Clients get IPv6 addresses, but no working network connection
-
My situation.
pfSense running on Netgate SG3100 router, connected to fiber.
pfSense has a IPv6 address. Ping IPv4 and IPv6 from the router to the internet is working.
My clients in the local network do get a valid IPv6 address, and a IPv4 address. Networking between clients, and to the internet, is working on IPv4, but not on IPv6.
However, I also have a OpenVPN server on the router. When I connect from an external location, to my router, I have a working IPv6 connection (internet tunneled over OpenVPN)!
Somewhere, the routing gets wrong in the internal network side of the router.
My setup used to work correctly. I suspect an upgrade of some kind has caused this issue.
Help is appreciated. -
@innostus This may seem like a very silly question but: do you have an allow rule on your LAN that passes IPV6 traffic?
-
@luckman212 Silly questions don't exist


Protocol Source Port Destination Port Gateway Queue Schedule Description Actions
IPv4+6 * LAN net * * * * none Default allow LAN to any ruleIs this what you mean?
-
Run Packet Capture on the LAN port, filtering on ICMP6, to see if you have Router Advertisements going out.
-
@jknott
During the first seconds I also started a ping6 to google.com.
Is this enough data? What should I be looking for?14:51:11.620463 IP6 2a02:a442:5457::cc41 > 2a00:1450:400e:801::200e: ICMP6, echo request, seq 1, length 64
14:51:12.650994 IP6 2a02:a442:5457::cc41 > 2a00:1450:400e:801::200e: ICMP6, echo request, seq 2, length 64
14:51:13.674961 IP6 2a02:a442:5457::cc41 > 2a00:1450:400e:801::200e: ICMP6, echo request, seq 3, length 64
14:51:14.699007 IP6 2a02:a442:5457::cc41 > 2a00:1450:400e:801::200e: ICMP6, echo request, seq 4, length 64
14:51:15.722957 IP6 2a02:a442:5457::cc41 > 2a00:1450:400e:801::200e: ICMP6, echo request, seq 5, length 64
14:51:16.746940 IP6 fe80::e820:59ff:fee4:c5b0 > fe80::208:a2ff:fe12:49f2: ICMP6, neighbor solicitation, who has fe80::208:a2ff:fe12:49f2, length 32
14:51:16.747037 IP6 fe80::208:a2ff:fe12:49f2 > fe80::e820:59ff:fee4:c5b0: ICMP6, neighbor advertisement, tgt is fe80::208:a2ff:fe12:49f2, length 24
14:51:21.673303 IP6 fe80::208:a2ff:fe12:49f2 > fe80::e820:59ff:fee4:c5b0: ICMP6, neighbor solicitation, who has fe80::e820:59ff:fee4:c5b0, length 32
14:51:21.673795 IP6 fe80::e820:59ff:fee4:c5b0 > fe80::208:a2ff:fe12:49f2: ICMP6, neighbor advertisement, tgt is fe80::e820:59ff:fee4:c5b0, length 24 -
Here's what Router Advertisements look like. You'll see they occur every few minutes. They can also occur after being requested.

These were captured in Wireshark and I used display filters to show only the RAs.
-
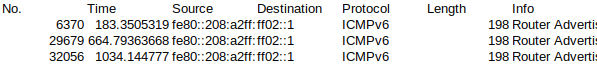
No. Time Source Destination Protocol Length Info
6370 183.350531899 fe80::208:a2ff:fe12:49f2 ff02::1 ICMPv6 198 Router Advertisement from 00:08:a2:12:49:f2
29679 664.793636676 fe80::208:a2ff:fe12:49f2 ff02::1 ICMPv6 198 Router Advertisement from 00:08:a2:12:49:f2
32056 1034.144777006 fe80::208:a2ff:fe12:49f2 ff02::1 ICMPv6 198 Router Advertisement from 00:08:a2:12:49:f2