Initiating a WOL when router is behind a VPN?
-
@viragomann said in Initiating a WOL when router is behind a VPN?:
Trying this now... Hit a snag:
This requires a recent pfSense version. Former version are not capable to take a host name here.
I'm currently running "2.6.0-RELEASE (amd64)", and it says it's the latest version. When I try to make the route, it says it needs an IP address or alias. So I created an alias. That seems to have worked, and I was able to create the route.
I released the WAN lease and renewed it. The IP address though might not be right. The modem I have is one of those combo modem/router/switch/wifi things from the ISP. Right now I have one of the LAN ports set as a static IP (192.168.0.50) and is set on a DMZ (so pfSense handles all the ports/etc). So when I was looking at the WAN release page, I saw it listed my WAN IP as that 192.168.0.50, rather than the true WAN IP. Will that be a problem? --- I just checked the No-IP website and it indicated the correct IP (but I did go in and manually specify that a few days ago before disabling pfSense's updater. I'll monitor this and report back.
-
@hansolo77
Ah, there is a router in front of it. Basically it should word with that as well. But pfSense has to request the public WAN using an external IP check service.By default pfSense uses http://checkip.dyndns.org
It's set in Services > Dynamic DNS> Check IP Services.So your problem might be, that the IP checks goes out to the VPN. So you can route checkip.dyndns.org to the WAN gateway in the same way to resolve this.
-
@viragomann Makes sense.. I'm going to keep monitoring it and see what happens. At least I kind of have an idea of what to do. Thanks for your help!
-
Well, I give up (again). I have the whole "report the correct IP address" working. I've watched it a few days, and it is still reporting out the same IP address. So I think I'm good there. Now my problem is getting the WOL function to work. I've tried everything. When I'm initiating the command from my tablet to the computer when on the same network, it works fine. But when I send the command from my tablet to the computer when I'm on a different network (bluetooth tethered to my cell phone's hotspot, using celluar), it doesn't work.
Don't get me wrong. I know all about how I need to use the DDNS instead of the computer's IP address. It all worked brilliantly before I started using pfSense. I have my WOL program configured with 2 entries. One is "local" using the IP address (10.27.27.200) and port (9), and the specific MAC address. The other is "remote" using the DDNS "kyber.ddns.net" and the same port and MAC. Local works, Remote doesn't. Even when I'm using the same network, I can't get the remote WOL to work.
To get where I'm at, I've already tried various things. I have the modem, which is configured to put my pfSense on DMZ already, doing it's own port forwarding for the WOL packet. I have it pointing that all port 9 requests go to the pfSense router. This shouldn't matter because of the DMZ, but I tried it anyway. On the pfSense side, I have the computer set up using a static IP (obviously). Then I have the NAT rules set to forward all port 9 requests to the IP address of the computer. Didn't work. I even moved that rule to the top. No dice. I also know that this works using UDP, but I set it to TCP/UDP as a test just in case, didn't matter. The only thing I can make work is the pfSense's built in WOL system. That's good enough for now, but I'd love to make this work without having to VPN into my network to initiate the wake.
I don't know if this problem is because of the IPVanish VPN that's running on the router, or if it's something else. All I DO know is that it's not working lol.
As an aside... I noticed that when I enabled the WOL widget on the pfSense homepage, I can trigger the command easily enough. But the icon that indicates the computer is up or down never changes from down. I tried to read a bit about how pfSense verifies a computer is up, and apparently it does it via pings but Windows 10 blocks pings. So I looked up how to fix that, and it should be working now, as I can ping it from another computer. Is the widget broken when it comes to showing up/down or am I missing something else?
-
@hansolo77 said in Initiating a WOL when router is behind a VPN?:
but Windows 10 blocks pings
It does so if it is using a network that it is considering as 'public".
Make the "Private"and W10 answers to ping.Or, as usual : add or change a ICMP firewall rule
-
@gertjan said in Initiating a WOL when router is behind a VPN?:
Or, as usual : add or change a ICMP firewall rule
I'm so newb I don't even know what ICMP is.. so I think it's safer to just leave it alone. I'll check that Private answers to ping too.
-
@hansolo77 said in Initiating a WOL when router is behind a VPN?:
I'll make it easy for you. The answer is one click away

-
@gertjan That's incredibly unhelpful. :( I mean, OK, it's a protocol. Why would the suggestion be that I have to add or change an ICMP firewall rule, if this "verify a PC is on" function is built into pfSense already? I don't understand. If there is some other step I have to do, ON the firewall, to make a function ON the firewall work, that just doesn't make any sense. Sure, if I had to do something on the PC, that's different. Sorry I'm so lost.
-
@hansolo77 said in Initiating a WOL when router is behind a VPN?:
That's incredibly unhelpful
I get it.
I was just helping you with : "I don't even know what ICMP.Consider :
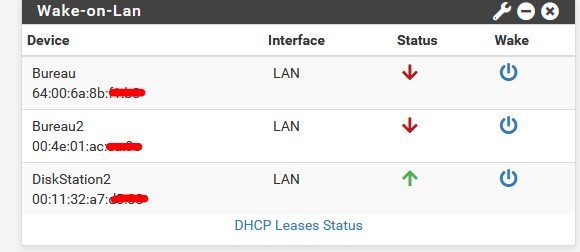
How does the widget knows the device is off line ?
Because it doesn't reply on pings = ICMP echo request packets.@hansolo77 said in Initiating a WOL when router is behind a VPN?:
Is the widget broken when it comes to showing up/down or am I missing something else?
Most probably not, as in that case you should see many posts here on this forum with the same observation.
If the widget says : "down" then the ping requests send to your device doesn't come back with an answer because it doesn't want / can't answer, or it is off line.You should check the firewall of the Windows PC if it is enabled to reply on pings.
@hansolo77 said in Initiating a WOL when router is behind a VPN?:
but Windows 10 blocks pings
This is not a standard behaviour at all : you changed the network settings of that PC, like adding software that changes its firewall ?
If you can not pint that PC using pfSense > Diagnostics > Ping then your issue is with that PC.
I presume you do not have a router between pfSense and that PC, just a cable or a switch.
-
This post is deleted! -
@gertjan
I think I might have fixed the problem. At first, I had a suspicion that it might be because the network connection is complicated. This PC has 2 connections.. one is a 10gb NIC, the other is the motherboard's onboard 1gb. The 10gb doesn't allow WOL, so I also enabled the 1gb specifically for the WOL. I've had some trouble with the 1gb, in that Windows doesn't like it when I have both NICs using the same gateway. So I thought maybe that might have been the problem. When I got home today, I decided I would experiment with that to see if I could make it work. Before doing anything, I also decided to "start fresh" by rebooting all the systems, PC's, modem, router. Surprisingly, I think rebooting the pfSense router was all I had to do. The widget now shows the PC in question is UP. I will monitor this and see if it correctly reports DOWN when I get home from work tomorrow, and UP again when I wake it.
Lol, guess I was wrong. Now it's stuck saying it's on all the time. ^_^ Why can't I be smarter than this. :(
Going back to my original theory.. I think it's the way my 1gb network is setup. I can ping it from a command prompt on another computer. But if I use the the Ping from pfSense, it gives me 100% loss. If I ping the 10gb network, it comes back with 0% loss, and works with command prompt too. So the question now becomes, what's different between the 2 connections? Besides the IP address, they pretty much match EXCEPT for the fact that I have to leave the "Default Gateway" blank or Windows complains. If that's a requirement, I don't know how to get around it.
Here is the breakdown of my network connections. 10g is an SFP+ Addon NIC running cat6 to the pfSense. 1g is on motherboard running cat5 to the pfSense. The 3rd NIC is setup but nothing is connected and it's disabled. They are using only IPv4 not IPv6. Also, this is after I tried putting a gateway address into the 1G.
Name: 10G Description: Mellanox ConnectX-3 Ethernet Adapter Physical address (MAC): *REMOVED* Status: Operational Maximum transmission unit: 1500 Link speed (Receive/Transmit): 10/10 (Gbps) DHCP enabled: No IPv4 address: 10.27.27.202/24 Default gateway: 10.27.27.1 DNS servers: 10.27.27.1, 8.8.8.8 Network name: Network Network category: Public Connectivity (IPv4/IPv6): Connected to Internet / Connected to unknown network Name: 1G - Left Description: Intel(R) I211 Gigabit Network Connection Physical address (MAC): *REMOVED* Status: Operational Maximum transmission unit: 1500 Link speed (Receive/Transmit): 1000/1000 (Mbps) DHCP enabled: No IPv4 address: 10.27.27.220/24 Default gateway: 10.27.27.1 DNS servers: 10.27.27.1, 8.8.8.8 Network name: Network Network category: Public Connectivity (IPv4/IPv6): Connected to local network / Connected to unknown network Name: 1G - Right Description: Intel(R) Ethernet Connection (2) I219-V Physical address (MAC): *REMOVED* Status: Not operational Maximum transmission unit: 1500 IPv4 address: 169.254.254.13/16 Connectivity (IPv4/IPv6): Disconnected -
@hansolo77
Yeah, two gateways won't work well at all. But when you remove the gateway, you cannot communicate with the NIC from outside the subnet.
As a workaround you can masquerade the packets going to 10.27.27.220 by adding an outbound NAT rule on pfSense. -
@viragomann said in Initiating a WOL when router is behind a VPN?:
@hansolo77
Yeah, two gateways won't work well at all. But when you remove the gateway, you cannot communicate with the NIC from outside the subnet.
As a workaround you can masquerade the packets going to 10.27.27.220 by adding an outbound NAT rule on pfSense.Attempted to do that, but probably didn't do it right (it didn't work). This is what I made:
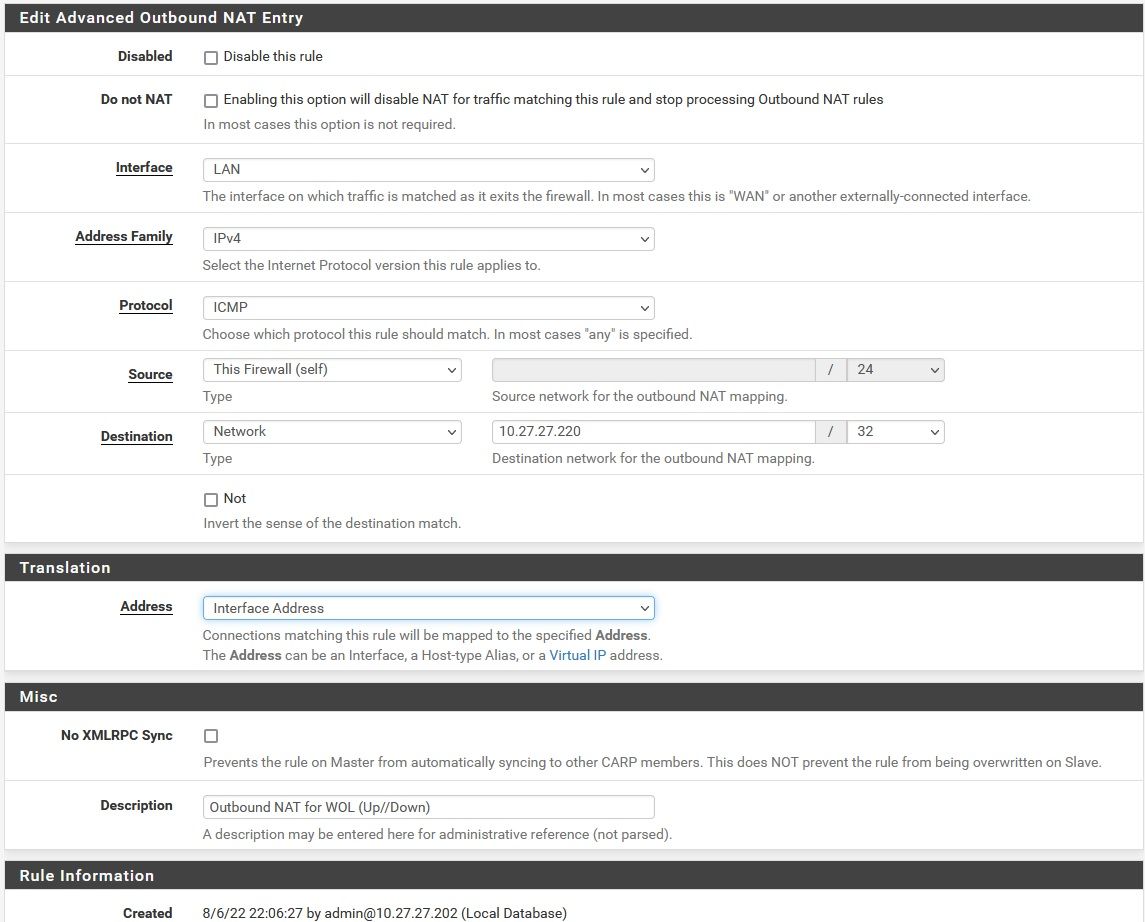
-
@hansolo77
The source has to match the origin source address of the packets. If it’s unknown or a dynamic public address select „any“.
„This firewall“ will make no sense at all. If pfSense itself talks to the device it uses the interface IP anyway.The protocol has to match to the communication as well. ICMP is for pongs, but not for WOL.
Also consider to set the outbound NAT to hybrid mode to have the rule take effect.
-
@viragomann
I see. This is all still ridiculously new to me. I will make adjustments.
Yeah still not working. I'm about to give up on this.