SCTP and NAT not logging
-
Hi,
On a pfsense 2.6.0 we configure :
- a NAT 1:1 from external IP to internal server.
- a FW rule on WAN to allow traffic from "all" to "sctp_LAN" on SCTP
- a FW rule on "sctp_LAN" to allow traffic from *sctp_LAN" on SCTP
- activate logging on both.
User can't connect via sctp, and i don't see anything in logs when filtering on SCTP protocol only, or on the user"s external IP (with all protocols).
I test to add * to * / * rules with logging, i can see a ssh or random tcp traffic, but the sctp don't go and nothing in logs.
Is there something special to configure to have sctp events ?
Thx
David -
Let's see some screenshots of the 1:1 NAT and firewall rules/
to "sctp_LAN"seems probably wrong though. The destination there should be the internal server.Steve
-
@stephenw10
yes i admit that with the NAT, i'm not sure of which rules i need and on which LAN
In the doubt i activate both.-
NAT
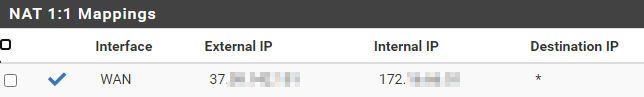
-
FW Rules on WAN
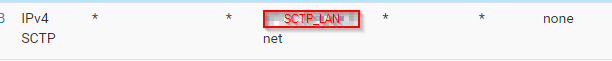
(sorry i change the name to go with the description) -
FW Rules on SCTP_LAN
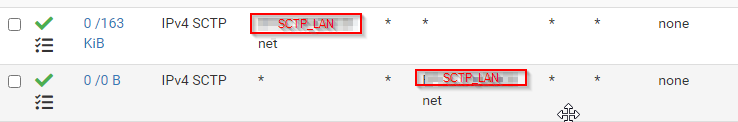
Ha and SCTP_LAN is the subnet with internal IP of the server
-
-
I try to get logs with a minimal filtering :
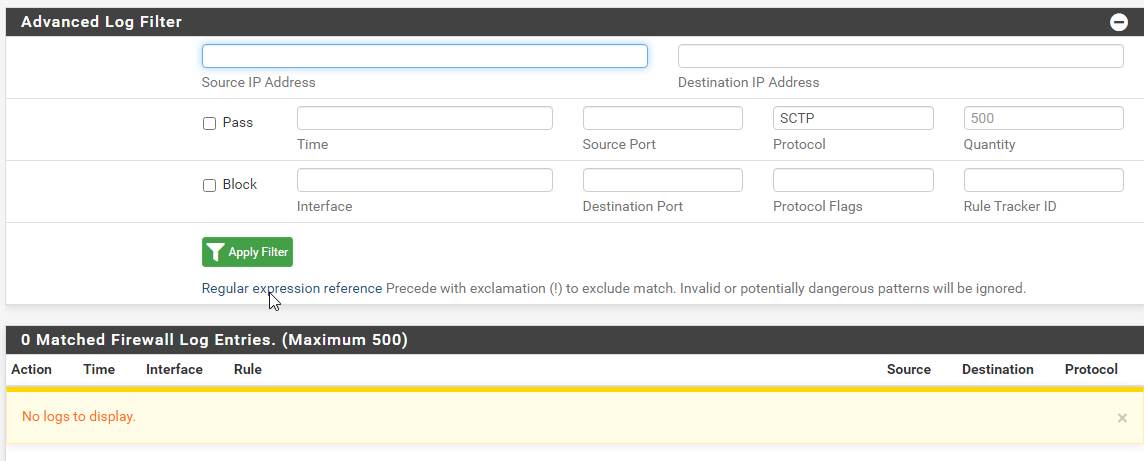
Another note : we have the same flow working but via an internal VPN/IPsec and the same king of rule, but in IpSec tab.
-
The WAN destination rule should probably be the internal 172 IP. But that rule using the entire subnet should also match and pass it.
You don't need any rules on the internal interface to allow connections in from the internet.
The second rule you have there with destination SCTP_LAN net can never match anything. Traffic with that destination would just go directly between hosts and never hit the firewall.Run a packet capture on WAN. Make sure you are seeing SCTP traffic arrive and with the expected destination IP.
Steve
-
@stephenw10
Yes i'll do this tomorrow.
But was thinking that it should be visible in the logs like others ?
Or something that prevent SCTP packet to be logged ? -
It should be logged there if you have logging enabled on the pass rule(s) and any states have been opened.
It may have left the logs already if you have a very busy WAN.