Starlink Integration with Dual WANs
-
Greetings pfSense Community.
Over the past two months, I moved pfSense to a VM after the MikroTik J1900 Router failed. I purchased a replacement, Protectli Vault 4 and began moving to the new FW. Starlink sent me my dish, so I decided to setup the new FW with dual WAN as shown in the diagram.
The problem is that I cannot get pfSense to send the appropriate packets to any of the servers.
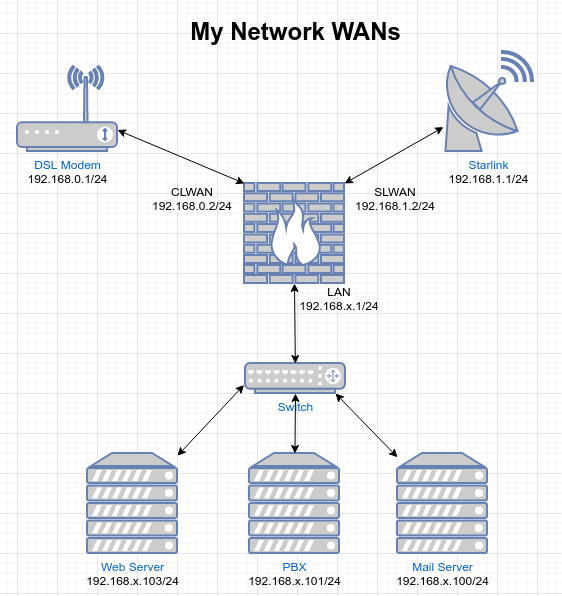
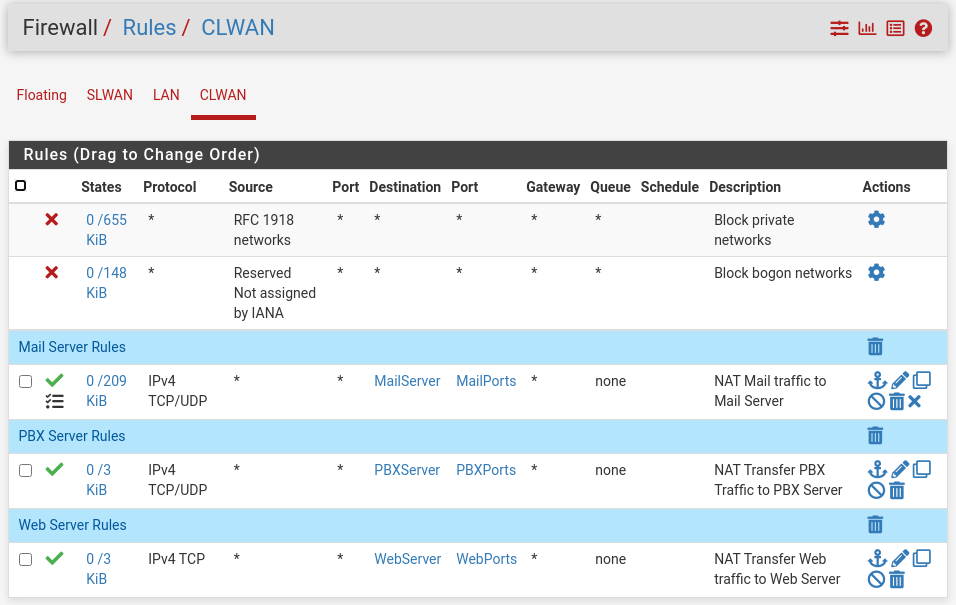
All servers that need a public IP address will use the CLWAN, DSL, and other computers would use the SLWAN, Starlink. The Web Server, Mail Server and PBX will use CLWAN.
The rules are identical to the rules that are working on my VM FW.
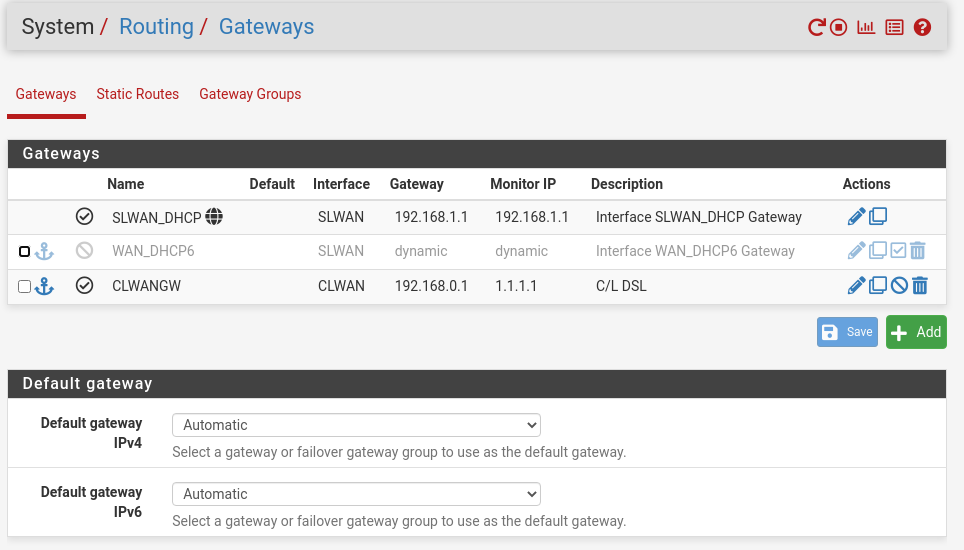
And here are the two Gateways. I did not setup a Gateway Group.
tcpdump shows packets correctly routed to the FW but there is no out bound traffic to the LAN.All three servers use the CLWAN for outgoing traffic.
I chose this approach because I do not intend to maintain the DSL link until I select another solution.
I could not find any similar configuration or problem in Google.
Any thoughts suggestions or reference material that may be of use.
Thanks,
Jens -
@jemadsen So if your issue is inbound traffic, and the WAN gateways are private IPs, do you have NAT rules set up as well? The ISP router would need to forward those ports to the pfSense router, for pfSense to see them.
-
@steveits
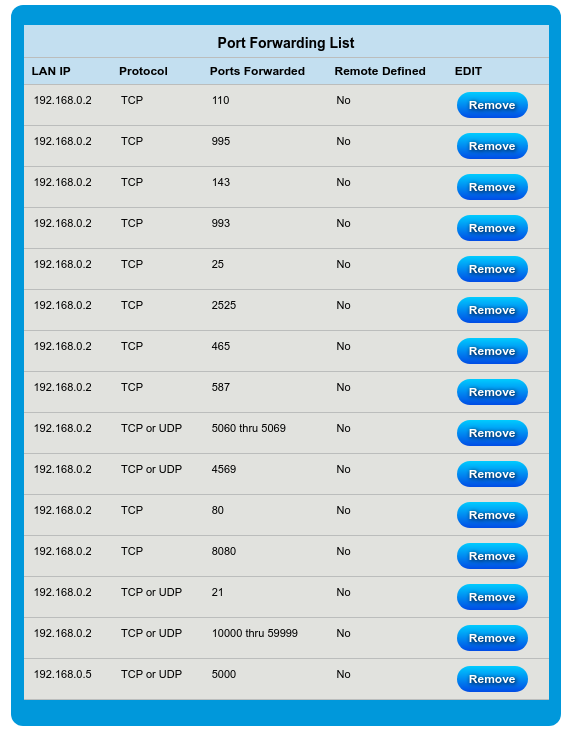
Thanks for your response. Sure do.
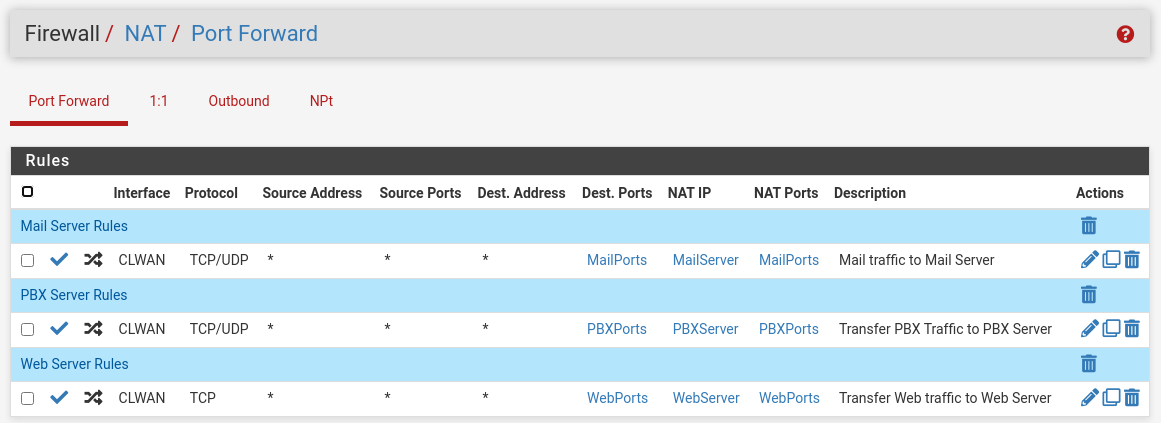
-
@jemadsen And also in the ISP router?
-
@steveits The modem is currently setup with my pfSense VM and works fine. It is when I switch with the VM that I have problems. The only difference is the additional WAN.
-
@jemadsen Hmm. I have seen some routers (AT&T) which select port forwards by MAC address which is both useful and annoying.
If you set up NAT reflection can you access it from the LAN?
Did you run through https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat-port-forwards.html ?
If you do a Diagnostics/traceroute out from pfSense CLWAN does it make it out?
Did you restore the VM config to the new hardware? (thinking, maybe, an incorrect subnet mask? there are places where it defaults to /32)
-
@jemadsen
Thank you Steve for the recommendations.
I will look into reflection and it sound like it will help.
I have been doing traceroutes, tcpdumps, netcats. I setup a dual setup, where the VM FW handles the mail, VoIP and Web traffic. The Proctectli handles the rest of the traffic thru Starlink.
I scanned some of the troubleshooting document and tried the recommendations.
I initially started with the VM configuration, but when it didn't work, I reset and manually configured the Proctectli. The VM was my learning environment with more "STUFF" to take into account to troubleshoot.
I have built up several pfSense FWs over the years and I know most of my mestakes, unfortunately, I am also good making new ones.
Having the VM FW to use as reference. I searched for some example similar to mine, but all were failover/load balancing.
I need to get my servers back online so I am using both FWs one that works for the CLWAN and the other for the SLWAN. It working now. Next I will build up a test setup on my VM Server and trouble with that.
I will continue to look for an example or recipe. It is my birthday this weekend.