Routing traffic between remote offices behind respective firewalls
-
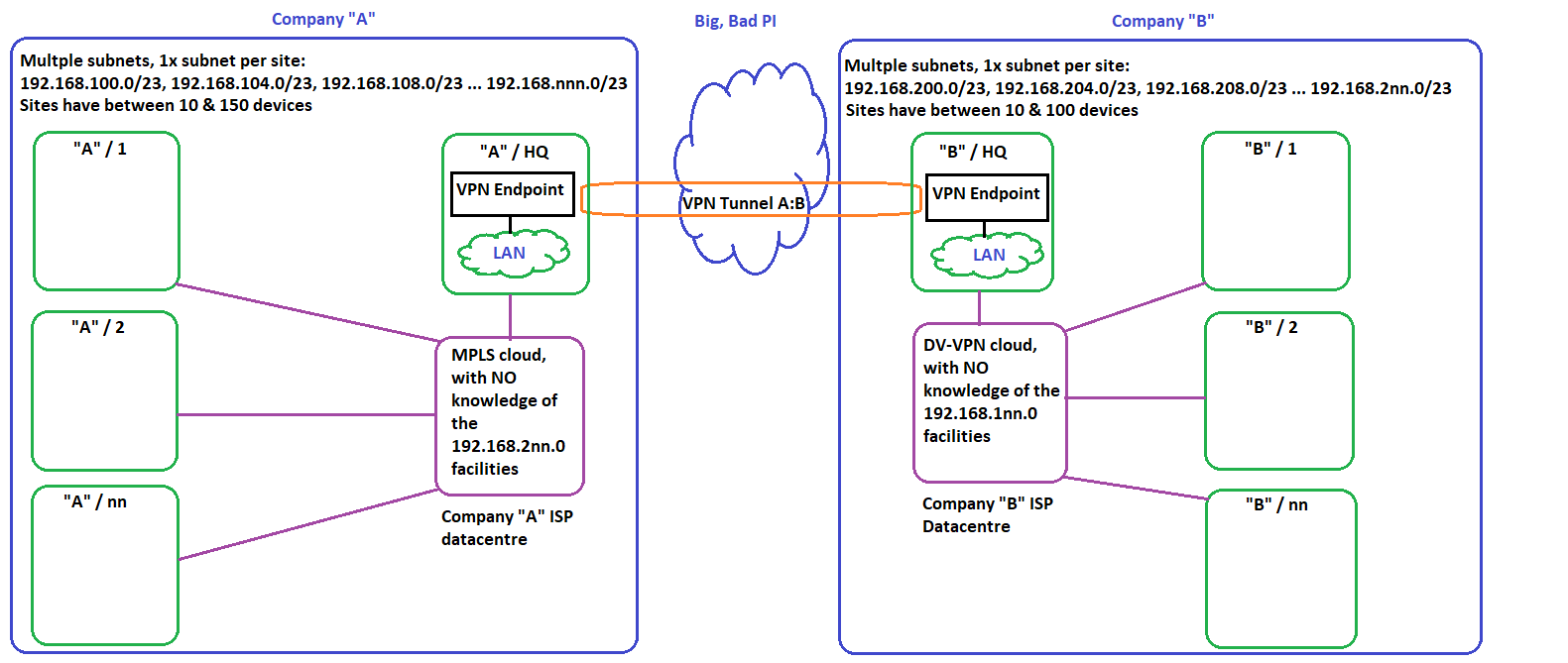
Forgive me if I have put this in the wrong place, wasn't quite sure if it should be: PFSense, OpenVPN, Routing, Bridging, etc.
My business model is currently; business A and business B.
Business A is an MPLS with no in-house L3 or routing change access
Business B is a hybrid star/spoke, Dynamic Virual VPN arrangement, with outsourced L3/routing control ( the third party then outsources the control to another company: A recipe for not getting anything done, or anything remotely approaching what was requested).I have PFSense servers at each HQ with an OVPN successfully running between them and all users at each HQ site can communicate with the HQ at the other end of the link.
This was the model originally proposed and it works great!
"End of story" I hear you say...
Nope: "Project creep" has set in and ALL SITES now need to talk to ALL SITES.There is no way to create a second IP range in either Business, so a standard "LAN/WAN" approach can't be adopted.
I have tried using a single NIC (as firewalling isn't really needed).
I have tried using dual NICs, with a split of the 192.168.n.0/23 thus: 192.168.101.249/28 aliased to WAN & the rest aliased to LANIn my head, both should work, but I suspect I still need an OVPN tunnel to route through.
I have created an OVPN tunnel between A/1 and A/HQ and both ends get an IP, the tunnel shows UP at HQ, but Down at A/1.
I have fully-open firewall rules on all LAN/OVPN interfaces (until I get it working), but as the tunnel is Down/Up, traffic doesn't traverse.I like a challenge, but can't find any help with this.
One more thing.....HELP!
-
What you should be doing is just routing the traffic. That should only require additional routes and rules to pass the traffic. However I gather from your description that is not viable since you don't control the main routers at each site?
Given that A/HQ clients can access B/HQ and vice versa there must be routes present at each HQ site to the other via the pfSense internal IPs. How were those added? What routes are in place exactly?
Adding a VPN between A/1 and A/HQ seems like it would conflict with whatever route already exists between those sites. I assume via the MPLS? Centrally routed somehow?
Steve
-
@stephenw10
Hi and thank you for your response.
Simple routing table mod for the traffic:
e.g.
Source 192.168.1nn.0 , destination 0.0.0.0, Default GW (192.168.1nn.254)
Source 192.168.1nn.0 , destination 192.168.2nn.0, PFS VPN (192.168.1nn.250)
and vice-versa
That's the easy bitAs mentioned; in-house, we have zero control over the routing across the MPLS and the ISP are unhelpful, they would rather sell us other solutions (ah, the joys of outsourcing).
As also mentioned, routing struck me as the easiest way, but without a VPN tunnel between the LAN VPN servers, the "next hop" would be the site Default GW and the traffic would then be lost/quenched in the MPLS.
I had originally though this could work as a single PFS VPN server at each HQ, with a single dedicated PFS server at each sub-site: But as I can't get the the LAN tunnel to go "UP/UP" and transfer traffic, I will now try with a second PFS VPN (LAN only) at HQ and add some simple routing to hand-off to the working PFS VPN server in the Company.
I daren't even suggest buying additional equipment at this stage, due to already having spent a tidy sum on Unifi Dream Machine Pro devices, that couldn't be made to work, even with numerous attempts by Unifi/Ubiquiti technical assistance: This also delayed the project roll-out by over 8 months (they didn't respond very quickly on any occasion).
On the bright side, the fire extinguishers are now available for their intended purpose, rather than propping doors open: The UDMs now do this role :-( -
@rolster said in Routing traffic between remote offices behind respective firewalls:
Simple routing table mod for the traffic:
e.g.
Source 192.168.1nn.0 , destination 0.0.0.0, Default GW (192.168.1nn.254)
Source 192.168.1nn.0 , destination 192.168.2nn.0, PFS VPN (192.168.1nn.250)
and vice-versaAre you applying that to each HQ client directly then? Or at the HQ router?
The MPLS default route at 192.168.1nn.254 is somewhere uncontrollable in the ISPs network?
There's no reason why an OpenVPN tunnel between A/1 and A/HQ should not work. And having that would then allow you to route traffic to the HQ pfSense in order to use the tunnel. You could very easily end up with some asymmetric routing happening though. I imagine currently the subnets at each site are part of the MPLS routed network directly? Does each site actually have a firewall/router?
Adding pfSense at each site and putting all traffic through it would give you far more control over what goes where and prevent asymmetry but may not be practical.Steve