wireguard with dynamic routing
-
What is the best way to handle dynamic routing with wireguard?
I have a single wireguard tunnel running bgp.
The allowed IPs currently have the wireguard transit network (/30) and also the LAN subnet of the remote end. There are a few more LAN subnets i need to access. Do I need to update the AllowedIPs for each remote network? If I do, doesnt that defeat the purpose of dynamic routing? -
-
@stephenw10 thats the thing...i did read it. I guess im not following at all.
WireGuard requires Allowed IPs to decide where to send specific networks. In that case, having to define these networks manually negates the purpose of dynamic routing. Using a single peer allows WireGuard to send any traffic it needs across the interface, including arbitrary networks.
So in the allowedIP list i only include the transit address of the WG interface?
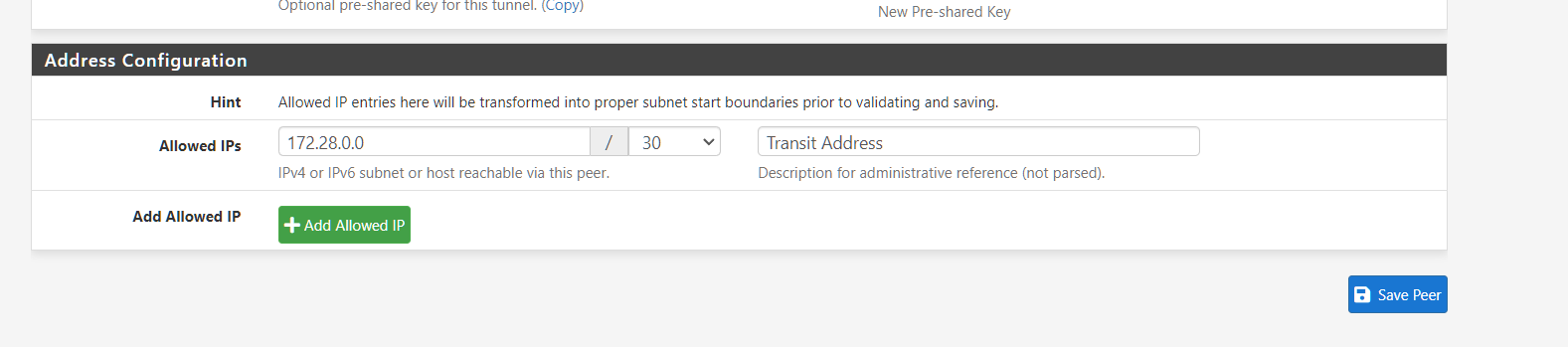
EDIT
I am attempting to ping 10.0.1.1The network is learned via BGP and i can see it in the output.
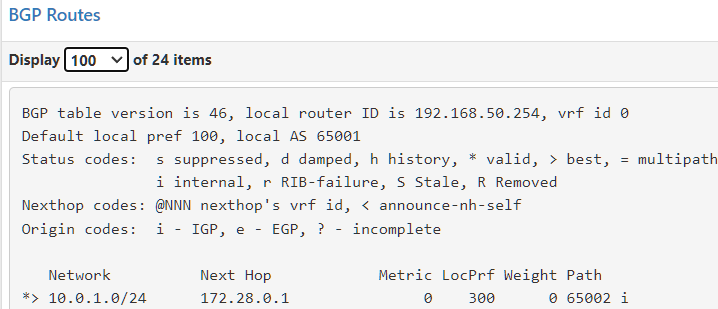
The problem is that i dont see it in the route table of pfsense
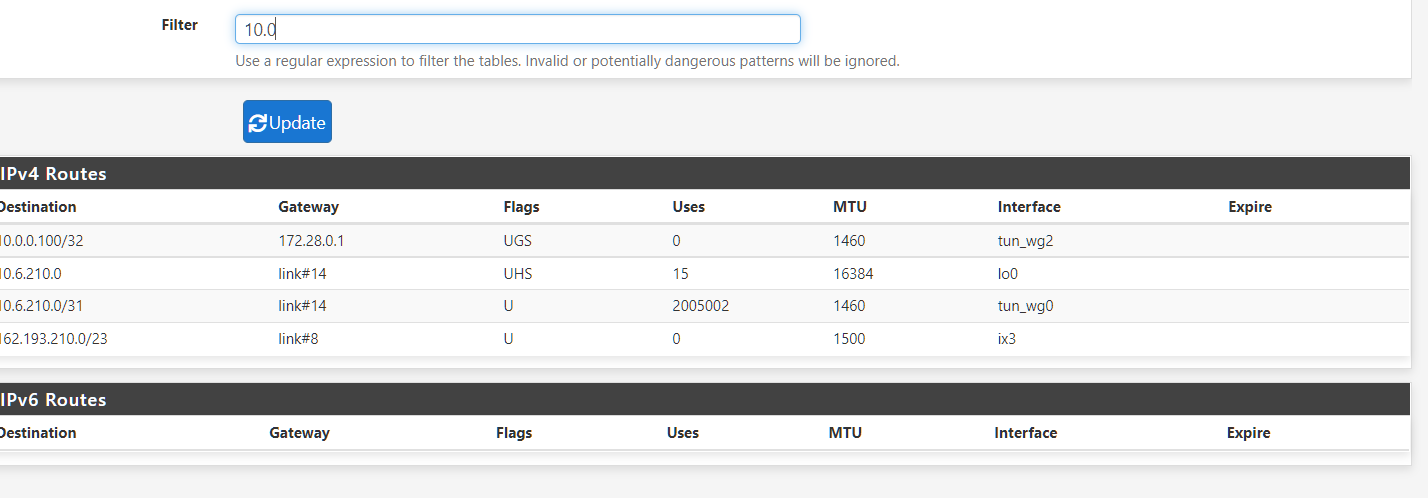
-
It's seeing the neighbour OK on both sides?
You will probably need to set the allowed IPs to any to actually route traffic bit it should see the routes being announced as long as it's sending from the tunnel address inside that /30.
-
@stephenw10
How do you set the AllowedIPs to any?
A route is being received from the neighbor -
@michmoor Ok figured it out. Allowed IP is 0.0.0.0/0
The documentation doesnt state this at all.
"When more than one peer is connected to a single WireGuard tunnel, WireGuard requires Allowed IPs to decide where to send specific networks. In that case, having to define these networks manually negates the purpose of dynamic routing. Using a single peer allows WireGuard to send any traffic it needs across the interface, including arbitrary networks."
Better wording needs to say something along the lines of 'permit all routes using this syntax 0.0.0.0/0 in the Allowed IP section and ensure routes are received from the remote peer. Control of traffic to destinations is handled by firewall rules"
-
It's somewhat shown in the peer settings page but I agree it can easily be read as Wireguard will allow any traffic as long as there is only one peer. That is not the case, as you found you must configure it to allow all traffic.
Steve
-
@stephenw10 Just glad this has been sorted out :)
So for future me when i forget how I did this... "add 0.0.0.0/0 to the allowedIP" section to have dynamic routing, route traffic over the tunnel.