Conflict between WAN and VPN interface/gateway
-
@sticilface said in Conflict between WAN and VPN interface/gateway:
pfsense (2.9.0)
There is no such version..
Why would you be using a /8 mask? 10.x is not a CGnat address range. But if your going to use such a large mask on that interface, then no you wouldn't be able to use 10.x anything elsewhere because they overlap.
Why can you not use say a /24?
If you can not change that mask from /8, then use the other rfc1918 ranges for other networks you want to use locally, 172.16-31.x.x or 192.168.x.x
-
sorry its a typo. version 2.6.0! attempted to correct it but post is labelled as spam for some reason.
@johnpoz said in Conflict between WAN and VPN interface/gateway:
Why would you be using a /8 mask? 10.x is not a CGnat address range. But if your going to use such a large mask on that interface, then no you wouldn't be able to use 10.x anything elsewhere because they overlap.
I do not have control over this it is assigned via DHCP.
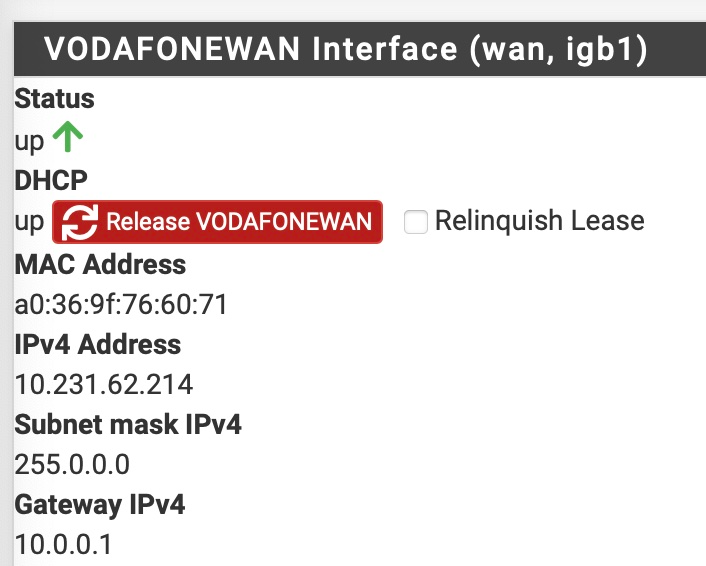
If I try an set it as a static IP
10.231.62.214and the gateway10.0.0.1I get the following error.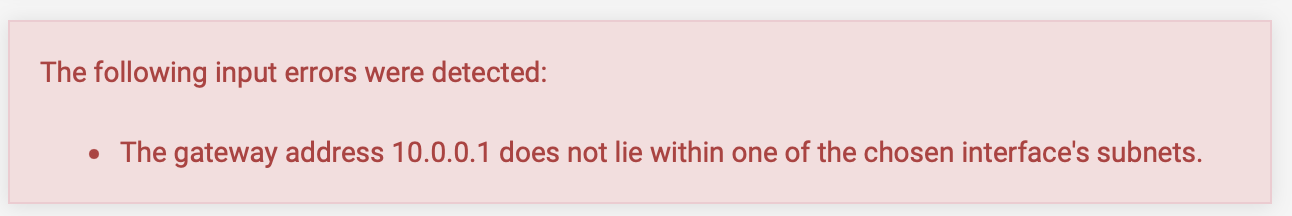
@johnpoz said in Conflict between WAN and VPN interface/gateway:
If you can not change that mask from /8, then use the other rfc1918 ranges for other networks you want to use locally, 172.16-31.x.x or 192.168.x.x
I am using 192.168.1.x locally this is not a problem. The issue is that I now have the VPN interface which has an IP address that I also do not control and this has been set as below:
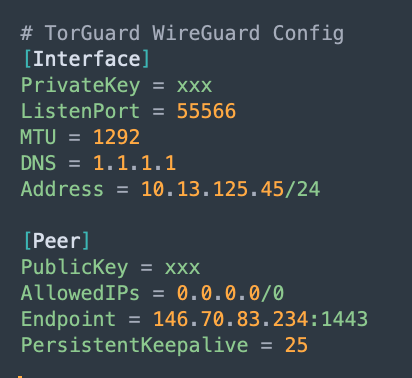
so both TorGuard and vodafone are using the same IP ranges on their networks and I cannot control this.
Is there a way around this?
@johnpoz said in Conflict between WAN and VPN interface/gateway:
172.16-31.x.x o
I attempted to use a virtual IP for vodafone but I couldn't get it to work. but probably because I'm not sure if this is even the correct approach.
Thank you for the lightening fast reply.
-
@sticilface what does your wan connect to - some vodafone router I assume, can you not log into it and change the lan network mask?
-
-
@sticilface said in Conflict between WAN and VPN interface/gateway:
It's configured in bridge mode so no.
Your in bridge mode and you get a 10/8 address? Well put it back in router mode then.. A mask of /8 is not going to allow you to use other 10.x networks anywhere else..
A 10.x address is not going to allow you do do anything inbound anyway. So there is little point to bridge mode, normally use bridge mode so pfsense gets a public IP on its wan. If your just going to get a rfc1918 address with such a large mask that is causing you problems, the easiest solution so you can use other 10 networks is just to double nat.
-
@sticilface Sounds stupid at first but use a VM (with OpenWRT) for every VPN connection. I have it setup like this and is working quite good.

Johns advice sounds good too.
-
Mmm, tricky situation.
Yeah using the ISP device in router mode is almost certainly easiest. It's an extra level of NAT but you're already double NATing so not much difference.
Otherwise you might be able to do something with custom overrides in the DHCP client and allowing a gateway outside your subnet. But that's always going to be hacky and liable to stop working.
Steve
-
Thank you @johnpoz
Reconfigured in router mode so i'm now triple NAT'd but i guess it makes no difference as you say.I now have this working as expected.
I would be interested in any other solutions, if for example I want to use another VPN that happens to allocate in the same address space. Seems sub optimal that your network structure is dependent on IP addresses you do not control. @Bob-Dig as you say maybe multiple VMs is the answer.
-
@sticilface said in Conflict between WAN and VPN interface/gateway:
as you say maybe multiple VMs is the answer.
how would that be a solution to your same network problem? if the vpn is using the same network as the location trying to connect, or your local networks are the same as the remote network.
If your on some network 192.168.1/24 and the tunnel is 192.168.1/24 or the remote network your trying to get to is 192.168.1/24 your going to have a bad day..
Why best not to use very common network, 192.168.0 and .1/24 are the most common default network, its best not to use those ;)
-
@johnpoz Especially with WireGuard, some Privacy-VPN-Providers do funny sh!t. Even with OpenVPN it was a pain in the a. (PIA?) with overlapping tunnels, now its often even worse, like every tunnel get the same IP. But depends on the pVPN-Provider.
-
Indeed I totally agree. I'm using 192.168.1.255 address space locally.
My question relates more to what do you do when there is a clash between interfaces when you do not control the address or gateway given to it by your ISP. In this case I was lucky as i could reconfigure my router.
But hypothetically I wanted to use two VPNs one in the UK and one is Spain (by different providers) and they both give you the same address.
Could you configure Pfsense to perform NAT (similar to me reconfiguring the modem from bridge to router mode) on an interface before handing it over as a gateway.
Re the multiple VMs solution, you can have each instance of pfsense connect to the VPN and then perform the NAT via your local IP... Thats how I interpreted the OP comments... so if you want to access VPN2 you route that traffic to that VPNs address on your network.
-
@johnpoz said in Conflict between WAN and VPN interface/gateway:
how would that be a solution to your same network problem? if the vpn is using the same network as the location trying to connect, or your local networks are the same as the remote network.
It doesn't help accessing something at the end of the VPN but it does allow you to have multiple VPNs where the tunnel subnets conflict. Like 5 connections to PIA where they all give you the same tunnel gateway for example. No way to do that in pfSense directly.
Steve
-
@sticilface I only do NAT in OpenWRT for those pVPNs, between pfSense and OpenWRT it is routed.