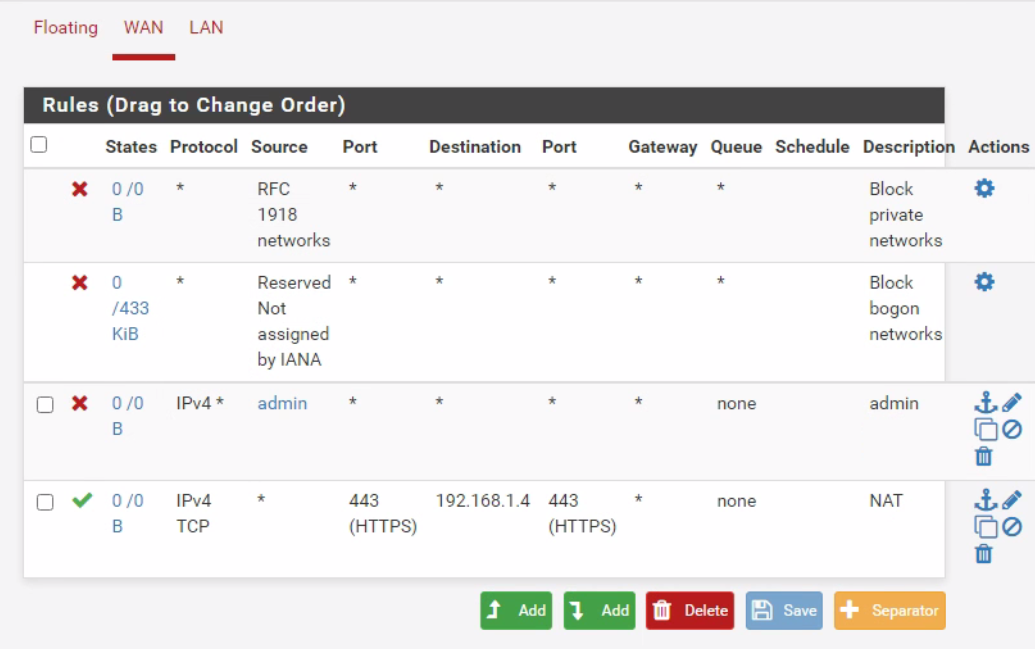
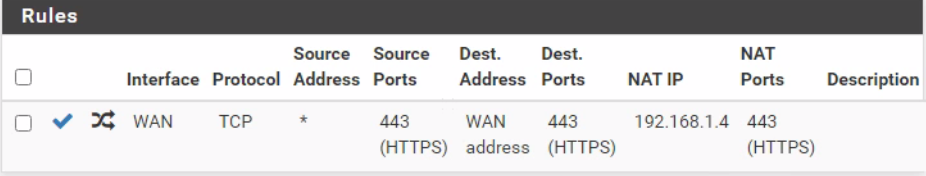
Just trying to forward 443 to an internal server
-
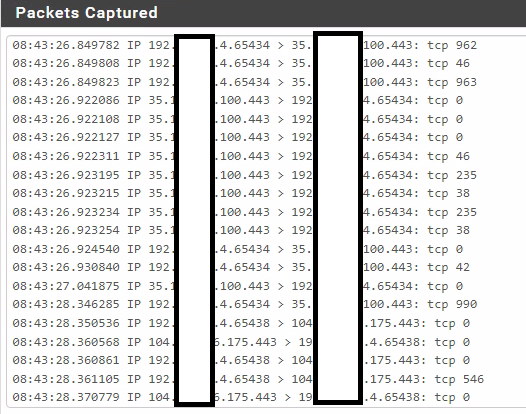
Here is what I'm seeing on the LAN when I run a packet capture and open port checker.
Keep in mind I can get to the web server on 443 just by going to https://192.168.1.4 and it loads without question. I've also tried this with the firewall off.
Also just checked, and the WAN is listing the expected external IP Address.
-
@combat_wombat27 If I'm reading this correctly though this is just showing me traffic of people going to https sites, not something external accessing an internal https site.
-
@combat_wombat27 You need to make sure your sniffing for what your wanting to sniff for, or increase number of packets you capture from the default 100.
I see no traffic "to" 192.168.1.4 port 443, I only see traffic too some public IP on 443 from that picture.
-
@johnpoz okay, I've done the scan again even though I didn't get 100 packets last time, and still there is no traffic to 192.168.1.4:443. So if I'm understanding properly it is hitting the firewall and not making it past.
-
@combat_wombat27 said in Just trying to forward 443 to an internal server:
I've done the scan again even though I didn't get 100 packets last time, and still there is no traffic to 192.168.1.4:443
You can not see the internal IP on WAN. This could only be seen on LAN behind NAT.
Simply filter your capture for " > [WAN IP]:443" in the browser.
-
@viragomann No, that is regarding the internal packet capture to see if the traffic made it inside the network. If you check my replies above you will see where I DID see the packets hit the firewall externally.
-
@combat_wombat27 please post your port forward and wan rules, do you have any rules in floating? If so post them as well.
So you know what IP your testing from, say in the sniff on your wan and the can you see me IP.
Now filter on your lan side for this IP and port 443 in your packet capture..
If you say its hitting your wan but not forwarding it, then you have wrong setup in the rules/port forward, or pfsense does not know the mac address of the device your trying to forward too..
Like you saw my test port forward and wan rules.
-
@combat_wombat27 said in Just trying to forward 443 to an internal server:
If you check my replies above you will see where I DID see the packets hit the firewall externally.
Yes, but I cannot see any confirmation that you even get the packets on WAN.
I was assuming that before based on your first posts, but now I'm not sure anymore. -
@viragomann It's pretty simple. There is a pic showing the external packets hitting my external IP on 443. That said, I marked out the external IP address.
-
@combat_wombat27
In this capture 35.x.x.x might be your WAN and it shows also response from it from port 443.
Regarding this it should work well at all. Or did you disable the port forwarding again and is it pfSense responding here? -
@viragomann No that is not our WAN, nor is it any IP subscribed to our network or firewall internal or external. That is an internal 192 computer talking out to the web. I am not seeing the expected traffic to 192.168.1.4 on 443 as shown in the example images from Johnpoz
-
This post is deleted! -
@viragomann He has talked about both a packet capture on the LAN and WAN side. I've offered proof that the packets ARE reaching the firewall on the WAN side, and that those packets AREN'T making it to the server on the LAN side.
-
@combat_wombat27 said in Just trying to forward 443 to an internal server:
I've offered proof
Where did you offer this - I see no packet capture showing traffic hitting your wan on 443..
-
@johnpoz Okay, I really feel like I'm going crazy here. I would have sworn I saw the packet trace show the firewall received the packets and pasted a screenshot in chat. That must have been inaccurate as I don't see anything. That said, if packets weren't making it to the WAN side interface then how am I able to open up the Web GUI on 443 when enabled.
-
@combat_wombat27 even more interesting. Even though I had tested and remade my NAT rule already, I noticed the 4443 NAT as a test worked. So I just adjusted it back to 443 and it started working.
I still don't understand how I wouldn't be seeing the packets externally if they were making it at least to the firewall. Maybe someone can explain that feat to me.
Anyways, it is working currently.
-
@combat_wombat27 said in Just trying to forward 443 to an internal server:
I still don't understand how I wouldn't be seeing the packets externally if they were making it at least to the firewall
You were not sniffing correctly. You had a filter wrong? You had the wrong interface? etc?
So do you access the forum via the same IP? Because I don't get any response hitting that IP on 443.
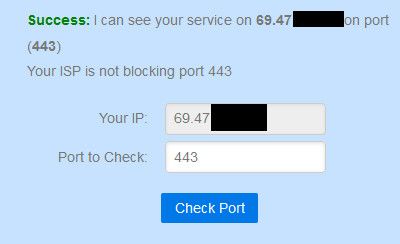
But you say its working? If it was working you would see a successful test on can you see me . org
-
@johnpoz I don't think the filter was wrong as the only difference in the filter I used for testing 4443 was to change the port from 443 to 4443. From there it showed traffic on 4443 just fine. I then switched it back to 443 and did not see the packets reach the firewall.
Yes, it is working and yes I got a Success. No, we are an MSP so we are not at the site where this was being deployed.
-
@combat_wombat27 said in Just trying to forward 443 to an internal server:
I then switched it back to 443 and did not see the packets reach the firewall.
it is working and yes I got a SuccessWell there is piece of the puzzle missing because what your saying isn't possible - how would you access 443, if you are not seeing the traffic?
Your saying its working - so there would be state showing that, etc. If your creating a state, how would you not being seeing the traffic via a sniff - unless your sniff was not actually sniffing on the correct interface, or wrong port or some other error, etc.
When you sniff on wan, do you see other traffic?
-
@johnpoz Yeah. I'm agreeing with you. I don't know how this situation can be factual. I would assume I messed up the capture, but it worked just fine with 4443 just with the port changed.
I do see other traffic on the WAN yes.