Amazon and Default route 0.0.0.0
-
Hello fellow Netgate community members,
I have noticed a while ago that our Amazon fire HD likes to attempt to use 0.0.0.0 a lot, I at first blocked it because I had entered the proxy address into the Amazon tablet. However I today decided to add a NAT so that 0.0.0.0 just is directed to the firewalls interface. It seemed to help.
Does anyone else do this?
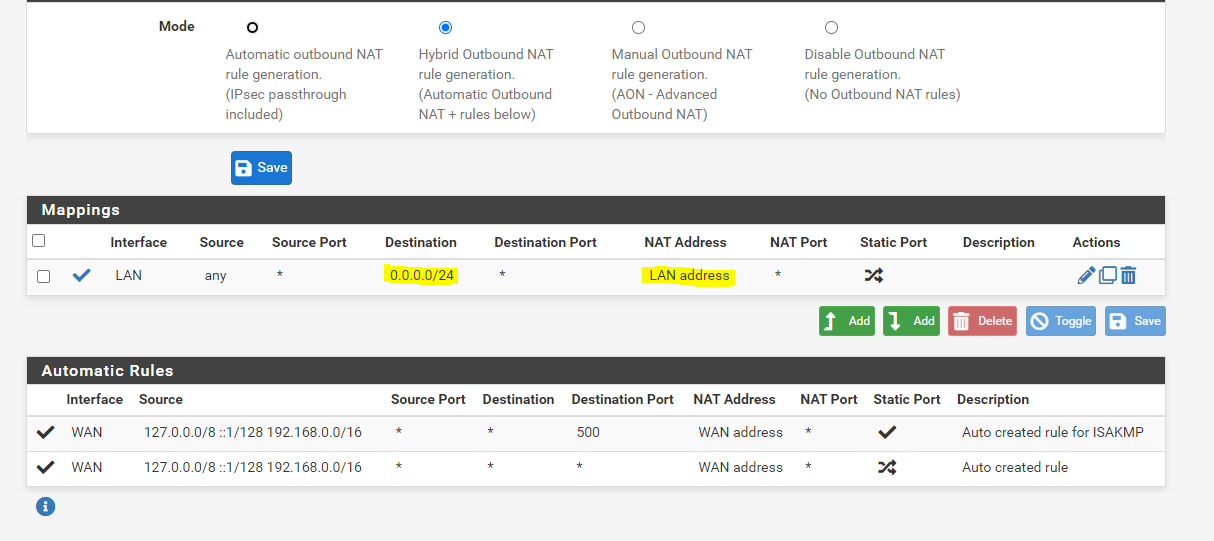
-
@jonathanlee i have applied setting let's see, now i feel some improvement on few devices
-
What traffic is it sending to 0.0.0.0? That is a non-routable IP address, you should never see anything sending traffic to it.
Steve
-
@stephenw10 only Amazon traffic does this,
In the world of Cisco this is 0.0.0.0 the default route.Per Juniper networking,
"The default route in IPv4 is designated as 0.0. 0.0/0 or simply 0/0. Similarly, in IPv6, the default route is specified as ::/0. The subnet mask /0 specifies all networks, and is the shortest match possible."
Amazon just wants the next hop so they can have it now as ip address of the firewall.
-
Yes it's a valid route. It's not a valid destination IP address though. You should not see packets being sent to it.
It's probably a bug where 0.0.0.0 has been used to indicate no address exists and something else has used that without checking it.Steve
-
@stephenw10 I use to try to block it for the Amazon tablet however the fire HD tablet started flooding traffic to that destination. Almost like the tablet wanted the know the default route. We have an Apple airport extreme in bridge mode for WiFi I wonder if that was the reason with a 192.168.1.2 address that maybe the reason. As soon as I set up that NAT it all stopped I do not even see a request anymore for address, even the memory usage declined.
-
Remember I did a post a while back about this,
https://forum.netgate.com/topic/171896/default-route-0-0-0-0-being-accessed/
It just got worse the full squidguard log was all 0.0.0.0 blocks for the amazon fire. After this Nat to direct it to the firewalls ip address I do not even see a request anymore.
-
Ha, yeah I'd forgotten that other post. Same conclusion there though. It shouldn't be sending that traffic.
There you were seeing it try to use that address for https which means if you NAT it to the LAN IP then it's going to be trying to get pages from pfSense that don't exist. Your webgui logs are probably full of errors from it's access attempts.Steve
-
@stephenw10 I use to have way to many logs for it, the Nat stopped it. I think the airport extreme caused confusion.
-
@jonathanlee said in Amazon and Default route 0.0.0.0:
I think the airport extreme caused confusion.
Why do you think that?
-
@stephenw10 because it is running in bridge mode however the firewall has 192.168.1.2 set for it so it has internet access. So the tablet connects to the WiFi unit and the firewall issues dhcp for it. Maybe the tablet was sending out requests to get off the LAN to find the default route. For my lan it's the firewall 192.168.1.1. that was the only device that was doing that. It was a new tablet. The logs got worse and worse with it blocked before.
-
That's unlikely. Nothing should send to 0.0.0.0. That's not how you 'find' a default route.
That is happening because something is failing to resolve something or has been set to 0.0.0.0 deliberately somewhere and a bug is causing it to try to use that as a valid address instead of recognising it as invalid. Redirecting that to the LAN IP will simply cause the traffic to hit pfSense where it will probably fail. If it's https traffic the pfSense webserver will have to handle that request and respond with an error which is firewall load that doesn't need to happen.
Better to use a reject firewall rule so that the Amazon device gets a response and knows it cannot connect to that.Steve
-
@stephenw10 It is only the amazon fire HD that does this. Once I set the NAT it stopped.
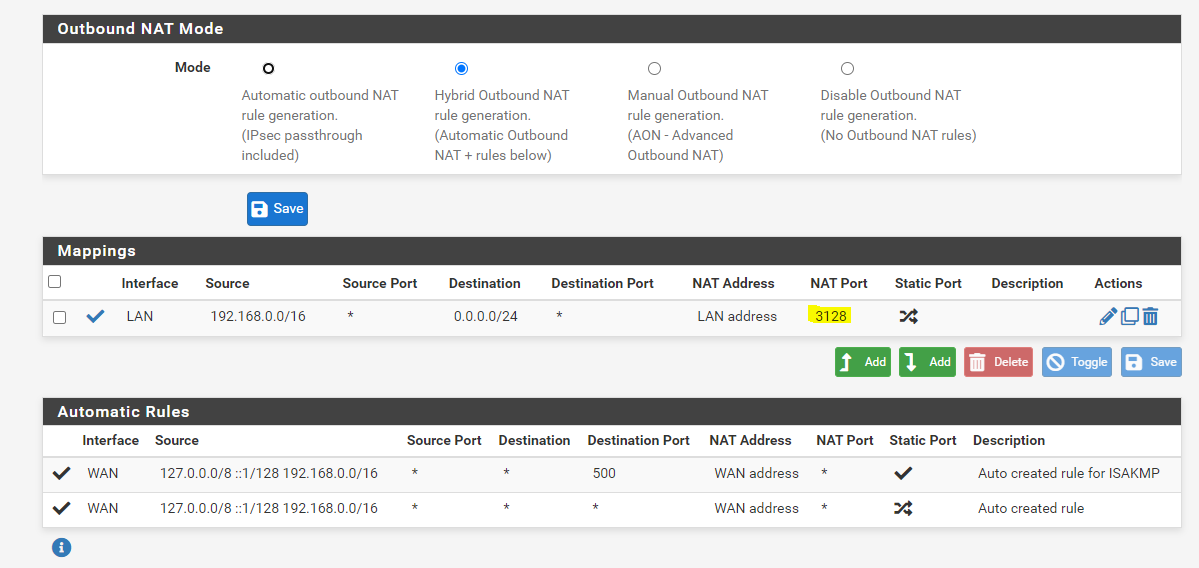
(Image: Nat Lan to 0.0.0.0 redirect to firewall with use of proxy port.)I agree it is weird however the old way to just block it was flooding my firewall non stop when my amazon tablet was running.
-
Did you try using a reject rule rather than block?
That traffic should be blocked or rejected in my opinion. If the only problem is that it's flooding your logs then just disabled logging on the rule.
Steve
-
@stephenw10 thanks for the reply,
I use to have a block for it and network was sluggish to respond with it blocked when Amazon tablet was running. This weekend the tablet actually stopped working and I had to reload a configuration from last week because of timers I had set up on squid guard for Zoom. I messed up something, it was working and all the sudden Squidguard stopped working. The tablet is set to splice, as intercept only worked for the browser. They won't let the certificate run for the other applications unless it is splicing so I can't really see what occurred outside of doubleclick net blocked and that was the last entry before Squidguard was depreciated and went to alarm timers in the logs. The configuration reload without the timers fixed it. Again the 0.0.0.0 is still nat to proxy lan interface and port use 3128
-
So did you try a reject rule rather than block?
-
@stephenw10 I will try that next. Thanks for the recommendation.