bug found: ipsec vpn ipv4 and web management do not work together
-
Hi all,
I am not sure how long this exists (on latest pfsense+ 22.05), I have an ipsec tunnel between 2 routers: using ipv4 addresses as tunnel end point ips
my pfsense is in the cloud and installed on the remote VPS, I can access it via public ip (obviously via trusted IPs that have been setup in the fw rules on pfsense ) the other end is my home and I am connecting from home.
I noticed that every time when I access it (pfsnse) the IP I am coming from is always ipv6, just being curious I disabled ipv6 stack from my network card and could not log in at all via ipv4.
Opened it from the other pc via ipv6, did packet capture: when I try to connect from my pc (same IP v4 as as the remote tunnel end from the pfsense perspective) I see 0 attempts in the logs:
These are the only logs I was able to see, there is no port 443 https logs at all, just port 500 for ipsec
19:09:12.395810 IP 109.107.xxx.xxx.500 (this is the pfsense side) > 121.99.xxx.xxx.500: UDP, length 80 (this is me from home pc)
19:09:12.702034 IP 121.99.xxx.xxx.500 > 109.107.xxx.xxx.500: UDP, length 80======================================================
disabled ipsec tunnel on the pfsense, was immediately able to connect from pc on ipv4 to the remote pfsense
19:10:35.879707 IP 121.99.xxx.xxx.58635 > 109.107.xxx.xxx.443: tcp 0
19:10:35.879853 IP 109.107.xxx.xxx.443 > 121.99.xxx.xxx.58635: tcp 0is that a bug?
thank you -
This post is deleted! -
doing pfctl -d does not help, so wouldn't be the firewall blocking it, looks like a genuine bug
-
Seems more likely to be a routing problem. When you create an IPSec tunnel it adds a static route to the end point via whatever interface the tunnel is using. You probably have a conflict of some sort there.
Steve
-
@stephenw10 said in bug found: ipsec vpn ipv4 and web management do not work together:
Seems more likely to be a routing problem. When you create an IPSec tunnel it adds a static route to the end point via whatever interface the tunnel is using. You probably have a conflict of some sort there.
Steve
Thank you for your support Steve, here is my configuration.
I am using 0.0.0.0/0 as local because Pfsense doesn't have a LAN network, as being a virtual appliance in the data centre. Essentially what I wanted to archive is to route all the traffic from my home fortigate (lan 10.10.10.0/24) via pfsense to the internet. It has been working fine, but yes, ipv4 management of the pfsense (via it's public ip address (as beeing a cloud device) is not working from my local side, but does work fine via ipv6, once ipsec runnel is down ipv4 management is working again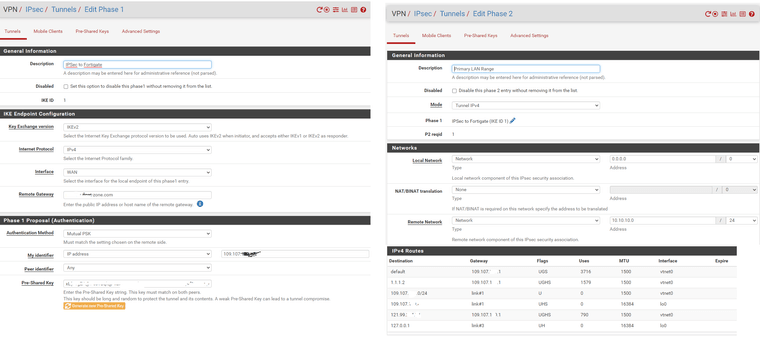
Thank you for any advice
-
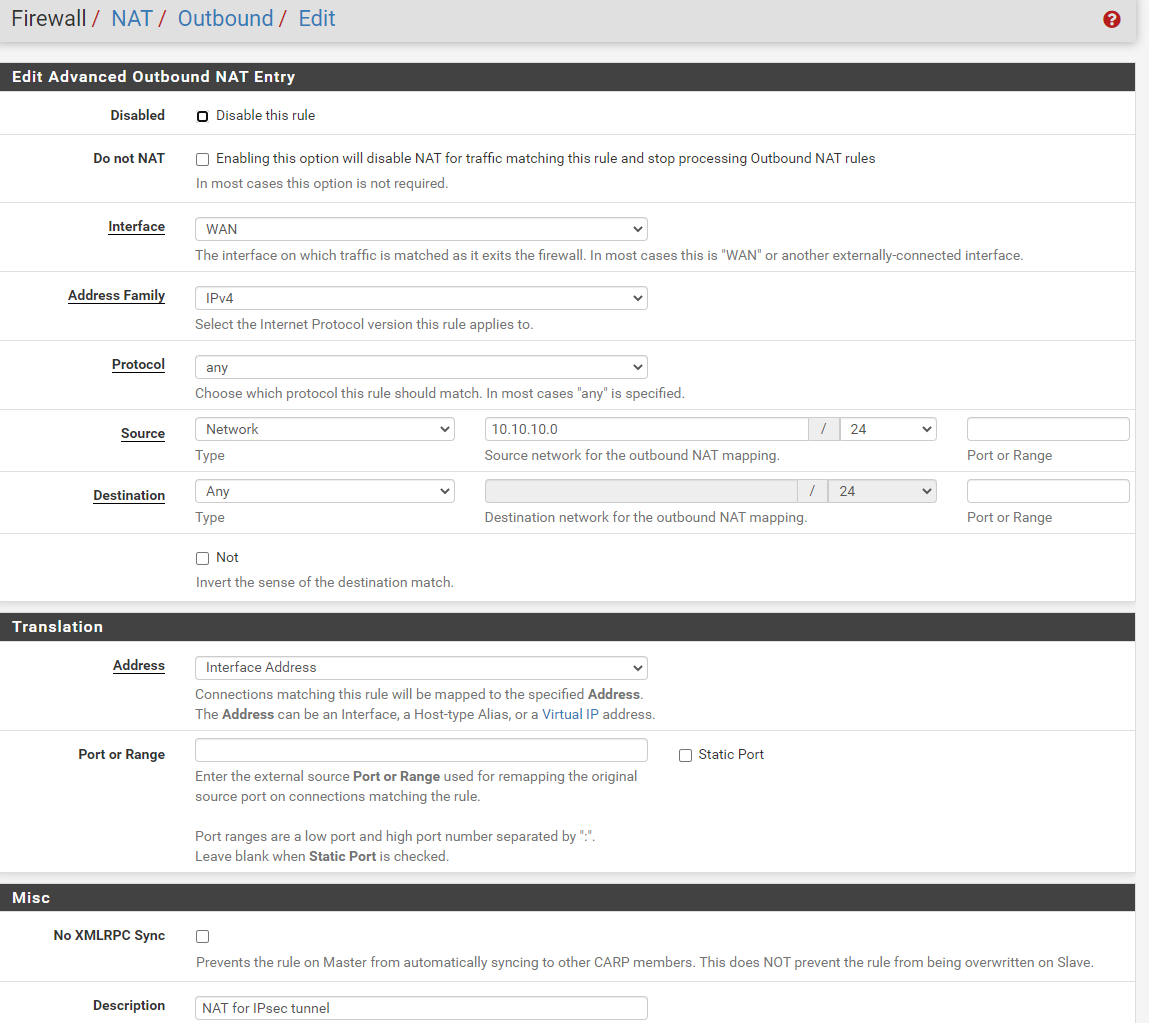
and those are my NAT rules on PFsense
-
the issue has been fixed and was related to the routing configuration but on the Fortgate side, thanks guys!
-
Thanks for the update, glad to hear it's fixed!