Static route VS firewall rule
-
I can't find any information in the Netgear documentation that will tell me for sure if a static route is needed through a VPN tunnel, or if I only need a firewall rule with a certain gateway set. Basically, does a static route overrule a firewall rule? Is it an allow all rule to the destiantion network?
I have a fully functioning wireguard interface that I am able to reach through, IF the static route is defined, and the tunnel interface has a allow rule for the destination im wanting to get to.
I want to limit the devices on my local LAN that can reach through this tunnel. At the moment, the only way I can reach through at all is if I have the static route set. If I try to disable the static routes and just create firewall rules with a gateway through the wireguard tunnel, I cant reach through.
@cmcdonald I followed your site to site video. One thing that an inexperienced person (like myself) would miss and wasnt pointed out in the video, is that you cant have two identical private subnets on both sides of the tunnel and expect a route to work. But I figured that out.
-
I can't find any information in the Netgear documentation
A Typo? Netgear and Netgate.
Set up a route on both sites to make parts of the network reachable is one thing, but the rules on pending what traffic
is exactly allowed should be also matching to this routes. -
Yes, sorry, that was a typo. I meant netgate. So I would think that adding a static route would not automatically allow all the traffic to go over that route, but it seemed to me like that's the case here. In my mind it makes sense that a firewall rule is needed as well. So what could be wrong here?
-
@nick-wollman said in Static route VS firewall rule:
So I would think that adding a static route would not automatically allow all the traffic to go over that route, but it seemed to me like that's the case here.
All matching traffic on a static route should use that route. A common example of one you didn't know you add is when you put a monitoring IP on a gateway -- then all the traffic to that IP (typically a DNS server because they're snappy to respond) will go through that gateway.
-
By "all traffic matching that route", is that true without any firewall rule that specifies that gateway?
In my case, without the static route, no firewall rule will get traffic to that destination, even if the gateway is specified in that rule.
-
@nick-wollman Static routes are made when you create and establish a VPN a static route is made to support that VPN. That is traffic that routes without the aid of a firewall rule specifying a gateway.
-
Ok, in my case i am doing a site to site vpn. I want certain devices here, to be able to reach over there. As soon as i define a static route, ALL my devices here can reach over there. How do I control that?
And what is the gateway option for in a firewall rule?
-
@nick-wollman You have a few options...
- Put those in their own block and pass that block through the site-to-site
- Dictate their IPs as part of the site-to-site
- make a rule that pushes those source IPs (as a host alias) through with a custom gateway.
You may need to have Outbound NAT set as well.
@nick-wollman said in Static route VS firewall rule:
And what is the gateway option for in a firewall rule?
Under Advanced at the bottom of the rule.
-
Thanks for the reply.
1-2. OK this is actually a viable option to specify the allowed IPs in the tunnel. Or segregate the devices and allow only them in the tunnel.
- OK this is what I thought would be the best way to do it, but what I’m saying is that this doesn’t work. If I understand correctly, I should make a Firewall Rule that specifies a custom gateway in the advanced settings of that firewall rule. I have tried to do this, but it doesn’t work. No traffic matches that rule. And it does not work without a static route. In fact, it doesn’t work at all.
-
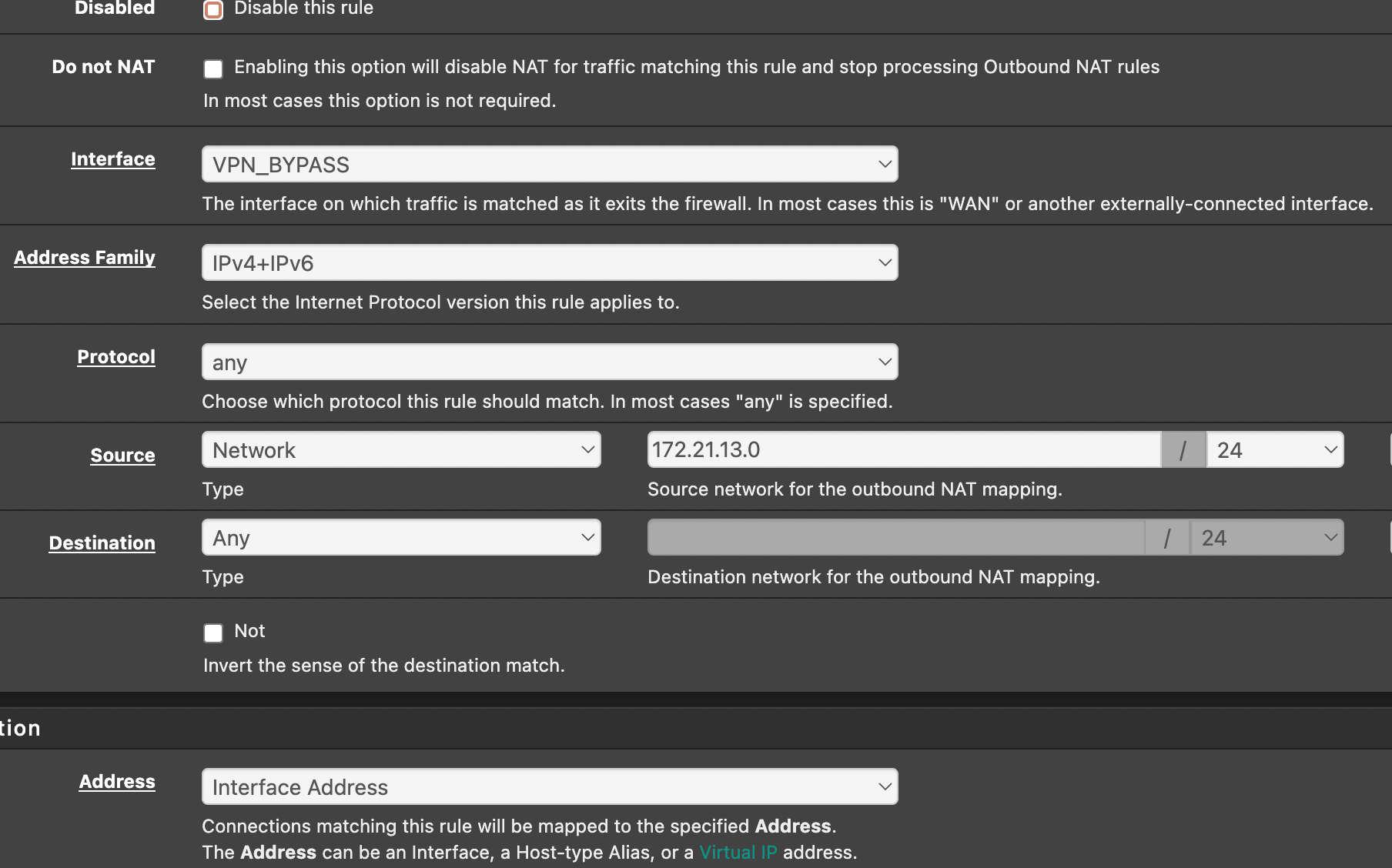
@nick-wollman Are you passing the alias in Outbound NAT, too?
Set Source to Network and enter your hosts alias.
-
@rcoleman-netgate said in Static route VS firewall rule:
@nick-wollman said in Static route VS firewall rule:
So I would think that adding a static route would not automatically allow all the traffic to go over that route, but it seemed to me like that's the case here.
All matching traffic on a static route should use that route. A common example of one you didn't know you add is when you put a monitoring IP on a gateway -- then all the traffic to that IP (typically a DNS server because they're snappy to respond) will go through that gateway.
BTW this seems like weird behavior. All traffic for that monitor IP will use that gateway? Why?
-
Well, I followed the WireGuard site to site tunnel video, and in there it said, to not specify an upstream gateway, so I don’t have to use NAT. Currently, if I reach a device on the other side of the tunnel, it is seeing my actual IP on my LAN here, exactly how Christian McDonald did it.
No good?
-
@nick-wollman Do what Christian tells you to.
-
Ok. I did. And now I post here, because the static route is too permissive, and restrictive firewall rule doesn’t work.
Can anyone help?