VPN Client - Cannot Access subnet
-
I have connected to NORD VPN from one of my LAN PC ( 192.168.1.50 ) using pfsense and OpenVPN. Everything works as expected. I can ping all my LAN devices ( 192.168.1.0/24 network ) from 192.168.1.50 after connecting to Nord VPN.
However I cannot ping any of the device in different subnet ( 192.168.5.0/24 ) from 192.168.1.50. The ping works fine if I disconnect OpenVPN.
VPN network is 10.8.0.0/24. I am running VPN client in pfsense and the used policy based routing to send only 192.168.1.50 via tunnel.
I get the following error message when I ping 192.168.5.25 device.
from 10.8.0.1 icmp_seq=1 Destination host unreachableI couldn't make it work yet after the following experiments experiments. Any help is appreciated.
- Added firewall rules in the VPN client interface to allow all the traffics
- Added outbound NAT rules with source as 192.168.5.0/24 for VPN client interface
- Added a static route in the VPN client PC ( 192.168.1.50) with the following command.
sudo ip route add 192.168.5.0/24 via 192.168.1.1 ( 192.168.1.1 is my pfsense router )
Is there any change that need to make the VPN client config for this? Any help is appreciated.
-
@yogi_en so your nordvpn is setup on pfsense, or the client?
If you connected vpn on pfsense, and you want your clients on lan to get to one of your other networks, you just need to setup rules to allow that before you send traffic to your vpn.
Could you please put up your lan rules from pfsense..
Here is info about bypass policy routing.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
-
@johnpoz NordVPN client is running pfsense ( not on the client device )
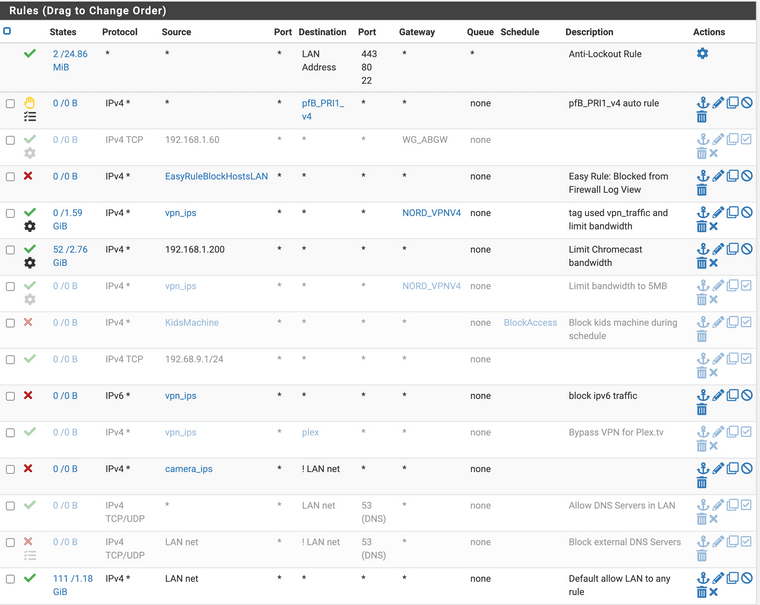 .
.I have attached the Firewall rules for LAN. Please see the rules with source as 'vpn_ips'. vpn_ips are set to 192.168.1.50 as of now.
-
@johnpoz , Thanks a lot!. It woks now. I added a rule above vpn_ips as you suggested. Now I can ping. I have been struggling with issue for the last couple of days. Thanks a bunch again!
-
@yogi_en yeah I would just going to ask what was in that alias where your forcing it out your vpn
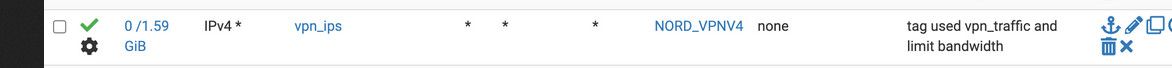
You would need a rule above that that allows those IPs to get to your other network.
So your all sorted now?
-
@johnpoz Yeah!. All sorted out. Thanks for your help!
-
A related question. I want to route all the traffic from one of my Docker container ( IP is 172.12.0.2 ) through the VPN tunnel. I added 172.12.0.2 as part of vpn_ips alias, but this doesn't seems to be working. Any ideas?
vpn_ips = 192.168.1.50, 172.12.0.2
Note: 192.168.1.50 traffic is going through the VPN tunnel as expected.
-
@yogi_en Your docker IP is not that, that is different network - its being natted..
example here are my docker Ips
budman@NAS:~$ sudo su ash-4.4# docker inspect -f '{{.Name}}-{{.NetworkSettings.IPAddress }}' $(docker ps -aq) /heimdall-172.17.0.2 /tautulli-latest-172.17.0.3 /sctx-overseerr-dev-172.17.0.4 /confident_perlman-172.17.0.5 ash-4.4#But those are all natted to my nas actual IP on the network 192.168.9.10, just on different ports. If you want your docker to be on your actual 192.168.1 network you would have to setup a docker bridge.
you can see what ports are natted to the nas IP with
ash-4.4# docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 8dd5d07807de linuxserver/heimdall:latest "/init" 3 days ago Up 3 days 0.0.0.0:8056->80/tcp, 0.0.0.0:4443->443/tcp heimdall 99919927e2a2 tautulli/tautulli:latest "./start.sh python T…" 3 days ago Up 3 days (healthy) 0.0.0.0:8181->8181/tcp tautulli-latest 1886118dee2f sctx/overseerr:develop "/sbin/tini -- /bin/…" 5 weeks ago Up 3 days 0.0.0.0:5055->5055/tcp sctx-overseerr-dev f1ab0ab01951 mynttt/updatetool "/bin/sh -c /usr/app…" 3 months ago Up 3 days confident_perlman ash-4.4# -
@johnpoz Thanks again for the detailed answer as usual. What is the best way to redirect docker container traffic though VPN Tunnel?. Is it via creating the bridge network?
I tried redirecting the traffic based on the docker port though the VPN tunnel earlier ( using firewall rules ). Some how it was not working, could be a mistake from my side.
-
@yogi_en does this docker go somewhere specific? Is so you could policy route via the destination.
If you don't know exactly where this docker might go (ip or port?), but you know you want to send it out the vpn then best option would be to make sure this docker actually gets an IP on your 192.168.1 network that is different then the docker host. That way no matter where this docker goes you can route it out the vpn via the docker actual IP on the 192.168.1 network
For docker to get an IP on the actual network the host is on, you need to setup a bridge in docker vs just the normal natting that happens. If you don't you don't actually know what traffic is leaving the host - it could be host traffic or docker traffic, etc. because its all coming from the host IP.
I have not played with this in a really long time - but believe you have to do something with macvlan as well on the docker.. This allows you to assign a unique mac address for the docker on the host interface so that host can be say 192.168.1.x and docker can have 192.168.1.y This way you can policy route 192.168.1.y traffic out your vpn connection.
-
@johnpoz Thanks!. Looks like setting up the bridge in docker is better suited for my needs. I don't know where exactly docker traffic go i terms of IP and Port.
Will also explore macvlan. Thanks again!