DNS Host Override not working
-
I have a host override for my internal nas:
nas.domain.tld -> 172.16.1.4,172.16.1.5 (it has two interfaces)
When I dig the host, I get back the correct answer: 172.16.1.4
However, when I try to access the site, I land at a DNS rebinding warning for the router (router.domain.tld) GUI. Moreover, if I try to traceroute to nas.domain.tld, I get back the WAN IP address.
This was all working until maybe three months ago. I've torn my hair out trying to find a combination of settings that works, but nothing fixes this. Hoping the community can help!
-
@cryptos said in DNS Host Override not working:
if I try to traceroute to nas.domain.tld, I get back the WAN IP address.
WAN IP = the pfSense WAN IP, right ?
And that is correct, your "nas.domain.tld" should point to your pfSense WAN IP.You have also a NAT rule, that maps "any IP" (from WAN) using port x to the internal LAN IP, using port x, or some other port, using TCP.
Right ?
And this NAT rule created an firewall rule on the WAN interface.Visitors that connect from somewhere from the Internet will never use the pfSense DNS to reach your NAS.
The local "host override" doesn't come into play here.@cryptos said in DNS Host Override not working:
I land at a DNS rebinding warning for the router
The router is pfSense ?
-
@gertjan said in DNS Host Override not working:
@cryptos said in DNS Host Override not working:
if I try to traceroute to nas.domain.tld, I get back the WAN IP address.
WAN IP = the pfSense WAN IP, right ?
Correct.
And that is correct, your "nas.domain.tld" should point to your pfSense WAN IP.
Not from inside, if I understand the point of the host override function: it should point to the internal IP. nas.domain.TLS is not published to my external DNS servers.
You have also a NAT rule, that maps "any IP" (from WAN) using port x to the internal LAN IP, using port x, or some other port, using TCP.
Right ?No. The nas is not (and is not intended to be) exposed to the Internet. It’s internal-only.
And this NAT rule created an firewall rule on the WAN interface.
Visitors that connect from somewhere from the Internet will never use the pfSense DNS to reach your NAS.
I’m aware. That isn’t the the use case here.
The local "host override" doesn't come into play here.
@cryptos said in DNS Host Override not working:
I land at a DNS rebinding warning for the router
The router is pfSense ?
Yes.
-
@cryptos said in DNS Host Override not working:
I land at a DNS rebinding warning for the router (router.domain.tld) GUI.
Here is the thing... If you router is called router.domain.tld, and you put in a host override that points nas.domain.tld to your wan or lan IP of pfsense.. And you hit it on the port your gui is listening on - then yes you would get a rebind warning.
Because to pfsense nas.domain.tld is not its name.. A host override for nas should point to the nas IP not pfsense IP.
if you want to hit pfsense with an different name, then you could put those other names here
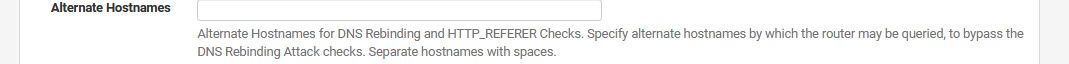
Under advanced, admin access.
But normally a host override is used for say public fqdn nas.public.tld to resolve that to the local IP vs the public IP (your wan). Now clients using your dns locally trying to go to nas.public.tld would go to say 192.168.1.100 (your nas) vs your wan IP 1.2.3.4 to just be nat reflected back to your nas..
You can setup whatever fqdn you want to any IP you want in your host overrides - but if you hit a pfsense IP with nas.localdomain.tld and its name is really router or pfsense.localdomain.tld then that would be a rebind warning..
If you want your clients to resolve nas.localdomain.tld to your nas IP, that should be say the 192.168.1.100 IP of the nas, not some pfsense IP.
Here example some host overrides of mine.. If I ask unbound running on pfsense for nas.local.lan I get back the IP of the nas (192.168.9.10)
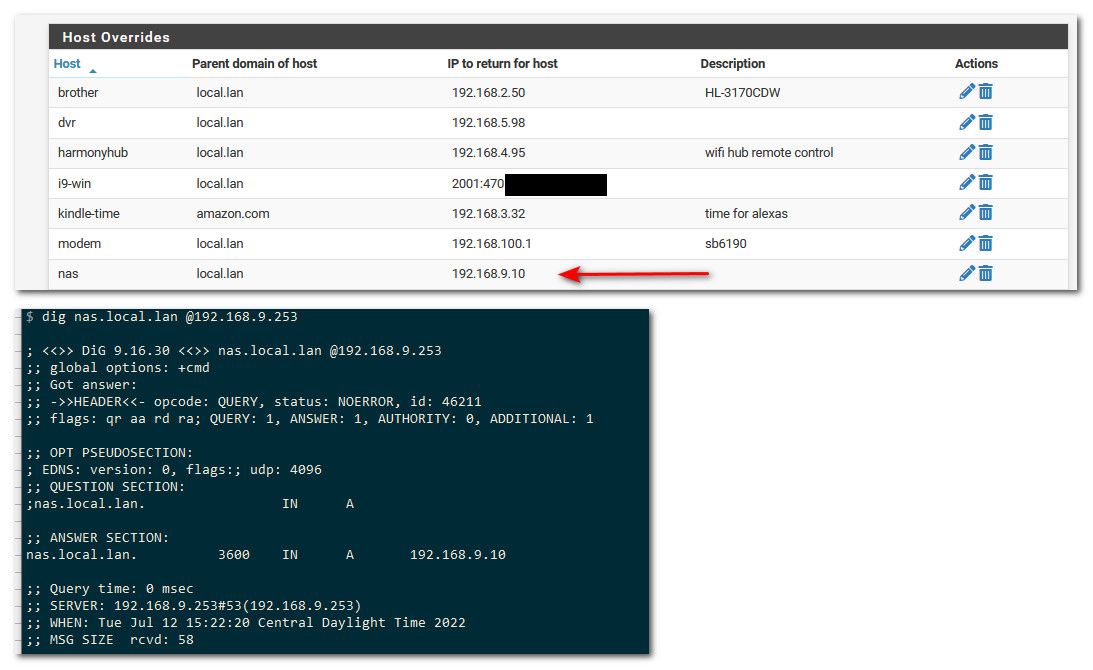
-
Apologies if I was unclear, but my nas override DOES NOT point to any of my pfSense box’s IPs. It points to the DHCP-reserved IP of the nas’s ethernet interface.
Here’s the setup:
router.domain.tld > 172.16.1.1
Host Override:
nas.domain.tld > 172.16.1.4I have verified that a DNS lookup against nas.domain.tld returns the correct IP address.
However, when I type nas.domain.tld into a browser, I get the aforementioned rebinding notice from the pfSense box. This is the behavior I can’t explain.
-
@cryptos well then there is no way you would hit pfsense IP to get that rebind warning - just not possible..
This is the behavior I can’t explain.
Your browser using doh maybe? And its resolving that fqdn to pfsense IP then..
What does nas.domain.tld resolve to on the public internet? If that domain.tld is public, and you have a wildcard setup then it would point to your wan IP - and that would generate a rebind warning because as I stated nas.domain.tld is not pfsense actual name..
Browsers love to say oh F you admin/user - I am going to use doh for your own good..
If your browser was resolving to that 172.168.1.4 address, which isn't on pfsense then there would be no way for you to get a pfsense rebind warning.
If your browser is firefox you should be able to go to
about:networking#dnsin your address bar and see what it shows for the fqdn in its cache.
-
@johnpoz said in DNS Host Override not working:
@cryptos well then there is no way you would hit pfsense IP to get that rebind warning - just not possible..
This is the behavior I can’t explain.
Your browser using doh maybe? And its resolving that fqdn to pfsense IP then..
I thought of that, and tested it, but no: When I disable all of the DoT/DoH/ODoH options in Chrome, Firefox, and Safari, I still get the same result.
What does nas.domain.tld resolve to on the public internet? If that domain.tld is public, and you have a wildcard setup then it would point to your wan IP - and that would generate a rebind warning because as I stated nas.domain.tld is not pfsense actual name..
Good thought!
That should return NXDOMAIN, but doesn’t. I think this points to a different issue: I have what is supposed to be a single dynamic DNS entry: connect.domain.tld, which points to the pfSense WAN IP. Weirdly, my dyn provider showed an entry for nas.domain.tld which shouldn’t have existed. I’ve deleted it, and that seems to have cured the issue, for now.
Still doesn’t make sense, though, since the override should have returned the internal IP for internal queriers.
Will see if it comes back!
Thanks for your help!
Browsers love to say oh F you admin/user - I am going to use doh for your own good..
If your browser was resolving to that 172.168.1.4 address, which isn't on pfsense then there would be no way for you to get a pfsense rebind warning.
If your browser is firefox you should be able to go to
about:networking#dnsin your address bar and see what it shows for the fqdn in its cache.
-
@cryptos said in DNS Host Override not working:
Still doesn’t make sense, though, since the override should have returned the internal IP for internal queriers.
Yeah - and you showed it did with your direct query.
These browsers and their doh ticks me off to no end.. I don't think you can view what the browser shows as IP for fqdn in chrome, but firefox you can.. And it should list your doh settings on the top
example
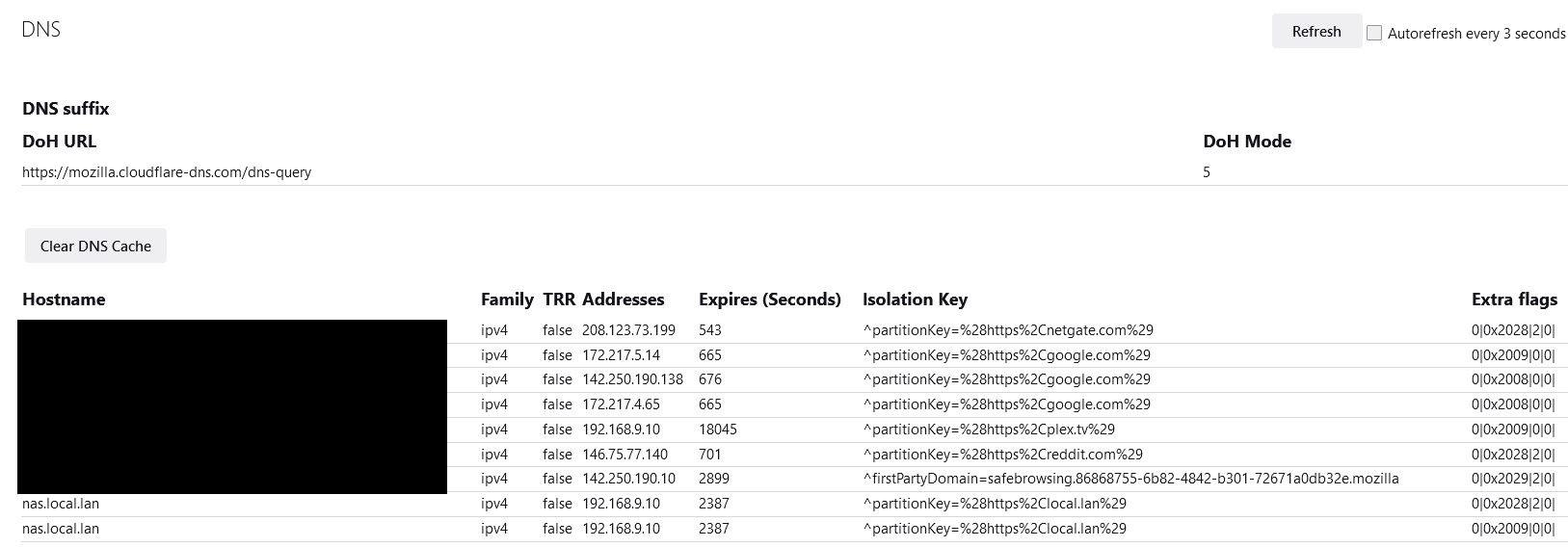
See my nas.local.lan - and what doh mode I am in, and if it came from TRR or not..
5 - Off by choice. This is the same as 0 but marks it as done by choice and not done by default.
You can never trust these guys these days... I have all known doh IPs blocked in pfsense as well.. If you couldn't tell, not a fan of doh ;)