Netgate 2100 - setup question
-
I am a newbie and trying to revamp my home network.
Existing setup and hardware
-
standard consumer router wan port connected to the following switches (I have 1GB fiber coming in)
-
24 port HP 1410 (S1), 16 port HP 1410 (S2) & 8 Port POE (S3) all are dump switches
My goal is to have 2 VLANS. one is a a VLAN10 for secured stuff and VLAN20 say for IoT.
Here is what I have in mind:
-
Create VLAN10 tied to Ports 2 and 3 and VLAN20 tied to Port 4 using NetGate 2100 software.
-
Connect ports 2 and 3 to two existing switches 24 PORT HP (S1) and 16 PORT HP (S2)
-
Connect port 4 to POE switch (S3)
My assumption is that ALL ports in S1 & S2 will be tagged as VLAN10 and ALL ports in S3 will be tagged as VLAN20 - In other words I do not need to buy managed switches to get this functionality.
Another assumption is that my wireless router (configured as AP) connected to ANY ports in S1 OR S2 will get VLAN10 wifi. If I connected another router (as AP) to ANY port in S3 then that wifi will be tied to VLAN20. Have I got it right?
So far is my understanding correct. Off course I will have to establish firewall rules so that VLAN10 and VLAN20 are completely isolated with the exceptions of "certain" ip from VLAN10 can talk to VLA20.
Please advice.
-
-
@netboy Your correct except the switchports won't be tagged, they will be untagged so your devices will not need to be tagged. Just a wording correction.
If you plug a switch into a router interface, whatever network is on that interface will be available on the entire switch, even the AP's as you said.
-
@netboy From what you said.... the ports 2 and 3 in my example and all the switches connected to those ports including AP's will be "untagged" - My understanding of untagged is they will have only ONE VLAN - in my example VLAN10 - Am I correct. Sorry if I am asking the same question in a different way. I want to ensure I understand VLAN correctly.
-
@netboy
Ah, my mistake. I meant the switches ports, as in your HP switches, but I forgot the 2100 has a built in switch.
Not really familiar with the 2100 but you would probably have to tag the 2100 ports and also the HP ports they connect to but you may want to wait for someone more familiar with the 2100 to be sure.
Can those ports be separated as individual interfaces? -
@jarhead said in Netgate 2100 - setup question:
@netboy
Ah, my mistake. I meant the switches ports, as in your HP switches, but I forgot the 2100 has a built in switch.
Not really familiar with the 2100 but you would probably have to tag the 2100 ports and also the HP ports they connect to but you may want to wait for someone more familiar with the 2100 to be sure.
Can those ports be separated as individual interfaces?Untagged ports in the switch config that reflect a tag on the LAGG0 (mvneta) in the software would just be plain traffic going over the wire.
By default your VLANs won't be able to talk to each other in pfSense on a L3 aspect (unless you mess up your switching and they can L2 with each other).
Make sure you keep the 5th tagged port on all VLANs in the 2100 config.
-
@rcoleman-netgate Sorry I am not able to follow you....this shows my ignorance :-)
-
@netboy If you're following this guide you should be fine: https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/switch-overview.html
-
All VLAN tagged traffic would be internal to the 2100.
The switches and all devices connected to them would appear to be on the expected VLAN interfaces in pfSense. Yes.
If you needed to you probably could pass VLAN tagged traffic through those switches but you would need to test that to be sure. The only reason you might want to do that though is if you added a guess SSID to your Access Point(s) and wanted that traffic to be on a separate VLAN.
Steve
-
@stephenw10
On another note supposing I configure as follows:-
LAN1 port in subnet 192.168.2.xxx and connect this to a "unmanaged switch" say switch2
-
LAN2 port in subnet 192.168.3.xxx and connect this to a "unmanaged switch" say switch3
-
Establish firewall rules such that LAN2 traffic can talk to LAN1 traffic and not vice versa
Will the above work with netgate 2100. The functionality is for me to use my "existing unmanaged switch" and isolate my iot and private network.
Can anybody chime in ......
-
-
Yes, that will work fine.
Steve
-
@stephenw10 Thanks for your response. Shall proceed with this setup
-
@netboy Hey there I am about to buy netgate 2100 and this is what I have in mind. Please note that I DO NOT HAVE managed switch and will not create VLAN. Can I achieve the below functionality: (I would like LAN1 & LAN2 physical ports of netgate to be configured with IP 192.168.0.XXX and LAN3 & LAN4 physical ports configured with IP 172.16.0.XXX - NO VLANS), Not shown in picture is both 192.168.0.XXX & 172.16.0.XXX should be able to access the internet
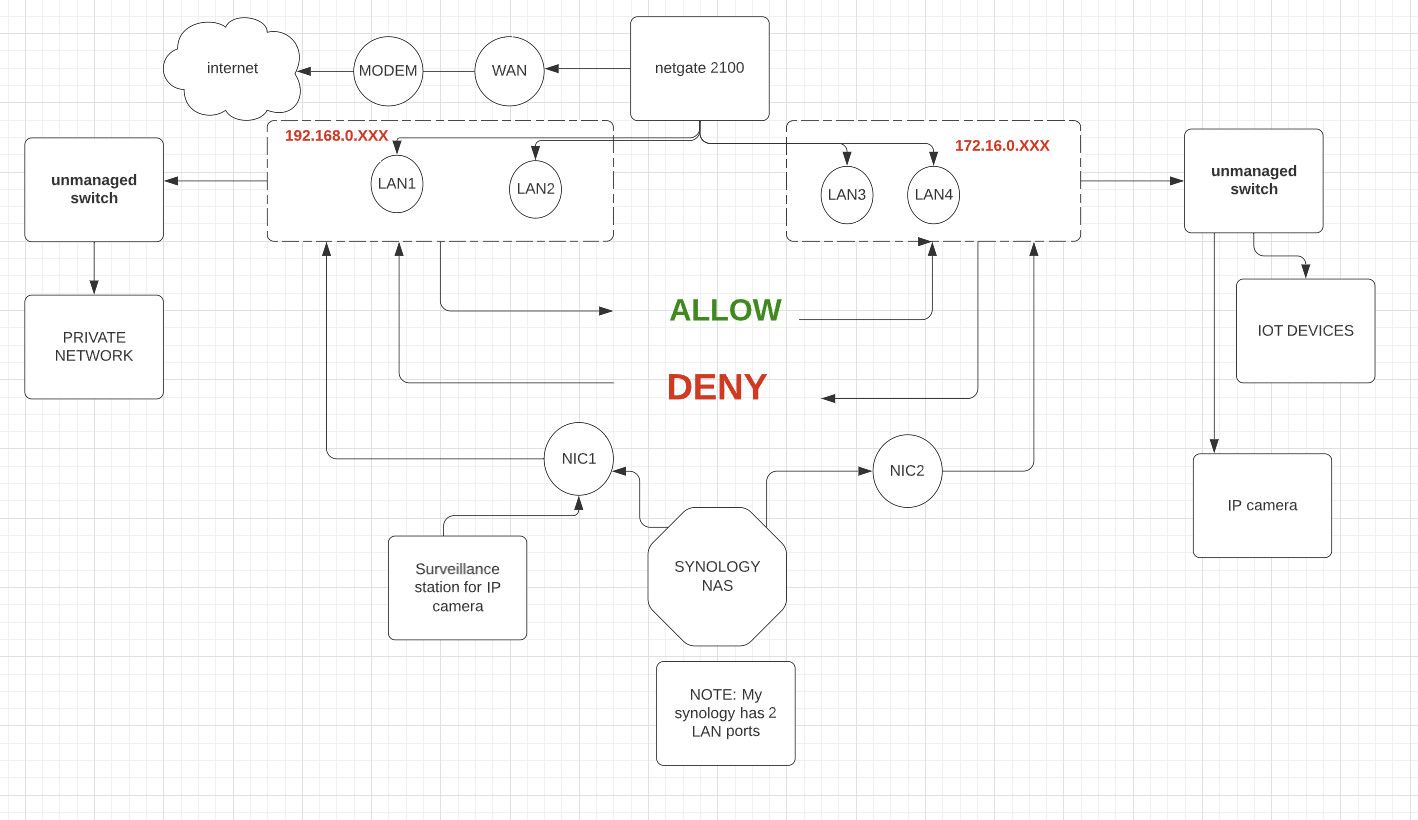
-
@netboy You can’t separate the ports without VLANs. However you don’t need a managed switch. The guide above explains how to do it. In the end, although internally it will be using VLANs, nothing else sees or knows about the VLANs since that’s all internal to the 2100. They become separate ports.
In your case if I followed you, you’d want two ports on the same VLAN.
Another option is to get a 5 port switch for $16 and isolate only one port on the 2100, and plug in the switch.
-
@steveits stephenw10 confirmed this can be done but you say not possible. I am totally confused. Can anybody chime in....
-
@netboy One can separate/isolate switch ports on a 2100. I have one and have done it (and, side note, undone it). You need to use VLANs as directed to do it. You’re trying to do an extra step and put two on the same VLAN. So something like:
Port 1 - unchanged
Port 2 - unchanged
Port 3 - VLAN 4093
Port 4 - VLAN 4093Correct? Nothing you plug in needs to know about VLAN 4093.
-
@netboy This is my understanding so far....
Define two VLANS
-
VLAN1: 192.168.0.XXX (Range 192.168.0.50 to 192.168.0.100)
-
VLAN2: 176.16.0.XXX (Range 176.16.0.50 to 176.16.0.100)
LAN1 & LAN2 -
Assign ports to VLAN1: For VLAN1 remove ports LAN3 & LAN4 but include and "UNTAG" ports LAN1 AND LAN2
-
Assign ports to VLAN2: For VLAN2 remove ports LAN1 & LAN2 but include and "UNTAG" ports LAN3 AND LAN4
-
Setup firewall rules so that VLAN1 traffic can flow to VLAN2 but not vice versa and ensure both VLAN1 and VLAN2 can access the internet
Have I understood the setup? Something similar to youtube video.
-
-
Yes. You can do that and you don't need any separate managed switches to do it. As Steve said the VLANs are all internal to the 2100 so no problem there.
Steve
-
@netboy I'm not very well caffeinated yet, but you only want two networks, correct? So you only need one VLAN. The base-not-configured ports are all one interface out of the box because it's a switch. You're trying to separate two of them.
Or if you follow Ryan's linked directions to the letter to isolate one port, and plug in a cheap 5 port switch, you'd have 3 ports +4 (1->4 remaining switch) ports.
-
@steveits
Now I am trying to implement my idea and seek help.I have changed my default IP for router from 192.168.1.1. to 192.168.0.1.
Can somebody show me screenshots to achieve the following:
-
Create 2 subnets 192.168.0.XXX & 172.16.0.XXX
-
Assign physical port LAN 1 & 2 to 192.168.0.XXX and assign physical port LAN 3 & 4 to 172.16.0.XXX
Please note that I do not use VLAN's - The idea is to connect LAN 1 & 2 to unmanaged switches and so is LAN 3 & 4 to another set of unmanaged switches.
I want to take baby steps as I go so that I can get help from this forum. Thanks
-
-
N netboy referenced this topic on
-
@netboy LAN is already assigned to 192.168.0.1 so ports 1 and 2 are done.
If you follow https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/configuring-the-switch-ports.html that will isolate port 4 and you can assign it 172.16.0.1. I would start with that, and worry about port 3 in a second step.