FIOS - getting /56 PD via DHCP6 but no V6 is assigned to WAN
-
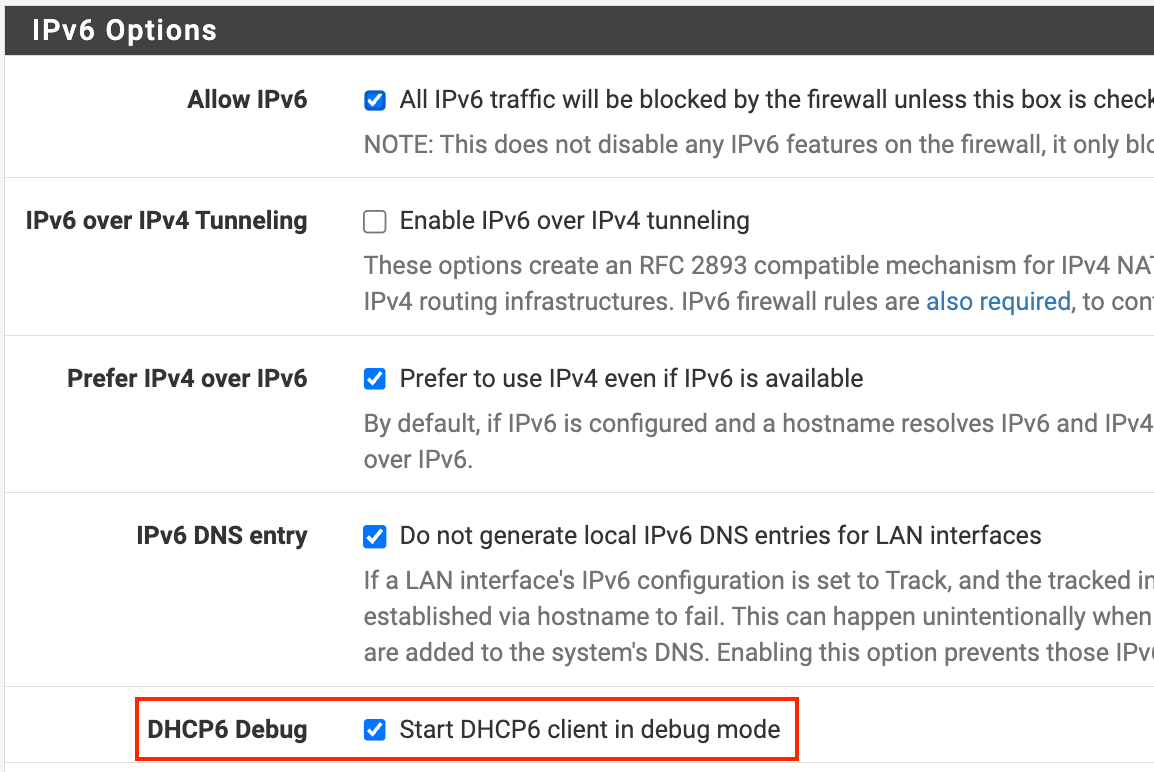
@betapc I'm not sure. Do you have debug enabled for dhcp6?
-
@luckman212 Yes I have that option check.
-
@betapc I'm sorry but I'm really not sure where to point you next. Maybe someone else has an idea...
-
@luckman212 Thank you very much. I will wait for pFsense version 23.01 to be release and see what happen when I do a clean installation.
Do you think ipv6/dpinger fixes from PR #4595 will be included on version 23.01? and maybe a fix to handle IPv6 to WAN for cases like this on Fios?
Thank you for your contribution to pFsense.
-
Finally I make it work, I upgrade to 23.01 RC, removed limiters and WAN firewall rules for Bufferbloat mitigation, then I change on your scrip the python version from 3.8 to 3.9 and works.
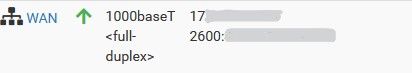
The only problem is the getaway still showing the local IPv6 and not the one from Verizon, and is unable to identify if the getaway is
online or not.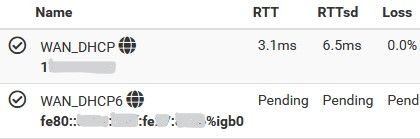
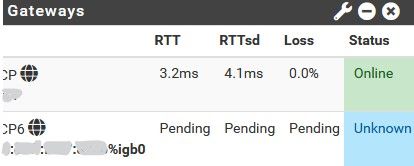
So this is normal behavior? or I need to do something else?
Thanks @luckman212
-
@betapc Verizon doesn't provide a global address to the WAN interface. They only provide a prefix that the router can use.
Verizon's own router takes an address from the "ff" prefix ID and assigns it to the WAN interface. pfSense does not provide an automated way to do the same though. I had manually accomplished the same thing by setting a virtual IP on WAN... but if my prefix ever changed in the future, I would need to change the virtual IP to match the new prefix. So I gave up on that.
I think @luckman212 had created a script to do something similar, that you could run regularly to change the address if the prefix had changed... I never looked closer at it though. I'm happy without a global WAN address... things work, that's what matters.
Mine seems to be happy pinging Verizon's end of the link-local route... not sure why yours would have problems with that. If you had a monitoring destination manually set, you'll need to remove that since the only thing it'll be able to ping without a global address is Verizon's end of the link-local route.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
Parts sound alike the problem described here
https://forum.netgate.com/topic/177981/no-ipv6-after-upgrade-to-23-01
-
Good evening, are there any plans to update the system patch or the script for pfsense 23.01+ and devd integration. I find this to be particularly useful with dynamic dns that I use for sending IPv6 traffic to my existing pfsense. It helps a lot having an IP from gua in a somewhat automated fashion. Thanks for writing this, I am still baffled by how this script works, I need to brush up on my bsd scripting.
I think this would be a good feature for the mainline pfsense releases.
-
I'm on CE 2.6 and just want to ask a question before I start trying to implement @luckman212 's workarounds to obtain a GUA for the WAN interface.
Would a GUA for the WAN interface allow me to use HAProxy to listen on that interface via a proxy front end definition? I want to use HAProxy to connect IPv6 clients to a backend Mastodon self-hosted server. I'm guessing that isn't working even though HAProxy's front end is set to listen to IPv6 on the WAN because that interface has no GUA.
Thanks.
-
For anyone who, like me, upgrades from CE 2.6 to CE 2.7, be sure to change @luckman212 's script to reflect the latest version of python. See my pull request here.
-
@yobyot this issue has been fixed in the latest 23.05.1 update
-
@maverickws said in FIOS - getting /56 PD via DHCP6 but no V6 is assigned to WAN:
@yobyot this issue has been fixed in the latest 23.05.1 update
Except I use CE 2.7 due to Netgate licensing.
On that point, it breaks my heart that to monetize pfSense, esp 7.2, which essentially means I can never use pfSense+ with client systems. That section along with others makes it impossible to assure my clients that nobody but me is accessing their systems.
-
Hi,
I am using pFsense plus 24.03, I am still having same issue where WAN interface only got a local IPv6 and not a IPv6 assigned by FIOS, is a problem when I configured CoDel Limiters for Bufferbloat, limiters work fine for IPv4 but not for IPv6 since it doesn't have a IPv6 and can identify traffic going through the WAN.
I tried your patch and I was unable to make work.
Are you aware if pFsense plus 24.03 already fixed this issue, and let me know what is the configuration we have to use to make WAN to obtain and IPv6 or how to make the onfiguring CoDel Limiters for Bufferbloat to work with IPv6 traffic.
Thanks.