IKEV1 Site to Site VPN - Cannot ping Remote Lan
-
Hi
i configured site to site VPN with ASA Cisco Firewall. Tunnel is created and connected. But not able to ping LAN side of remote firewall.
i also check post related to this but not fond the solutions.TCPDUM
[2.6.0-RELEASE][admin@pfSense.home.arpa]/root: tcpdump -i vtnet0 host 209.150.154.66
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on vtnet0, link-type EN10MB (Ethernet), capture size 262144 bytes
10:55:17.037625 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:55:17.038352 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:55:27.037675 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:55:27.038596 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:55:37.036752 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:55:37.037134 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:55:47.036759 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:55:47.037848 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:55:57.036351 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:55:57.037630 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:56:07.036155 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:56:07.037115 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:56:17.036014 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:56:17.036821 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:56:24.746466 IP static.247.28.216.95.clients.your-server.de > 209.150.154.66: ESP(spi=0xb1a453c1,seq=0xa9), length 132
10:56:24.924339 IP 209.150.154.66 > static.247.28.216.95.clients.your-server.de: ESP(spi=0xc69126e4,seq=0xa9), length 132
10:56:25.752597 IP static.247.28.216.95.clients.your-server.de > 209.150.154.66: ESP(spi=0xb1a453c1,seq=0xaa), length 132
10:56:25.934947 IP 209.150.154.66 > static.247.28.216.95.clients.your-server.de: ESP(spi=0xc69126e4,seq=0xaa), length 132
10:56:26.756420 IP static.247.28.216.95.clients.your-server.de > 209.150.154.66: ESP(spi=0xb1a453c1,seq=0xab), length 132
10:56:26.933789 IP 209.150.154.66 > static.247.28.216.95.clients.your-server.de: ESP(spi=0xc69126e4,seq=0xab), length 132
10:56:26.935119 IP static.247.28.216.95.clients.your-server.de > 209.150.154.66: ESP(spi=0xb1a453c1,seq=0xac), length 132
10:56:27.112269 IP 209.150.154.66 > static.247.28.216.95.clients.your-server.de: ESP(spi=0xc69126e4,seq=0xac), length 132
10:56:37.034736 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:56:37.035141 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]
10:56:47.035888 IP 209.150.154.66.isakmp > static.247.28.216.95.clients.your-server.de.isakmp: isakmp: phase 2/others ? inf[E]
10:56:47.036950 IP static.247.28.216.95.clients.your-server.de.isakmp > 209.150.154.66.isakmp: isakmp: phase 2/others ? inf[E]Pfsense Firewall
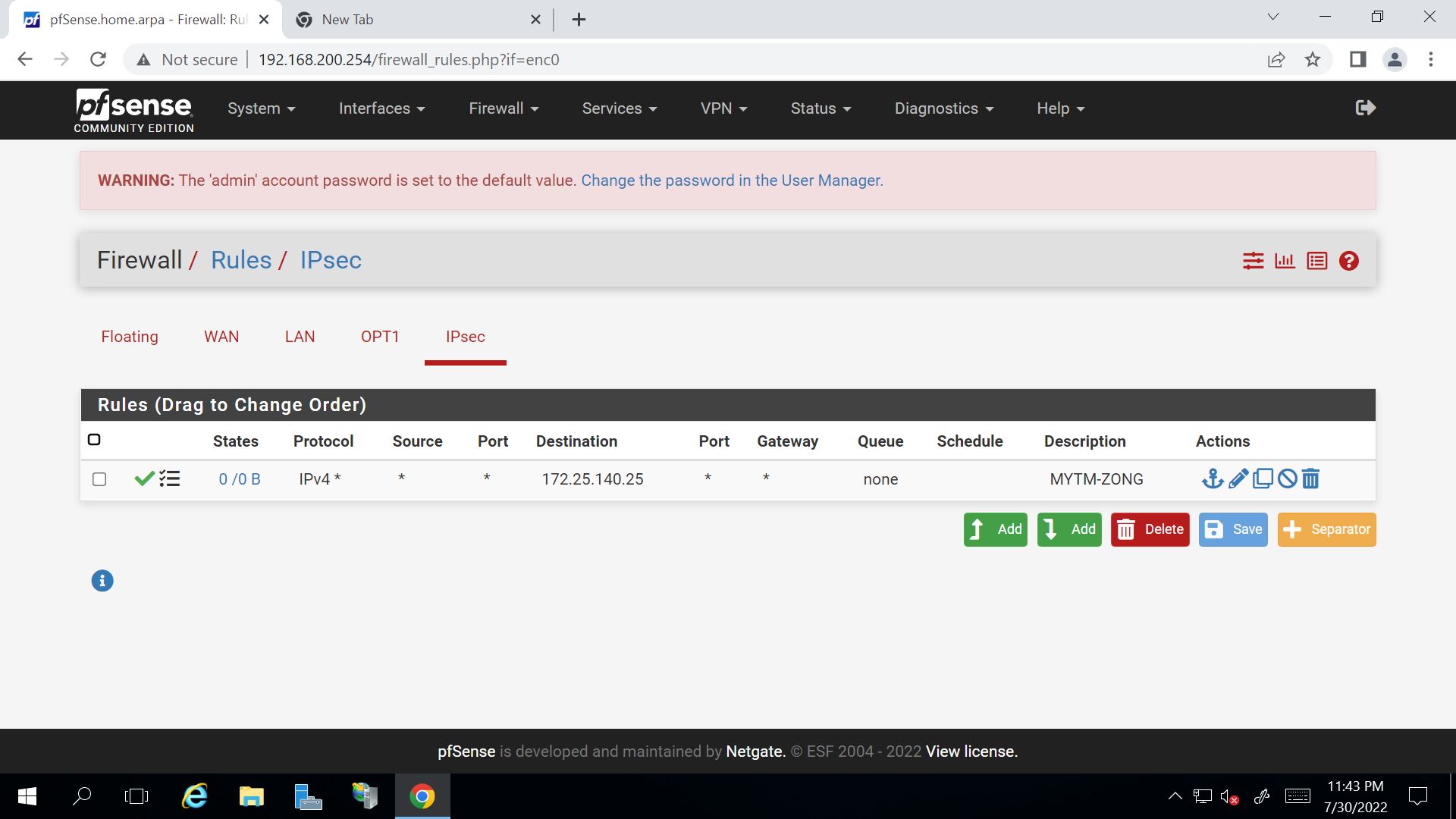
IPSEC Status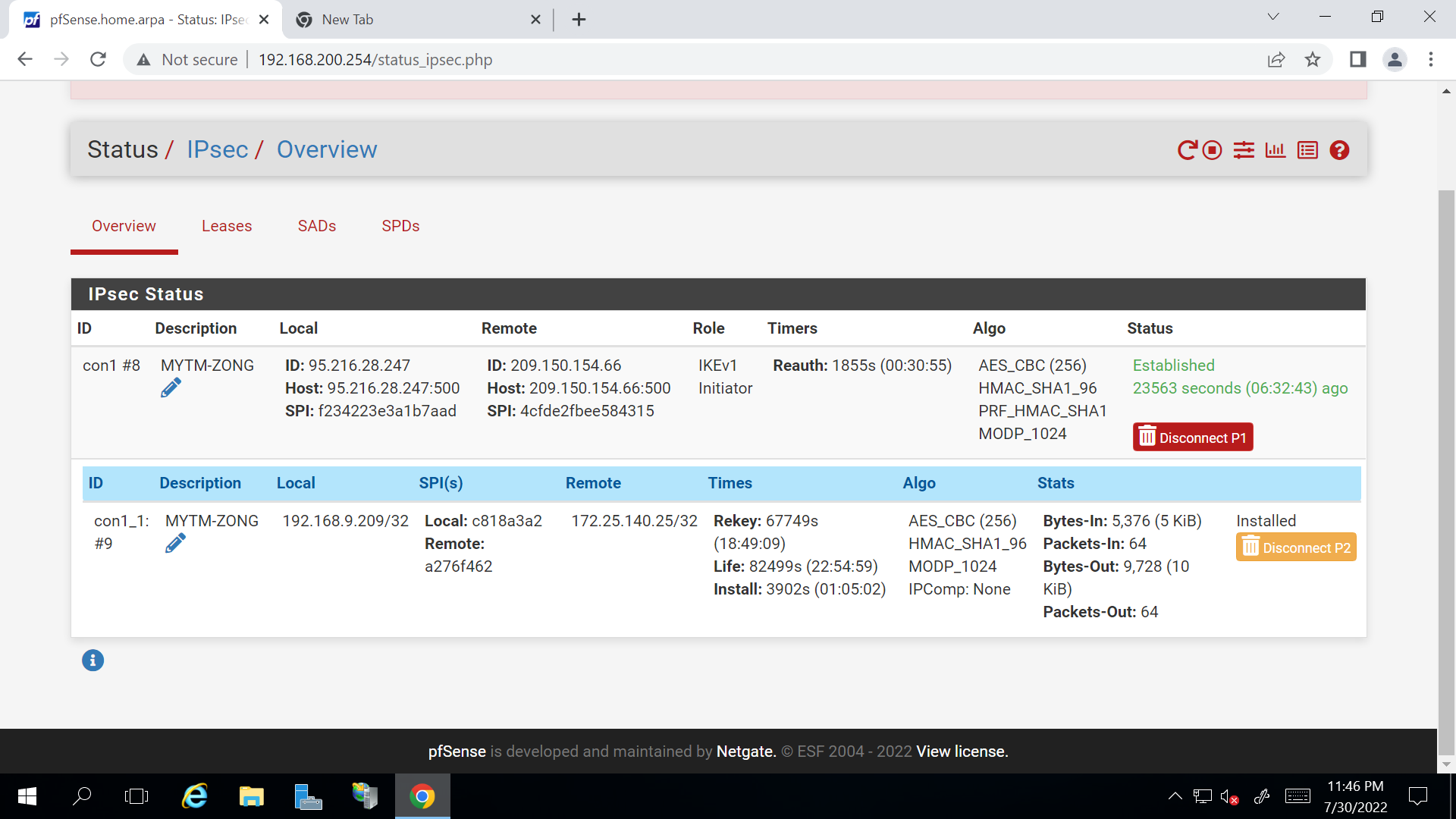
-
@shahidge4
The tcpdump from WAN is pretty useless, since the connection is established already.Your P2 has a single remote IP. So the VPN will only allow access to this one.
Do a packet capture on the IPSec interface.Ensure that the remote host does not block access from the remote network.