Any issue in changing the pfsense hostname?
-
Hello,
is it possible to change the Pfsense hostname without weird consequences?
Generally, I'd do it from /etc/hosts and then reboot to be safe. -
@jt40 you mean away from pfsense, mine is called sg4860 - yes it was a very creative in coming up with that name ;) since that is what it is.
Just change it here
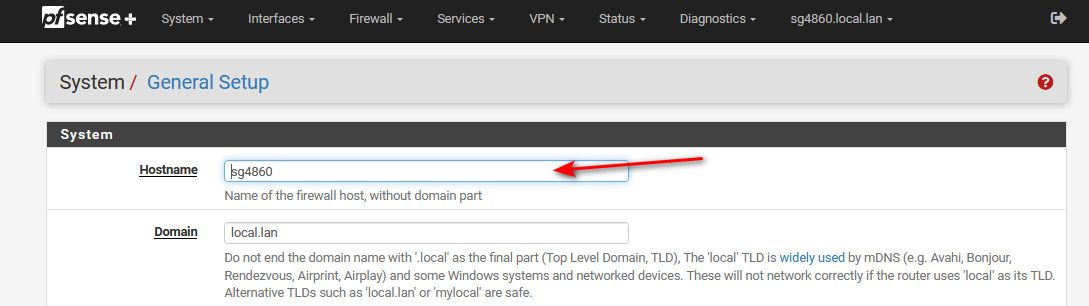
The only hiccup you might have is any bookmarks or such in your browser pointing to pfsense.domain.tld or not sure about the https cert, you might want to regen that if you access pfsense gui via fqdn. Not sure if that would get auto updated when you change it?
or if you are using your own cert for the gui vs self signed one that pfsense generates on its own.
I have a cert via CA created on pfsense that has the IP and sg4860 as SAN, so if I was going to change it I would want to gen a new cert with the new fqdn in it, etc.
-
@johnpoz said in Any issue in changing the pfsense hostname?:
@jt40 you mean away from pfsense, mine is called sg4860 - yes it was a very creative in coming up with that name ;) since that is what it is.
Just change it here

The only hiccup you might have is any bookmarks or such in your browser pointing to pfsense.domain.tld or not sure about the https cert, you might want to regen that if you access pfsense gui via fqdn. Not sure if that would get auto updated when you change it?
or if you are using your own cert for the gui vs self signed one that pfsense generates on its own.
I have a cert via CA created on pfsense that has the IP and sg4860 as SAN, so if I was going to change it I would want to gen a new cert with the new fqdn in it, etc.
LOL, I didn't notice that, awesome.
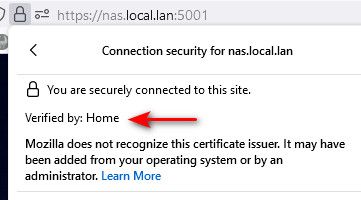
Regarding the cert, I'm using the default one, what kind of cert Pfsense expects?
In any case, it would be always a self signed cert, my browser will always complain about it, I don't think I can avoid it unless having a separate infra for such things, like Windows Server or any open source solution. (btw, do you know any? :D ) -
@jt40 just create a CA in pfsense, then create a cert with that CA and have your browser(s) trust that CA.
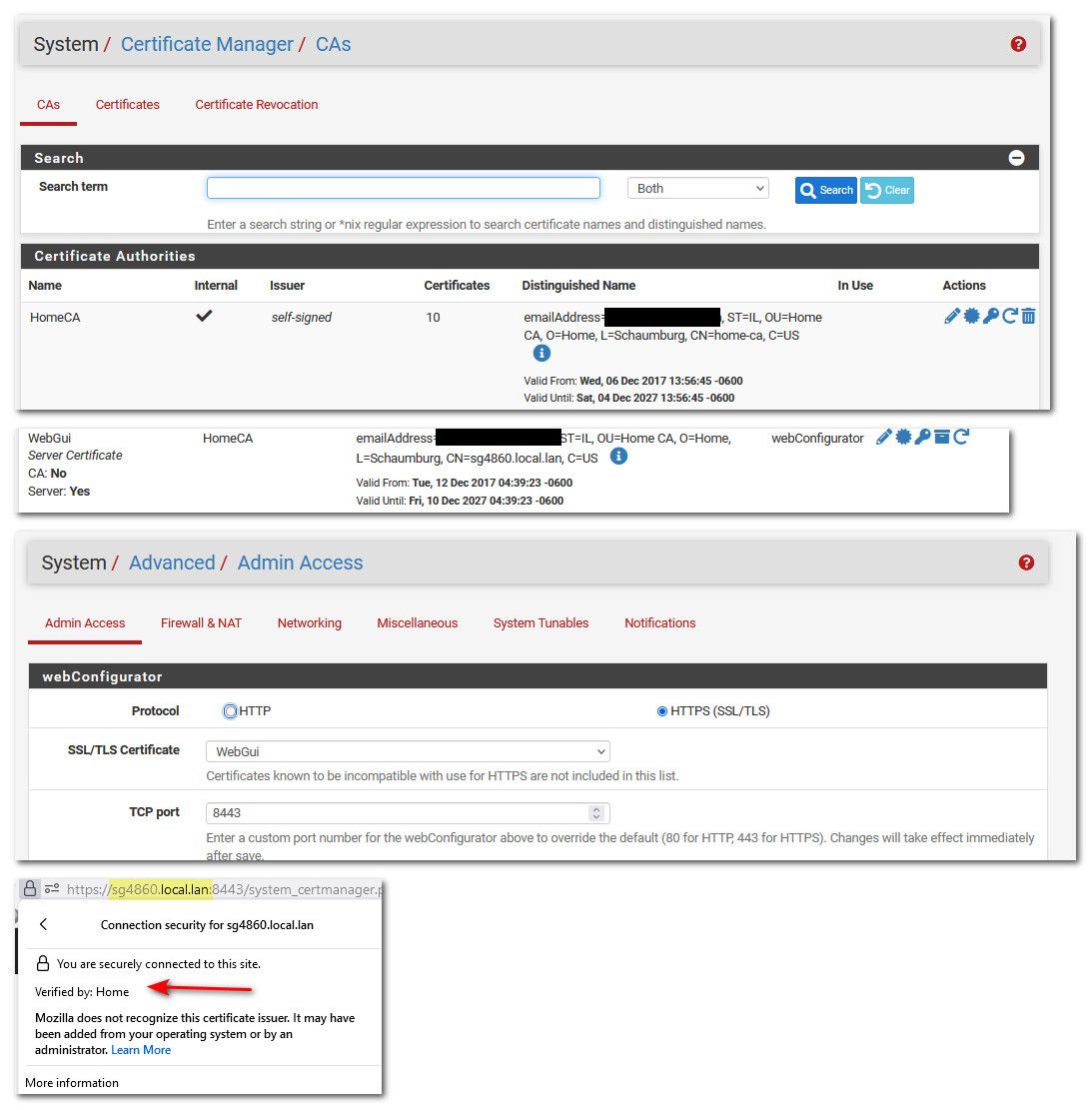
You can put whatever SANs you need to IPs, old name, etc..
I had created this cert way before browsers started limited valid dates to like 398 days or whatever they limit to these days.. So you can see mine is good til 2027, and browser has no complaints about it.
Once you create this CA you can create certs for any other stuff on your network that wants a cert, printers gui, switch gui, unifi controller gui, nas gui, etc. etc.. And since you trust the CA in your browser it will be happy with the cert and no complaints.