Netgate 2100 - setup question
-
Yes, if you had the switch connected to ports 3 and 4.
The switch in the 2100 does not support STP to prevent that.Steve
-
@stephenw10 What is STP? Yes port 3 and port 4 are connected to "separate" unmanaged switches so that anything connected to the switch has the 172 subnet.
This was my idea right from beginning.
Are you telling me that I cannot connect any switch to port 3 and 4?
Please note that port 3 is disconnected right now and port 4 is connected to a unmanaged switch. This configuration does not choke up web GUI but once I connect port 3 to a switch the web GUI chokes up.
Kindly advice
-
@netboy said in Netgate 2100 - setup question:
What is STP?
Spanning Tree Protocol.
If you have a link from one network going into another, it cannot detect that and mitigate the cross-talk.
You can connect a switch to those ports, yes, but I was asking you what the rest of those are connected to -- is it possible that one of those switches is connected to port 1 or 2?
-
@rcoleman-netgate You are on the money!!! I had daisy chained the switch which was in port 1 and port 3 because my standby router had only one port and was waiting for 2100 to arrive. Newbie mistake!!! Thanks for pointing this out!
I have now removed the daisy chain ethernet cable connecting switches which were in port 3 and port 1.
Web gui works fine.
Thank you for baby sitting me!
-
@netboy Yeah, don't do that :) It does bad things -- as you have seen. :)
-
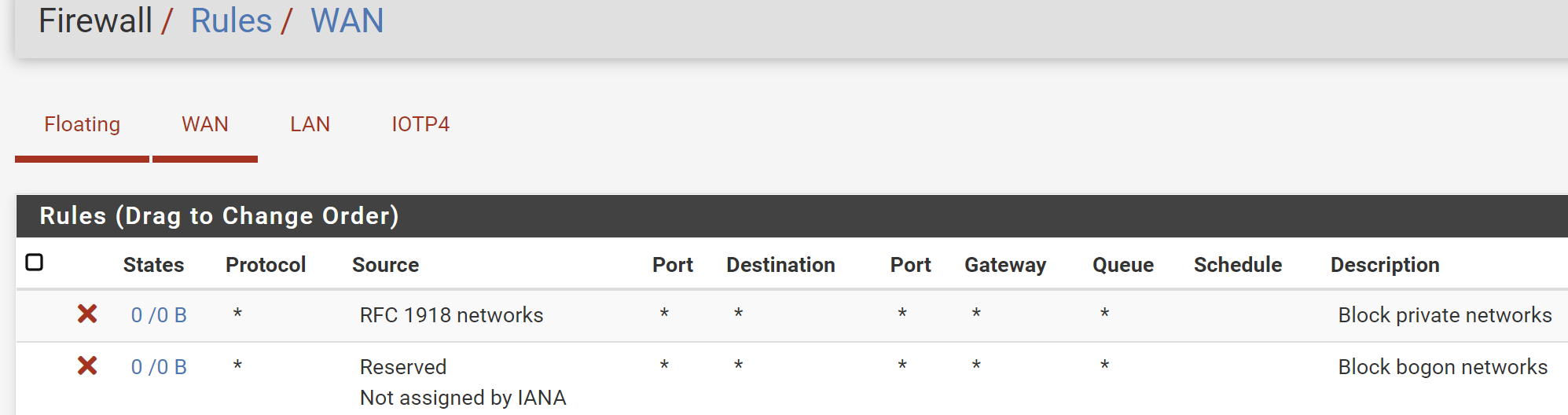
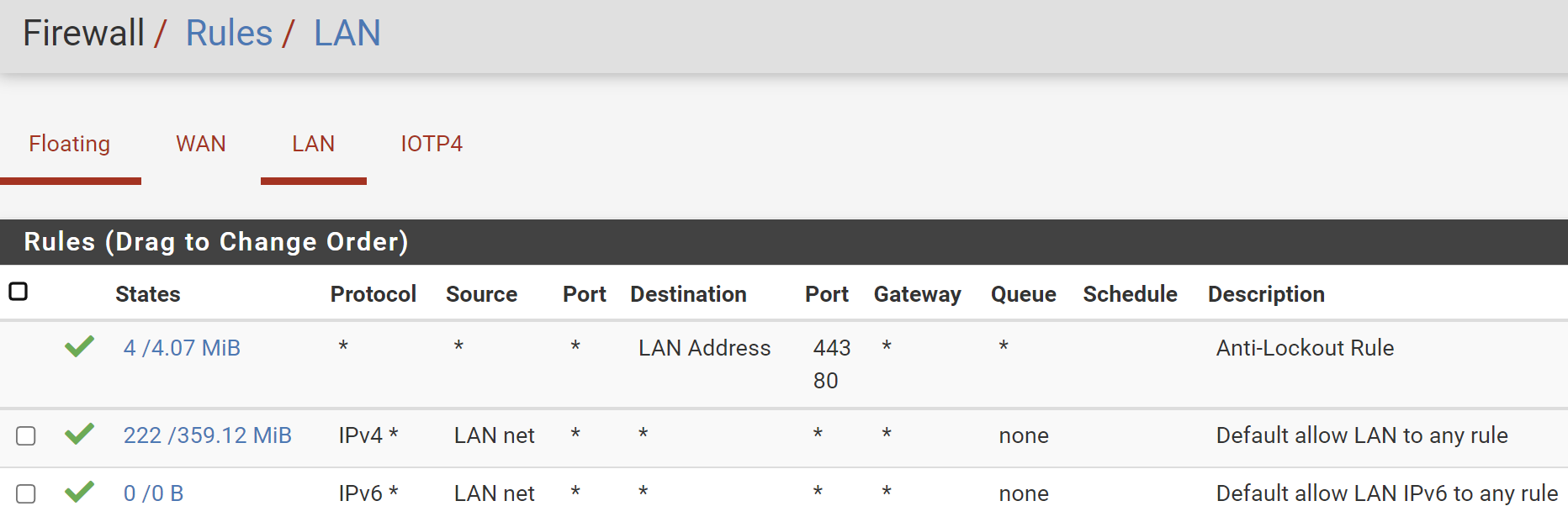
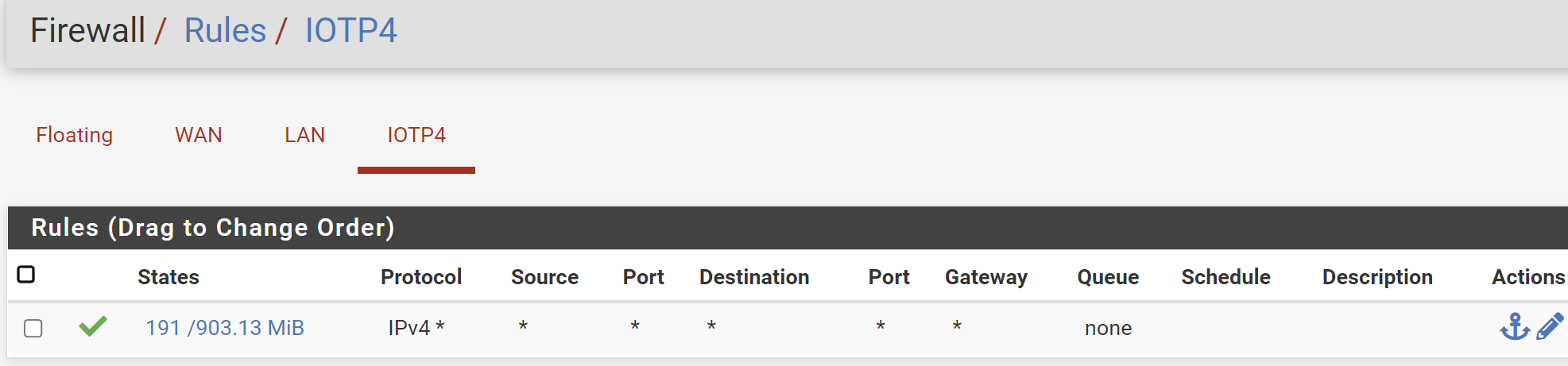
@rcoleman-netgate I need help in firewall rules.
I want 192.16.0.XXX subnet to go to internet and talk to 172.16.0.XXX subnet but I want to BLOCK 172.16.0.xxx to 192 subnet - 172 can talk to internet (allow). This is my existing firewall rules.
IoTP4 is 172.16.0.XXX
-
@netboy So block on LAN interface anything with a SOURCE address of IOTP4 Network. Put that above your "allow all traffic" rule
-
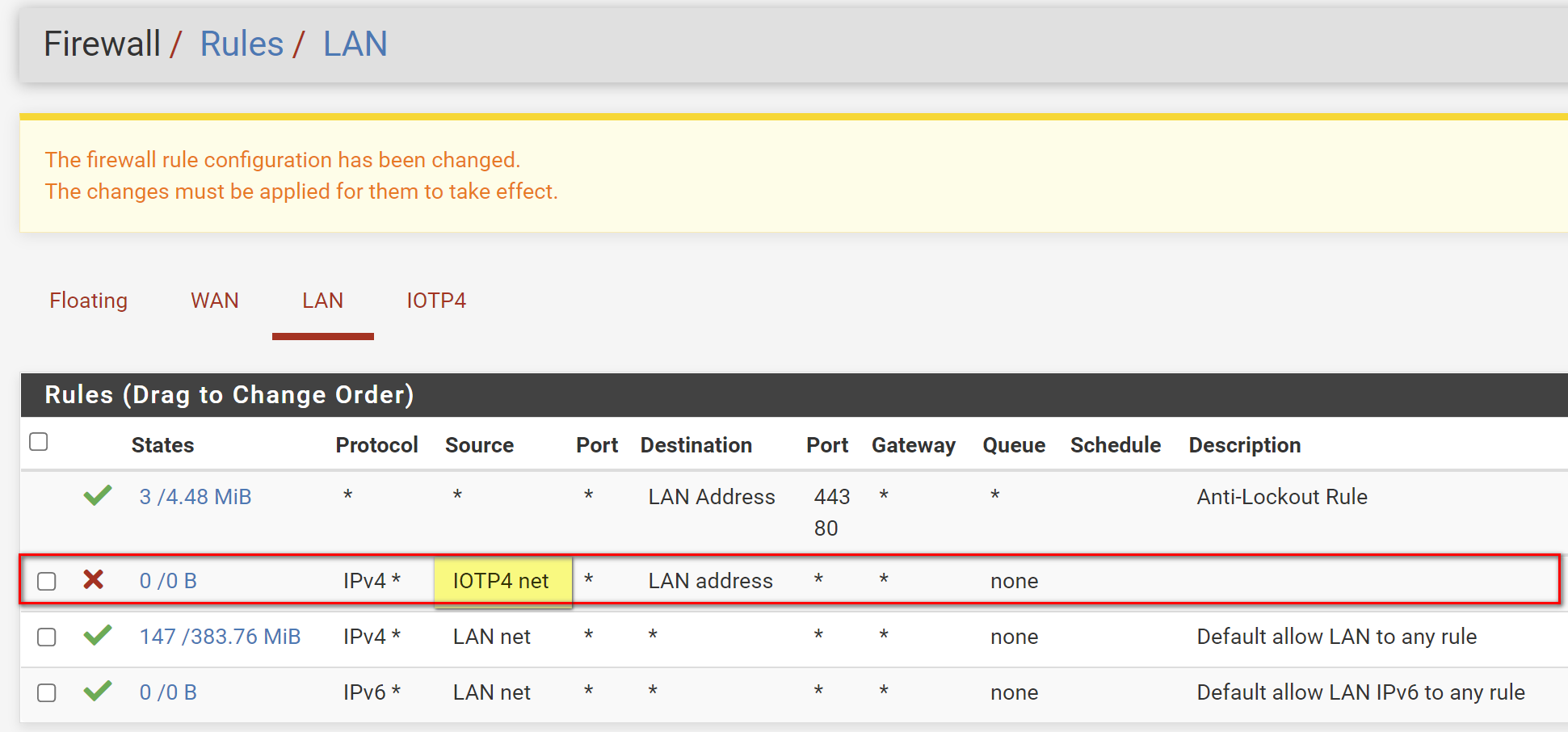
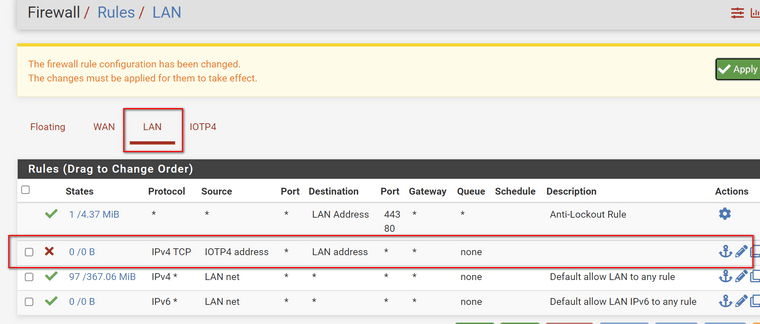
@rcoleman-netgate on the LAN firewall (192) BLOCK IoT (172) and this must be the FIRST rule. Have I got it right? On drop down there are two options IOTP4 address and IOTP4 net - which one to select as source
Below correct?
-
@netboy That will only block HTTP and HTTPS but not Ping or DNS
Set the traffic to ANY type, not TCP.
And, as I said, IOT Network, not IOT Address :)
-
@rcoleman-netgate
Is this correct? The order ok?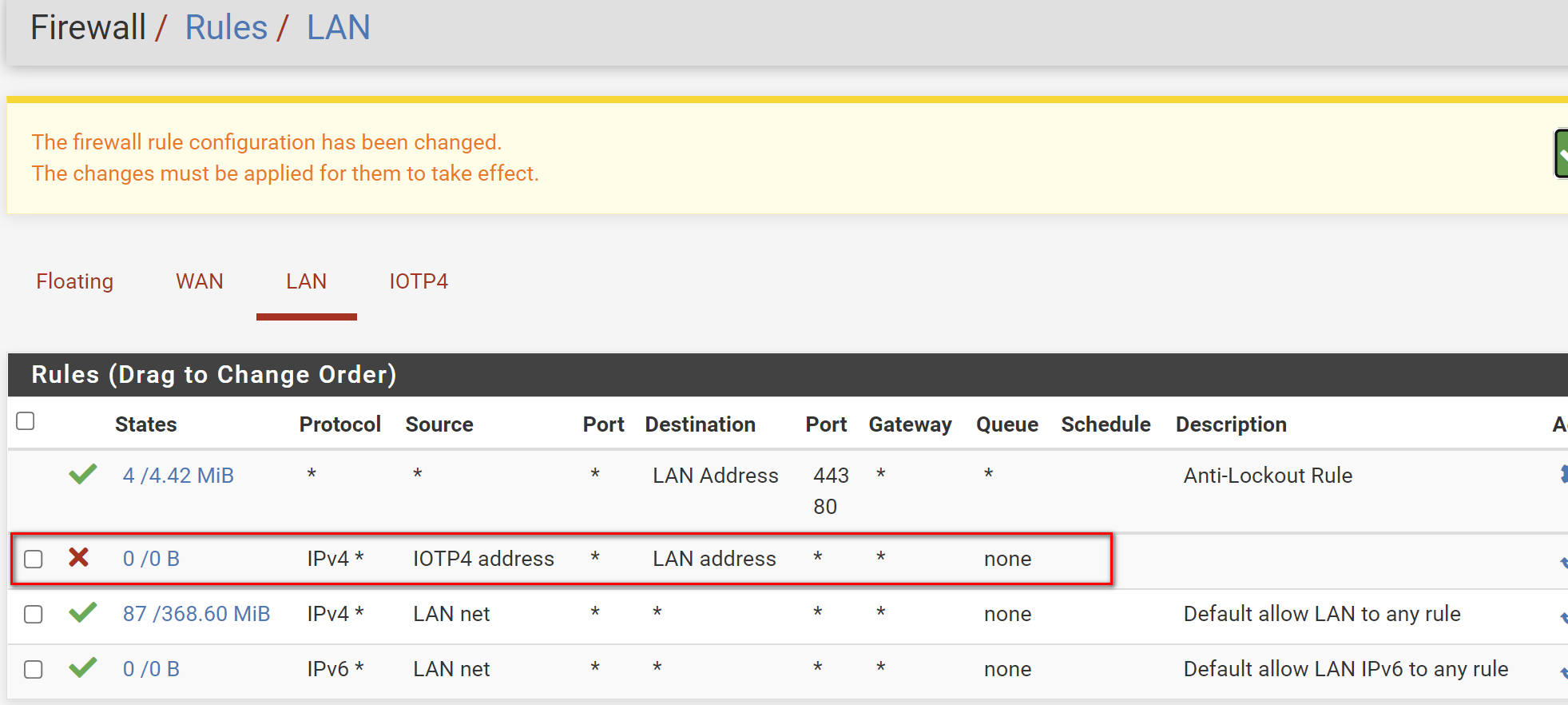
-
@netboy Needs to be IOTP4 Network, not address.
-
-
@netboy Should be. Plug into the IOTP4 network and try to access anything on the LAN network (pf GUI on that IP, ping, etc.)
it should block, and when you come back the
0 / 0 Bin the states column should increment.
-
@rcoleman-netgate Did not work - please see screen shot below
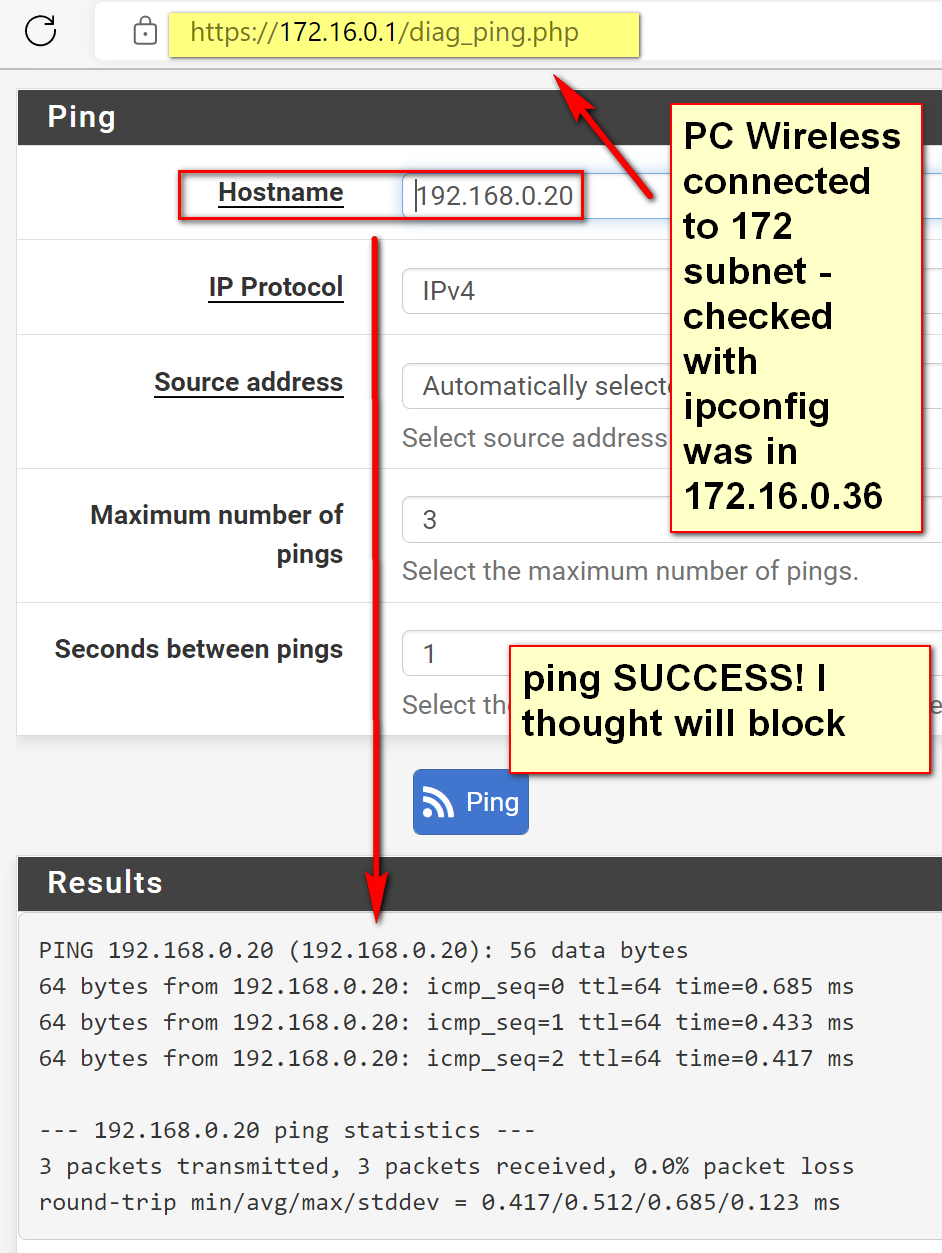
-
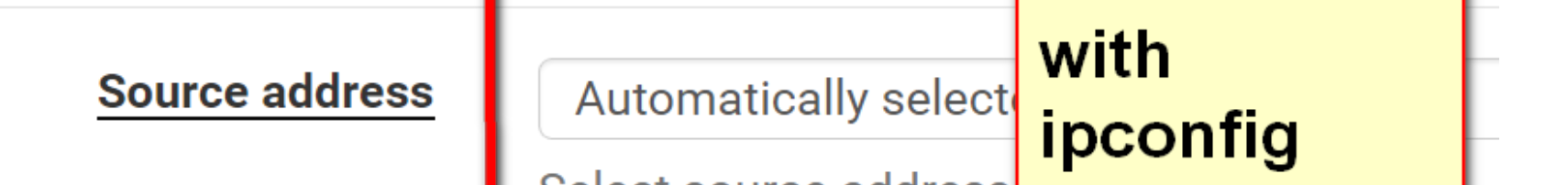
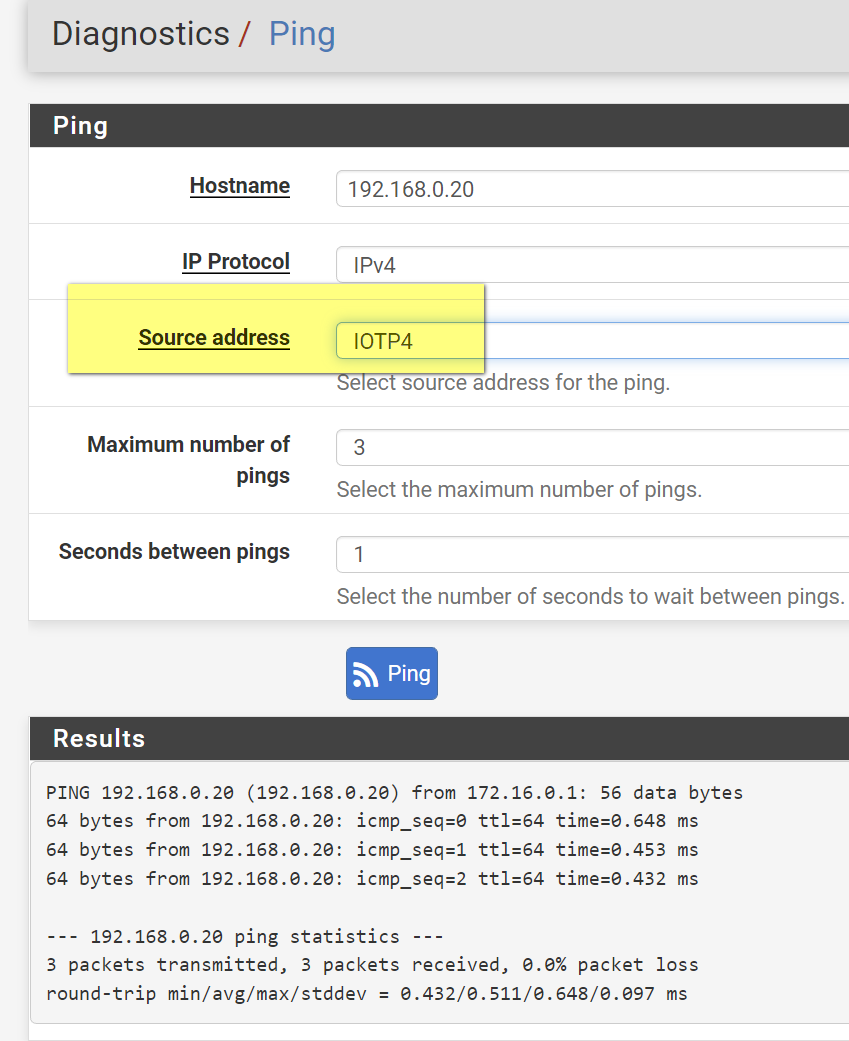
Automatically Select == use the network based on the IP you're pinging. Switch that to "IOTP4"
-
Able to ping after pointing source address to IOTP4
-
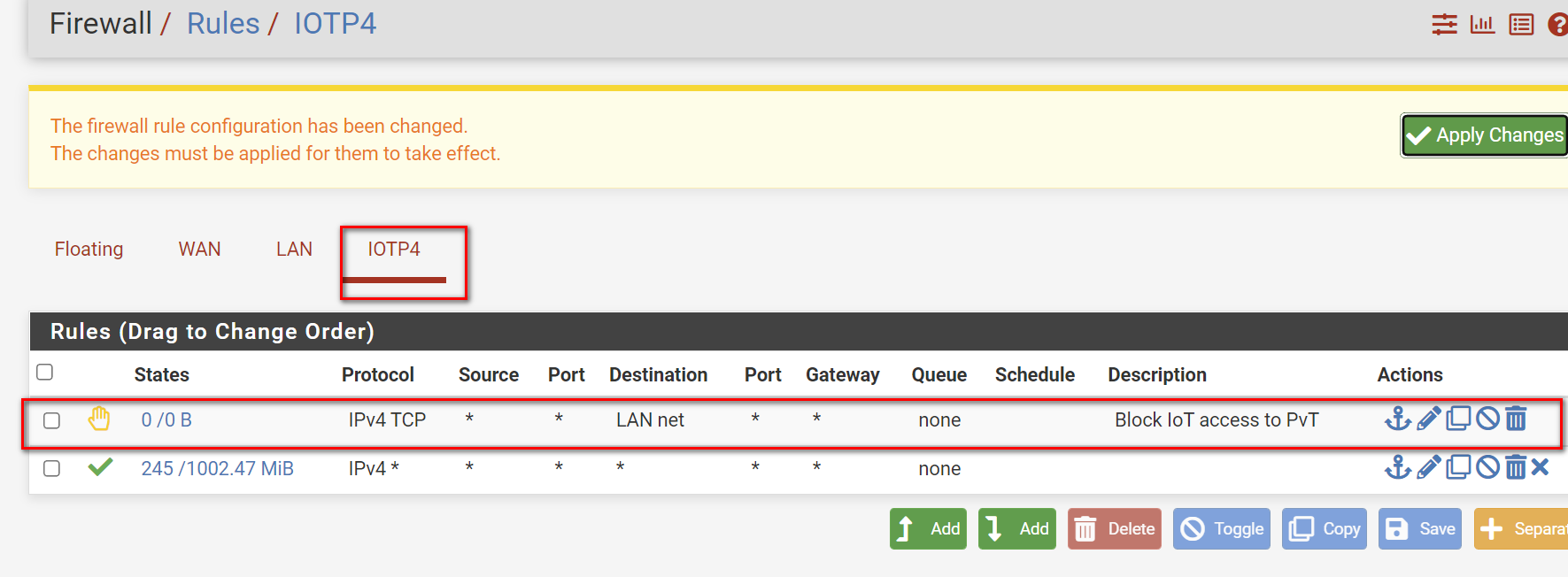
You should move that rule from the LAN interface to the IOTP4 interface.
Connections are opened from there and that's where they need to be blocked.
You probably also want the destination to be LANnet so that all hosts in the LAN subnet are blocked.
I would also choose to use a reject rule rather than block there so that clients on the IOTP4 subnet see the connection as refused imediately rather than having to timeout. It just makes failures easier to handle for devices mistakenly trying to access LAN.You need to test it from a device on the IOTP4 subnet so that the traffic goes through the IOTP4 firewall rules.
Steve
-
This post is deleted! -
-
That will work. I would set the protocol to 'any' though to include ping etc.