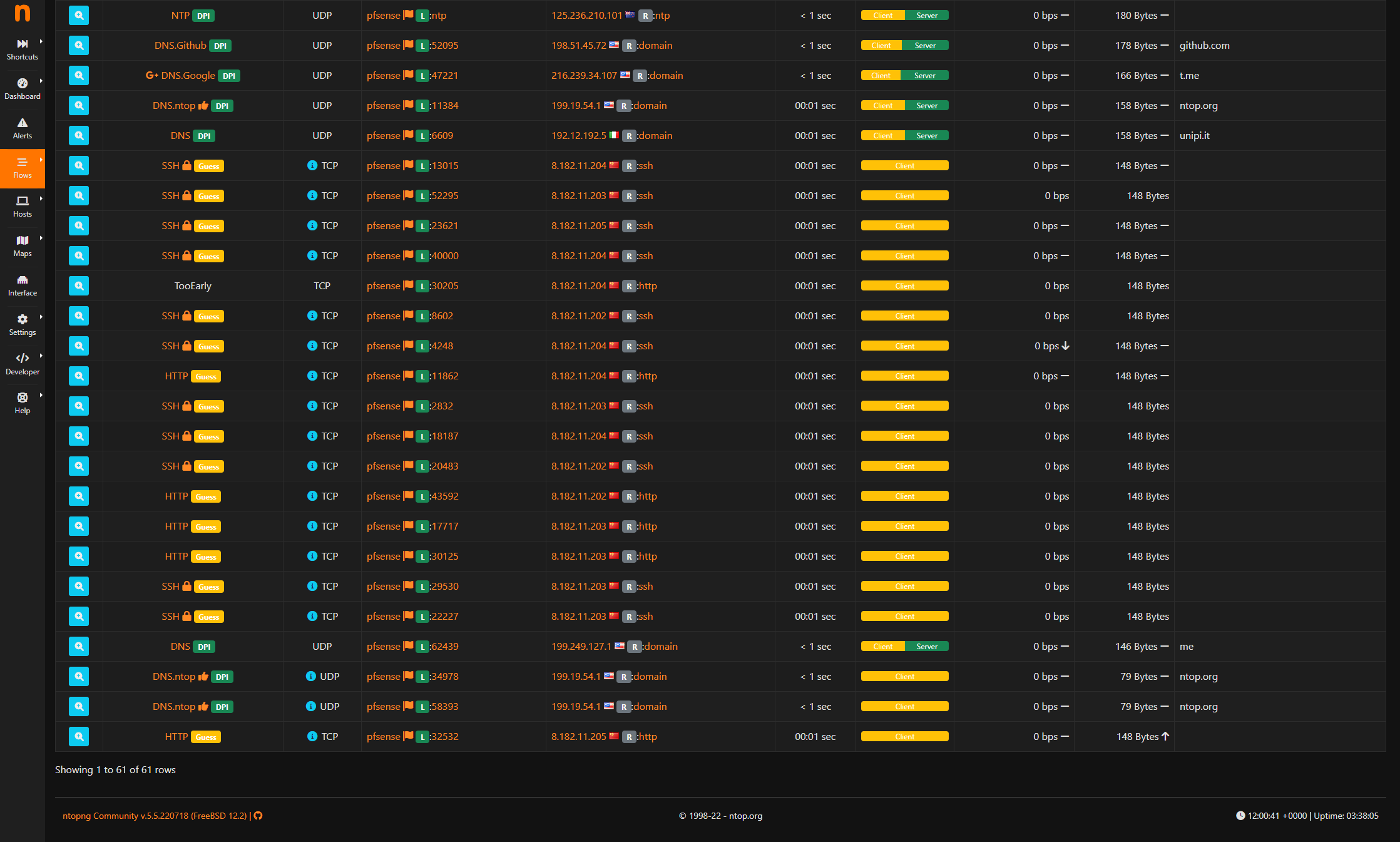
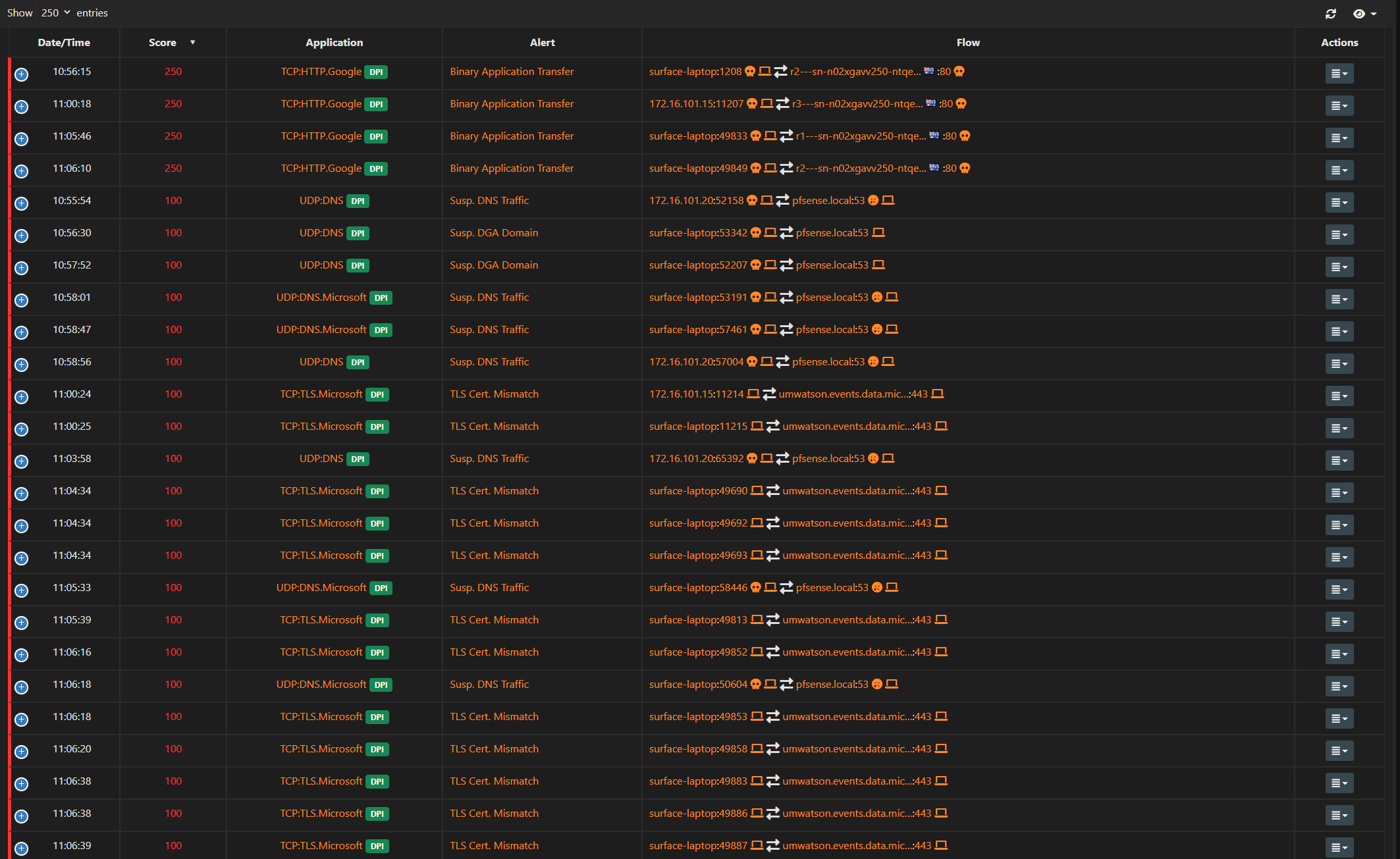
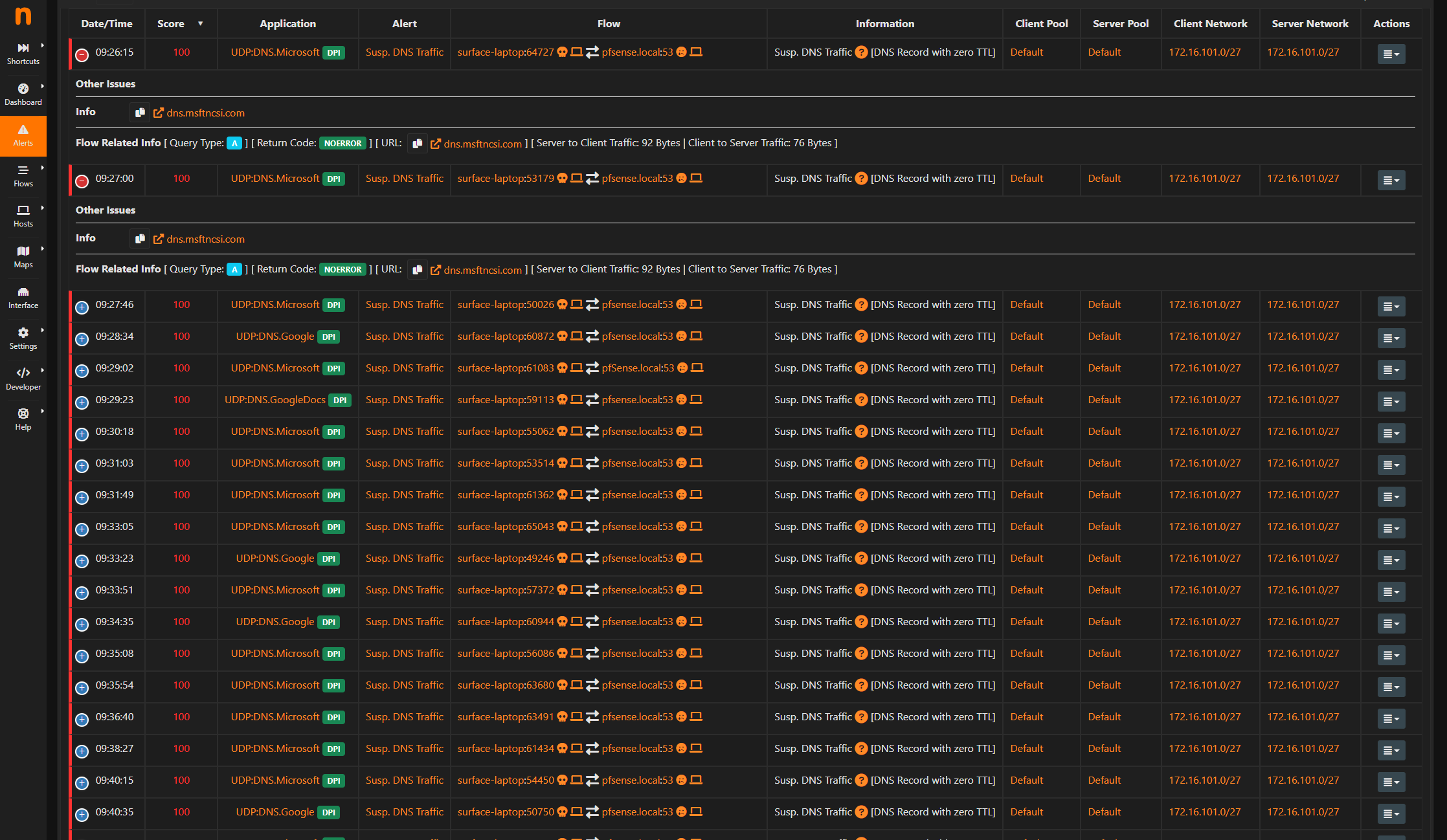
Suspicious Traffic?
-
@johnpoz ok ill go through and disable all my packages one by one
-
@deanfourie see my edit in finding what is creating the connections using sockstat
But I would bet a very large sum of money its ntop.. A very large sum!
-
@johnpoz Yea, you are correct. It is ntop.
But I still dont understand why.
-
@deanfourie because that is what it does with discovery - it finds an IP, and then tries to discover what it is, what os its running, etc.. I showed you the code in the discovery part of ntop where it does a ssh probe.
Here I just turned it on for my wan.. And bam it created ssh to IPs it discoverd..
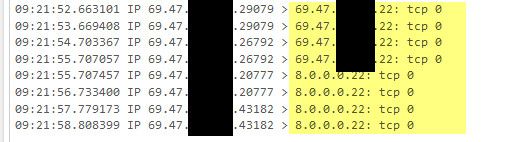
-
@johnpoz Thats so strange, why SSH?
So it only happens with network discovery?
-
@deanfourie because a lot of info can be gleaned from ssh, but it sends other discovery as well mdns, ssdp.. tries port 80 as well I believe.
Even if you can not log in - if ssh answers at all you can get info about that device normally.
Look in the code I linked to for the different discovery stuff it does.
-
-
@deanfourie so for example - here not even logging into one of my pi's and you can glean from just the ssh handshake info about it
debug1: Local version string SSH-2.0-OpenSSH_9.0 debug1: Remote protocol version 2.0, remote software version OpenSSH_7.9p1 Raspbian-10+deb10u2+rpt1 debug1: compat_banner: match: OpenSSH_7.9p1 Raspbian-10+deb10u2+rpt1 pat OpenSSH* compat 0x04000000This is why they normally suggest when you lock down a sshd, that you don't send banners, etc. But this isn't open to the internet and only I use it locally - so no reason to lock it down like its a DoD install ;) heheh
what ports answer, info gleaned from even the answer if anything at all can help "guess" to what the device is or os its running even without specific direct confirmation. So when doing a discovery the more info you can get about a device the more likely it is you can identify it correctly.
Normally when you are running ntop, you wouldn't have discovery going out to the ISP network, only your local internal networks.. You could piss off people with your "probes" if they complain to the ISP you could get yourself in trouble, etc.
-
@johnpoz "You could piss off people with your "probes" if they complain to the ISP you could get yourself in trouble, etc."
LIke port scanning the world.
Ted
-
@tquade to be honest port scanning the "world" could be less troublesome - than an isp customer complaining about another same isp customer
But sure yeah probing the world not normally a good thing ;)
To be honest many an isp should be filtering fellow customers from talking to fellow customers..
But forget getting in trouble or what you should be doing or not being doing to be a good netizen. I make sure no rfc1918 traffic leaks out my wan for sure.. Just doing my part to be a good netizen.. Rarely happens but now and then I typo a address or something.. I make sure that dns for my private domain never goes outbound as well - just no point in sending such traffic that isn't going to resolve..
What would be the point other then pure curiosity knowing that some fellow isp customer has ssh open, or running xyz as their router? What would you even do with that info? I would rather not waste my cpu cycles and bandwidth finding out that info in the first place - and just not send probes out my wan..
Now if he devices on pfsense wan this 192.168.8 network - and he wants to discovery his own devices on that network. Then going to have to look into making sure ntop only discovers 192.168.8/24 and not whatever his real wan is..
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
D denis_ju referenced this topic on