gateways, the sole client the outermost firewall has, is also listed as a gateway for it, so this firewall can reach without NAT certain inner hosts, BTW. It's even using an internal host as the monitor IP, not the gateway(client/inner firewall) itself:
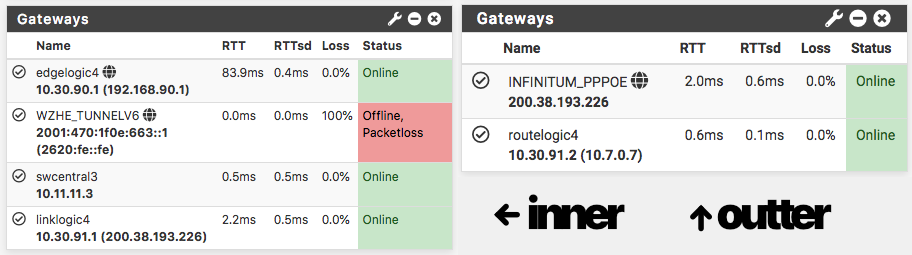
I know I'm screwing up… where though? (I mean, leaving out the fact of the double NAT :P)Oh well, I'm taking a little break, hopefully the routing fairy has a GIF or something for me when I come back… :)
*: any excuse to use that emoji.
-
@skilledinept IPv6 doesn’t use NAT. Firewall rules are necessary on the HE interface to allow traffic (there’s a default block rule).
My son woke me up early today so I’m not caffeinated but did you create an interface?
https://docs.netgate.com/pfsense/en/latest/recipes/ipv6-tunnel-broker.html#create-and-assign-the-gif-interface -
@steveits yep-yep. All that. It was working then it stopped. The inner firewall through aliases and gateway groups, didn't change much its configuration during all of this.
It's way too easy to switch an interface interface from something like VLAN on a vNIC(e.g. vmx0.3) to a tunnel client(e.g. ovpnc1), it's a very powerful feature IMO, the problem is that it doesn't always take. :(
It's working again and I still don't know the answer.
I changed an interface on the inner firewall, completely unrelated--it's internal, I just assigned another from the list like I mentioned before and no more config changes done. Back on the dashboard the HE gateway was now working.
So I thought, maybe it was the config not taking. At least I now knew all this time was on the inner firewall whereas all my focus was on the external one. It was misrouting, that's why there was no traffic on the external one.
The GIF tunnel uses both and IP address and a physical interface; setting a OpenVPN tunnel I learned that even if you set it on an interface that doesn't directly connect to an outgoing gateway it'll still find its way, I verified this again earlier today when I was decommissioning the old tunnel I had replaced: since it's assigned it cannot be disabled, nor I wanted to delete it so I'd have an emergency backup already set up. I set as the interface to the loopback address but it still reached the server.
I've also observed this in the DDNS client in a multiWAN firewall. Regardless of the interface chosen it might go through another. It's likely the same was happening on the GIF tunnel, I think.
But then I restarted the firewall for good measure and the HE interface went down again! Keep in mind that my IP address hasn't changed because it's natted from the outter firewall. HE should just come back. I couldn't make it come back again. So now I'm thinking maybe it even wasn't the firewall at all but something at Hurricane Electric's end. IDK.
Anyway, I made so many changes trying to make it work and to present a reproducible problem that I strayed too far from what it was. Then I eliminated double NAT because—why not.
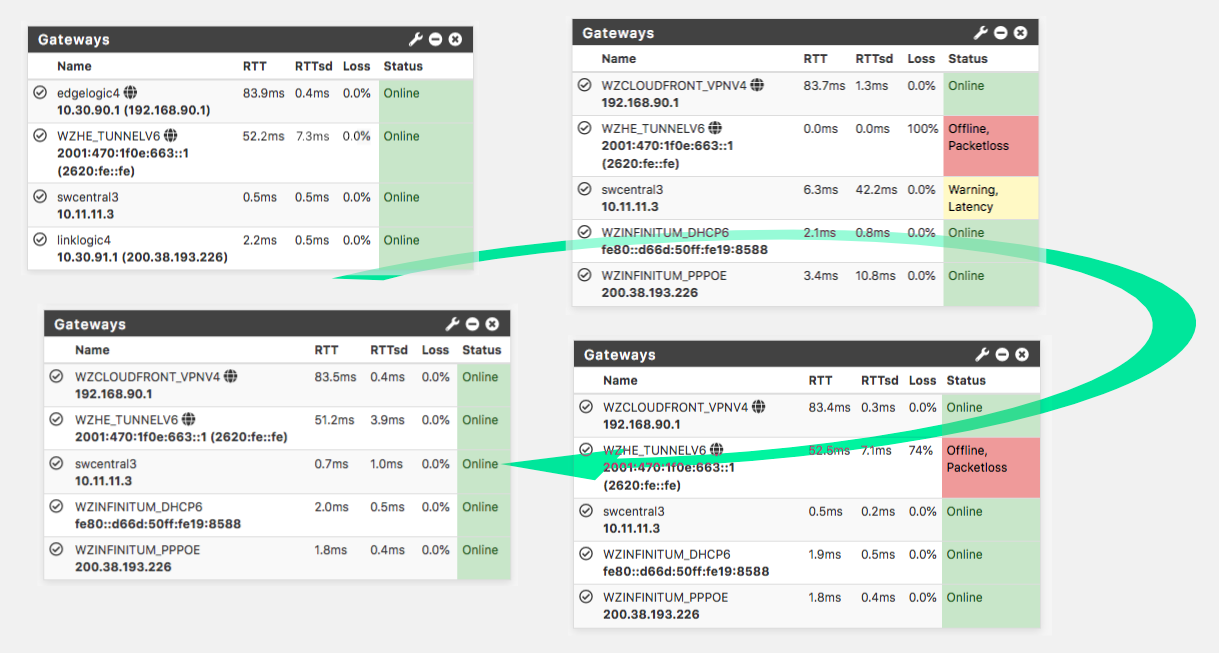
I made a backup of the config before starting and my history is set up for something like 300 or 500 (it takes forever to start too), I could get back even without the backup. But now that it's normal again, I think I'll stop messing with it…at least for the week. It was frustratingly fun though.
Thanks anyway for answering— have a great week!
-
@skilledinept “back away slowly“ as they say.
I recall now when I first set up HE I had to reboot for it to work. Reproduced, entered bug report, and couldn’t get it to happen after that.