Newbie question
-
I've just recently started experimenting with Pfsense. I have a proxmox server which is running a few VMs (see picture) including pfsense in a VM.
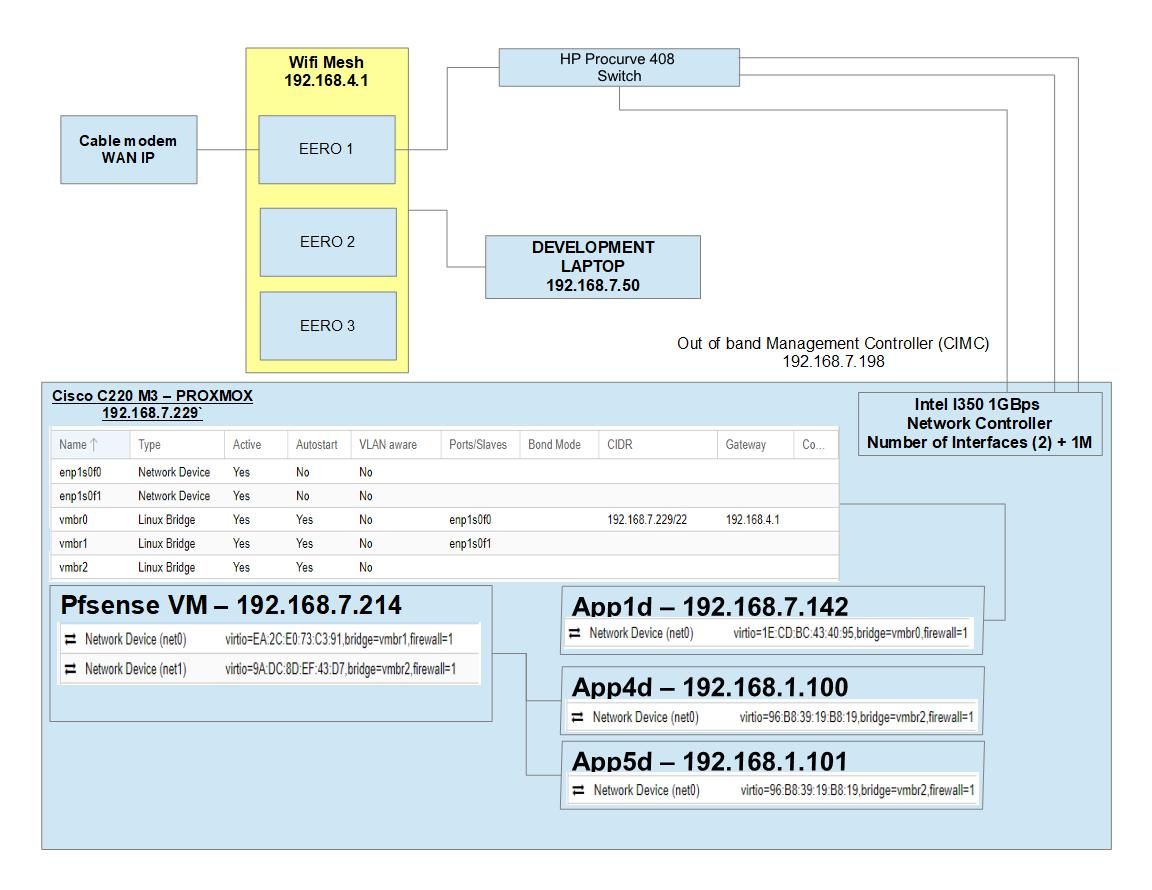
I have a couple of questions based on my observations below.
- app4d (192.168.1.100) and app5d (192.168.1.101) can ping each other using domain names - app4d.home.tdomain & app5d.home.tdomain - This works
- app4d and app5d can ping pfsense.home.tdomain (192.168.1.1)
- app1d cannot ping 192.168.7.214
- dev laptop (192.168.7.50) cannot ping 192.168.7.214
Is it possible to expose the pfsense DNS resolver externally so that app1d / dev laptop can interface with app4d / app5d using FQDN? If not, is it possible to setup certain routes for traffic to flow from the 192.168.7.x network to the 192.168.1.x network? Is this even a valid scenario I'm trying to solve??
Thanks in Advance!
-
@srikanthkaushik If pfSense is directly connected to those networks there is no need for custom routing. However all interfaces (except LAN) default to no firewall rules...so all traffic is blocked. Sounds like you need to add rules to each interface to allow traffic to the 192.168.1.1 network, and to the pfSense interface IP port 53 (TCP+UDP) for DNS.
Pinging or any connection on the same network doesn't go through pfSense.
-
@steveits Thank you. I will continue digging into the configurations to see where I'm going wrong.
-
Hi,
One reco regarding your pfSense VM settings in Proxmox : I'd recommend disabling the Proxmox firewall from this VM's interfaces, as it might interfere with the rules you'll set in pfsense.
For instance, if you allow some traffic on the pfSense interface, but did not also allow it on the proxmox firewall for the VM, then you might run into trouble.
As pfSense is a firewall, there's no point in enabling Proxmox's filtering on top of it

In addition, if the 192.168.7.214 interface is the "outside" (WAN) interface of you firewall, all incoming traffic is discarded by default, you'll have to define explicit rules allowing ICMP for instance for your tests.