Help me to understand NAT configuration (1:1 & Outbound + PortForward?)
-
Hello Everyone!
I am having an issue to configure NAT from firewall and here is what I have.
-
1:1 NAT configured,
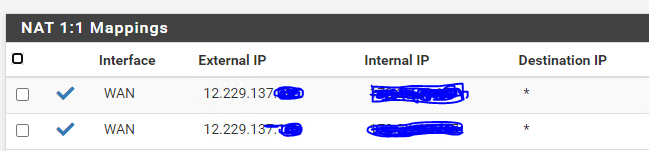
-
Outbound configured for WAN/LAN respectively,
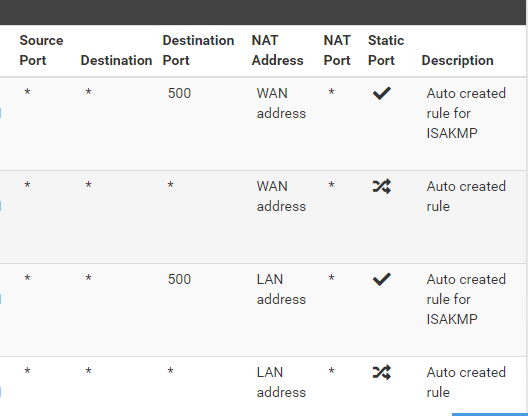
I was thinking my NAT rule has an order (1:1 NAT rule first, Outbound next), but I could NOT reach servers which has specific 1:1 NAT rule.
When I tried to create 1:1 NAT rule to Outbound, still not accessible.
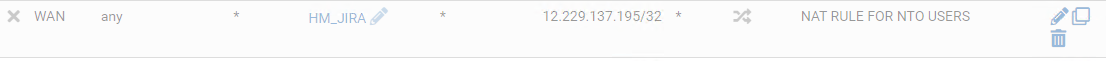
Can you tell me where did I miss?
Thank you for the response.
-
-
@eeebbune 1:1 NAT allows connections arriving on that interface (usually WAN) to an IP on an internal interface (usually LAN or DMZ).
Outbound NAT controls how connections out from an IP address to the Internet go out. (PC on LAN connects out to a web site)
They are completely different things.
As to why it doesn't work, does the server have a software firewall, and if so does it allow traffic from the Internet?
-
@steveits Appreciate your response.
If I correctly understood, 1:1 NAT is matching inbound traffics to be private IP address and outbound is matching outbound traffics.
Which means if I create 1:1 NAT to be either
LAN (interface) - External IP(Public IP) - Internal IP(Private IP)or
LAN (interface) - External IP(Public IP) - Internal IP(Private IP)
WAN (interface) - External IP(Public IP) - Internal IP(Private IP)Then it would be the solution?
Most community users recommends to configure PortForward. Would you agree with that? If so, may I ask you why?
By the way, I have allow any to server IP with all port rules to both WAN/LAN rule tabs.
Thank you very much.
-
@eeebbune 1:1 NAT forwards all ports.
If you are trying to get to your server from LAN using the public IP address, you'll still need Reflection enabled (see "Enable NAT Reflection for 1:1 NAT"). I would get it working from outside first, then worry about the LAN.
BTW, for 1:1 NAT you don't need to configure Outbound NAT.
https://docs.netgate.com/pfsense/en/latest/nat/1-1.html
"All traffic originating from that private IP address going to the Internet through the interface selected on the 1:1 NAT entry will be mapped by 1:1 NAT to the public IP address defined in the entry, overriding the Outbound NAT configuration."@eeebbune said in Help me to understand NAT configuration (1:1 & Outbound + PortForward?):
allow any to server IP with all port rules to both WAN/LAN rule tabs
If I'm reading that correctly and you've allowed all traffic to the server on WAN, when using 1:1 NAT that includes all ports, so SSH, HTTP, SMTP, FTP, NetBIOS, remote connections, etc., etc. I would really recommend against that and only allow the necessary traffic. See https://docs.netgate.com/pfsense/en/latest/nat/1-1.html#risks-of-1-1-nat