Pfsense sees NATted networks behind UDM-PRO
-
Hi, first of all i would like to thank you for that great product and i appreciate your efforts keeping it free and up to date.
I'm using Pfsense Firewall as my main firewall for internal users' internet access. I'm also using 2 UDM Pro wireless controllers in my network environment for wireless users.
Wireless users' networks are actually behind the UDM pro wan ip which means it gets NATted by UDM Pro and Pfsense should only can see UDM Pro wan ip. Both of UDM pros are using static ips that are part of Pfsense network (vlan) for NATting UDM pro's internal networks.
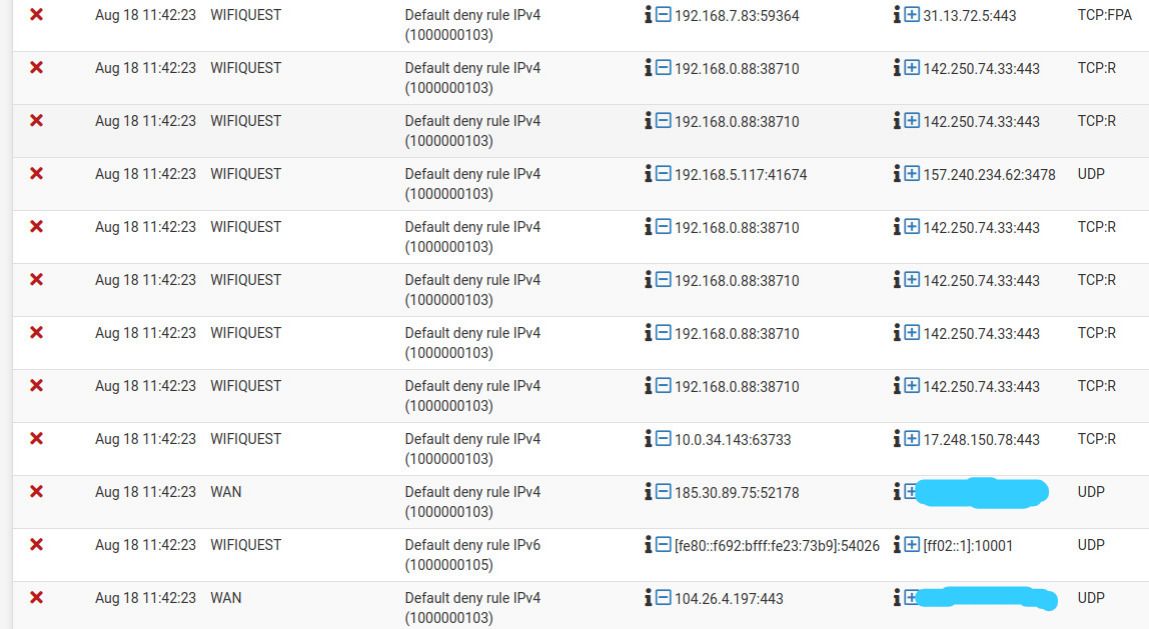
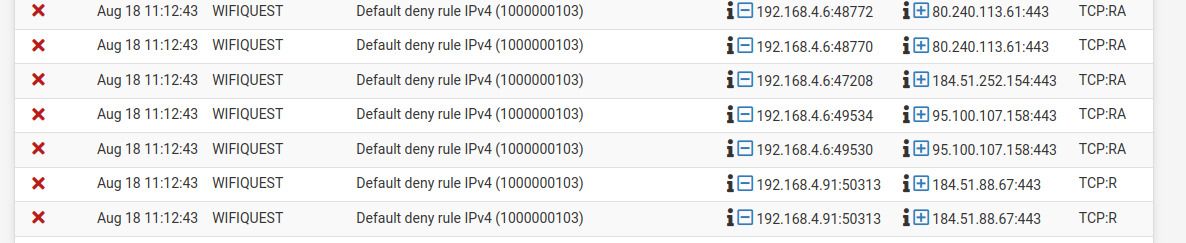
But when i look at the Pfsense firewall logs i see constant logs about UDM pro internal networks getting dropped by firewall with TCP:FPA, TCP:FA, TCP:R, TCP:RA flags.
The thing i don't understand is how Pfsense firewall sees UDM pro internal networks, how networks behind NAT can send packets directly to the firewall? And if so, how can i know which firewall interface receives that type of packets.
Overall, packet drops are not noticed by users but i know that something is not normal with my network. And i want eliminate the risks of my network being out of service because of unknown issues.
-
@gmhmaster said in Pfsense sees NATted networks behind UDM-PRO:
getting dropped by firewall with TCP:FPA, TCP:FA, TCP:R, TCP:RA flags.
Those are all out of state drops.
Screams asymmetrical. There should be no way for pfsense to see those packets if your network was correctly setup.
So either your networks not isolated like you think you are, or your udms are sending that traffic on without natting it.
-
What type of misconfiguration can cause these issues? I'm actually quite doubtful about my network, because on some parts of network we are using hubs (unmanaged switches). Can improper isolation of vlans be the cause of problem ?