SSH without passwords
-
My end goal is to set up a wireshark trace to debug some issues I am having with a new wifi based card. I saw a post that suggests I can do that by running tcpdump on pfSense and piping that to my PC running wireshark by running ssh. This requires I set up a key with keygen without a passphrase, which I've done before on other *NIX systems.
So I generate the keypair on my PC without the passphrase using openssh on Cygwin. This creates the key pair file id_rsa.pub. I've checked and this file is what ssh is using to authenticate with.
I then copied the public key into my pfSense system for that user.
When I attempt to ssh into the pfSense system it recognizes the user, but still asks for a password. If I specify the password I log in, so it's not the user part of the credentials.
The ssh command shows that the pfSense server is apparently rejecting the certificate. Debug output shows:
debug1: Offering public key: /home/Wayne.Johnson/.ssh/id_rsa RSA SHA256:dHQKYenNbkrL/hvhJ7822kfXpujVsScNsF5yfmPnCsA debug3: send packet: type 50 debug2: we sent a publickey packet, wait for reply debug3: receive packet: type 51 debug1: Authentications that can continue: publickey,password,keyboard-interactiveSo for some reason the sshd server on pfSense has rejected the publickey. I've been digging for a sshd server log but not finding anything is /var/log.
Questions:
Is there some restrictions on passphrass less logins in pfSense?
Where is the sshd config stashed?
Is there a sshd log?
What am I missing here? -
How did you add the key to pfSense?
Nothing special is required there as long as the user you added it to has privileges to login via ssh at all. I assume you can login using the password?
Steve
-
@wdtj if your goal is to just do a sniff on some pfsense interface - why not just use the built in packet capture under diagnostic menu - and then you can download it and view it in wireshark for example.
I prob do this 3 or 4 times a week.
edit: but I log into pfsense using public key, pretty much every day - normally multiple times a day
debug1: Offering public key: /home/johnpoz/.ssh/id_ed25519 ED25519 SHA256:y1pJFKtYk+f2IP<snipped> debug1: Server accepts key: /home/johnpoz/.ssh/id_ed25519 ED25519 SHA256:y1pJFKtYk+f2IPWai<snipped> Authenticated to sg4860 ([192.168.9.253]:22) using "publickey". -
I did do a Linux Wireshark "pfSense Remote sniffing" as a proof of concept, back in the pfSense 4.3.?? days
Ref:
https://www.cyberciti.biz/faq/how-to-add-delete-grant-sudo-privileges-to-users-on-freebsd-unix-server/on pfsense install pkg install security/sudo 1: visudo , add : %admins ALL=(ALL) NOPASSWD: ALL 2: vi /etc/groups , make sure your user is member of admins. As root on local linux machine 3: ssh-keygen 4: ssh-copy-id user@firewall As root on local linux machine - -i specifies the interface to tcpdump ssh user@firewall sudo tcpdump -iigb1_vlan100 -U -s0 -w - 'not port 22' | wireshark -k -i -It was fun to do , but i usually just do as @johnpoz mentions.
Local sniff , and DL + See capture in wireshark/Bingo
-
@johnpoz Yea. I just discovered that.
-
@wdtj OK, so the trace question is answered, but it still bugs me that the passphrase less ssh does not work.
I have a user defined via the GUI, it is a member of the admins group, and I did copy my public key to the "Authorized SSH Keys" for that user.
Since I can access with the password, this would mean (in my experience) that the server had an issue with the public key or it's file. Normally this is due to the file not having mode 600. Apparently this file is not in the users's .ssh directory on pfSense. Even if I try creating that file, it still does not work.
Normally I would look at the sshd log to diagnose this sort of issue, where is that on pfSense?
-
@wdtj not sure what your doing exactly.. But I just created a testuser.. put them in admin group.
Added their openssh public key I created in the gui.
and bam login in just fine with public key
And you can see that public key got added in their directory.

you can see in the auth log where it was accepted
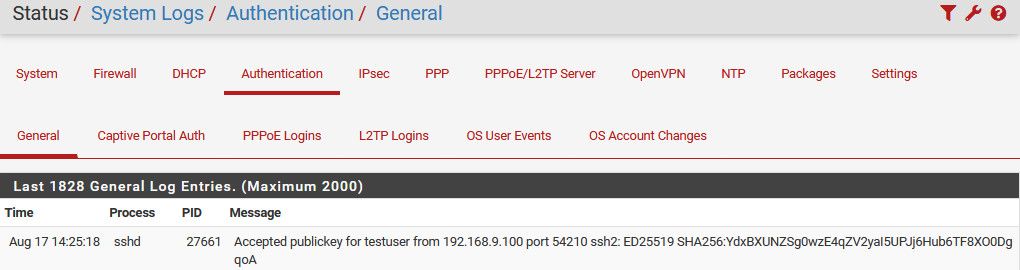
-
The SSH daemon logs to
/var/log/system.logon pfSense software, so look there for errors.Make sure what you pasted into the authorized keys is the full public key:
% cat .ssh/id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCpnbNaB/Ffpwg6B61Sp9fU/Y5y4pHITTZ8gEDR8dakS5uqI7HbkoXxO+vwRoJZ4/RPEVfGa22cp5KKOdzXdJpJyFqWNK2u228yBCNATATHSNoYOvwxvk3zsTESR6V0B/j8uT+tjJBKOcEd8rq0NLOLsw4bsGIwQQ6pvvIpAyrDCBczZj8yY8bvhwTupJl/OjYLAVU8iqTII9CHPygTlFe0TswMUyjyvFYVgvwP9yY5JYICMAES4tK1tplvA1WWxSYx96xXov9Df5VYKLxWaOyUL7MsXNHErlDqe7PZ6BIkVSCDw39Za8+p92W9IvlhJ/Blbv7odc04nOiZK0Vk9HktTSE4WzElcKzzURhgv6KNVn6E876S25HUHD7iiUGK/zC4lG5/1igpfZ6m8eVhzuW68Feor4A/6SIZRjcDyBp1s7vg9c+b/dnCcYqDc5zhQ7LOQGhNrz8rO41NafRy3tpCtFdHcQZG5hDLOagbHiSo8E3aYaQpj7UGJUH3z9JYU0k= jimp@fbsd-currentYou copy in that whole block from
ssh-rsaand include the comment at the end. The result must be on a SINGLE line if you copy/paste out of the cygwin terminal it may insert line breaks where it wraps lines so you will have to reassemble it into a single line. I suggest copying and pasting into an editor such as Notepad++ on Windows, or even open up theid_rsa.pubfile directly in Notepad++.Also if you are stuck running Windows on there, consider switching away from Cygwin to using WSL2/Ubuntu integration and Windows Terminal (free in the MS Store). It's a lot easier to work with over time than Cygwin, IMO.
-
@johnpoz I just copied the public key over again, and tried to log in. Still getting the same request for password. The log took a while to update but this is what it contains:
Aug 18 09:09:45 sshd 90095 error: PAM: Authentication error for waynej from 192.168.2.77 Aug 18 09:09:45 sshguard 54822 Attack from "192.168.2.77" on service SSH with danger 10. Aug 18 09:09:49 sshd 90095 Accepted keyboard-interactive/pam for waynej from 192.168.2.77 port 64218 ssh2First like appears to be from my cert. Second is accepting the password and letting me in.
Since my requirement for passwordless entry in now gone, I';ll just drop the problem. Thanks for your help.
-
@jimp I am aware of the problems with some editors inserting newlines in a copied block and I did check for that. The GUI window makes this difficult because it also wraps the line which looks like a newline was inserted. I tried deleting the wrap points (which ends up deleting the character before the wrap) but everything is on one line.
It would be nice to know where this key is stored so that it can be verified without all the GUI decorations (wrappings).
Since my requirement for passwordless entry in now gone, I';ll just drop the problem. Thanks for your help.
-
@wdtj might be stupid question but you don't have it set to require both do you?
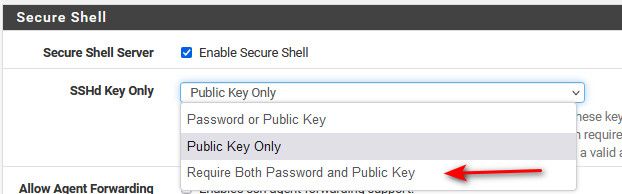
Where/what are you creating the key pair with?
What client are you trying to access with, with ssh you can up the verbosity and might get some clue to what is going on -vvv vs just -v in the openssh client for example.
-
The file is in /home/username/.ssh
Verify the user owns the .ssh directory and the authorized_keys file within. -
@dotdash I hear yeah and is a valid check - just curious how that would get borked, if he just used the gui. Now if he manually was editing those files sure.
-
The PAM error is usually from it just not matching the key. Either because the correct key isn't present, or what's in the file isn't valid.
The keys are on disk on the firewall in the expected location for a user, if you login with a password they would be in
~/.ssh/authorized_keys. If you login as admin or root, then use~<username>/.ssh/authorized_keys, or look under/home/<username>/.ssh/authorized_keys.The firewall will manage the content of that file and its permissions so those are not likely to be concerns.
These issues almost always boil down to a problem with the formatting of the key, either line breaks in the key, extraneous whitespace, or the wrong string pasted in (For example we've seen people paste in the fingerprint, not the public key)
There is also a slight chance that
ssh-keygenin Cygwin is generating a bad key somehow. Using a more modern format likessh-keygen -t ed25519may help instead of using RSA format.