DNS panflully slow when running Egress rules on LAN?
-
I am getting very slow browsing and DNS with Egress rules in place.
Everything is lightning fast when allow all is at the top.
Kind of annoying.....
Any suggestions?
-
@cool_corona
Suggestion ....
Use Reject instead of Block in the rule's top "Action".
Should send an immediate "Reset" instead of "Drop" and wait for TCP timeout.You would normally only use Reject on "Inside interfaces" (non public) , as it would also speed up an attacker's portscan, on the wan interface.
By egress , do you mean floating rules ?
/Bingo
-
Only running on specific interface for testing purposes.
After applying the Egress rules, only cached requests are fast. New requests takes 3-5 seconds to reply.
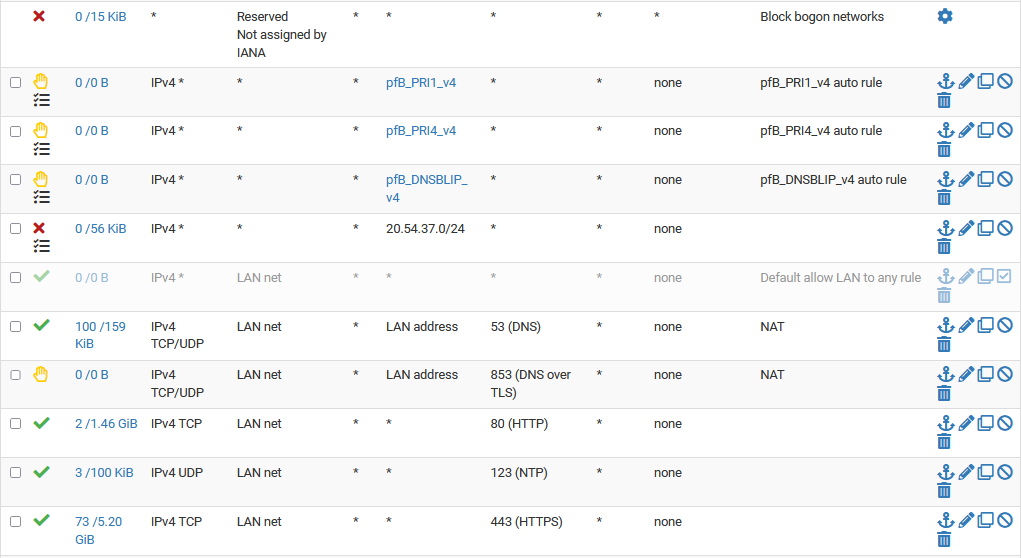
This is the Egress rules.
-
@cool_corona egress rules on the lan? Did you create egress (outbound) rules in floating?
All rules are evaluated inbound into an interface from the network the interface attached too, those would be ingress rules..
Use of the term egress you mean leaving the lan network.. but the rules would be ingress into the interface.
So your doing dns interception, that is the only way that 1st rule makes sense, you really should have tcp as well - dns can use udp and tcp.
Your second rule for 853 would always be TCP, and you have it only for udp.. Did you actually setup unbound for tls queries to it, what cert did you setup that your clients dns client is going to trust?
Your ntp rule you have as tcp, but ntp is never tcp it is always udp.
-
@johnpoz Thanks.
I will change it and test. I block DNS over TLS.
-
@cool_corona said in DNS panflully slow when running Egress rules on LAN?:
I block DNS over TLS.
Not in your rules you don't Why would you have the 853 allow rule as an interception rule if your blocking? Unless since your not actually listening it wouldn't work anyway so that is block?
Is your client trying to do that and its waiting for timeout, before it does a normal dns query? But I don't see any hits on the 853 rule, and the normal dns udp rule looks like really no hits either 6 KB? But maybe you have a rule above that allows directly to pfsense and that is only your redirection.
When posting rules it very helpful to show the headers, so you know for sure there are no rules above, and also show floating or specifically state you have no rules in the floating tab, etc.
example - from this posting you can see very clear what interface the rules are on, and that your seeing the full rule listing, etc..
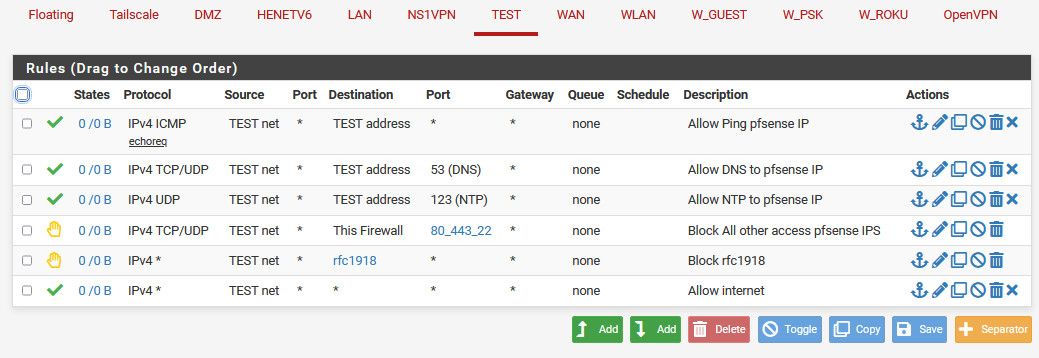
Your rules you have * as source - why would that not be lan net? Are you using lan as transit and have downstream networks.. But since you don't even call out the source network, and don't show the headers - have really no idea if those rules are your lan, or some other interface - maybe even floating tab?
-
-
@cool_corona blocking bogon on a lan side interface is normally never a good idea.. That rule is not a destination rule that is a source rule. How would you have source traffic coming into your interface with a bogon source?
And if your rules limit to the net your on, say lan net then the default deny would stop anything with a bogon source anyway.