Allowing Internet for (V)LAN, Advice for DHCP IPv6
-
I want the same kind of rule style that the WAN interface does where everything is blocked unless explicitly allowed, but checking online the common consensus for allowing a interface access to the internet is block firewall management, allow DNS, then block private address spaces in that order before adding a allow any to any rule.
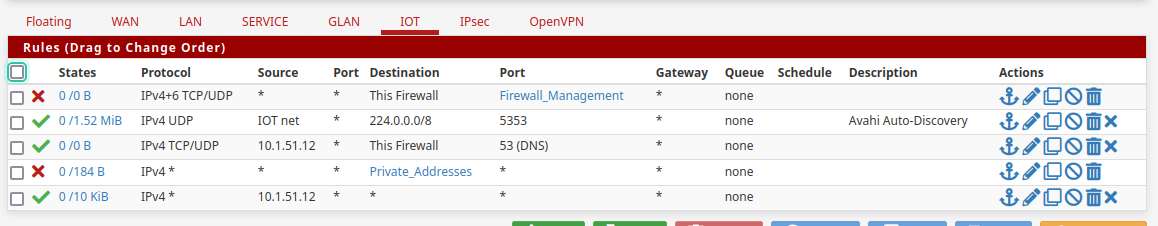
This case I'm doing that but for a specific host at the moment, but I might do something similar for other networks so anything I learn here will apply elsewhere. IPv6 is configured for the LAN but I'd like to enable it for other interfaces. Mostly as a personal goal to push as hard as I can for IPv6.Unlike my home ISP, the shop I'm working for has native IPv6 from the ISP and changing the DHCP6 settings I get some prefixes to use. I enabled IPv6 on some interfaces, track the WAN, and gave each a prefix ID but now I'd like to support IPv6 for these restricted locations so it would rationally mean adding a network to
Private_Addresses.However the IPv6 prefix is DHCP assigned!
So if the assignment changes,
Private_Addressesis out-of-date and suddenly these restricted devices have access to networks they should not have access to!Any suggestions to:
- Allow internet access only from certain networks, and
- Blocking cross-network IPv6 with the prefix DHCP assigned.
-
@jarrodsfarrell One thing you can do is: do a block rule for every other network you have, like block IPsec_net on IOT etc.
One other thing you can try is to put the gateway for IPv6 in a broader IPv6 internet rule.As a side note, your first rule is only blocking the management port of pfSense. I think it is better to block any port on your firewall unless needed. So first make the allowed connection to the firewall and then block everything else to the firewall.
-
@bob-dig I thought of doing that, but then whenever I want to add a new VLAN or interface I'd have to go to each of the tabs to block the new interface if I don't want access. It would just add linear administrative overhead.
But making an alias for the gateway might be a good idea. It's less likely to change and will fail to a secure state of just losing internet access instead of suddenly giving access.
Alternatively I can ask for a static IP and prefix from the ISP which will be a first for me.
I will also add and change the rule for the firewall; it was something I quickly bodged together from gut instinct since I had to fix something related to that device and didn't want to leave the door open as it were.
-
@jarrodsfarrell said in Allowing Internet for (V)LAN, Advice for DHCP IPv6:
But making an alias for the gateway might be a good idea.
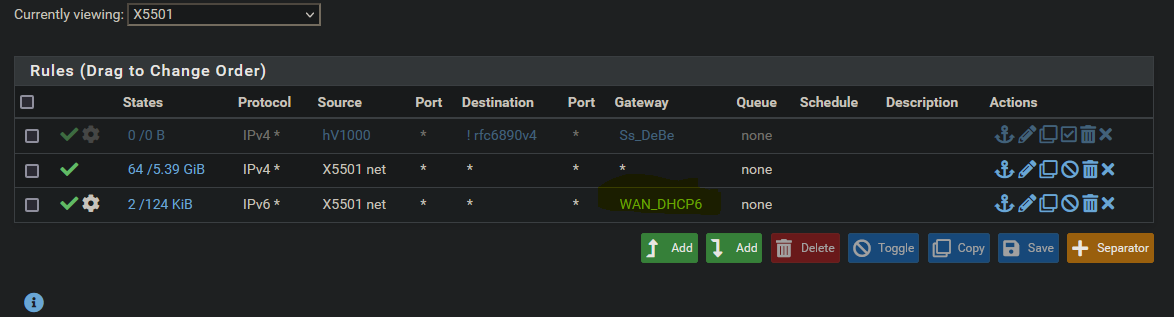
I meant like this, at least for me, I can not touch any internal subnets over IPv6 with that rule.
-
@jarrodsfarrell said in Allowing Internet for (V)LAN, Advice for DHCP IPv6:
IPv6 is configured for the LAN but I'd like to enable it for other interfaces.
How big is the prefix you get from the ISP? You just have to use a unique prefix ID for each interface. Also, you don't want to use DHCPv6 if you don't need it. SLAAC & RDDNS should provide all you need. If you need more, you can enable stateless DHCPv6.
BTW, Android devices won't work with DHCPv6.
-
@bob-dig Ended up being too low energy and busy to do it sooner, but I didn't think to check the advanced options; lot of the rules I've made (which isn't saying much) was without touching the advanced options.
But I did correct my rules though and even made an alias so permitting another device is just as easy as adding an IP to said alias.
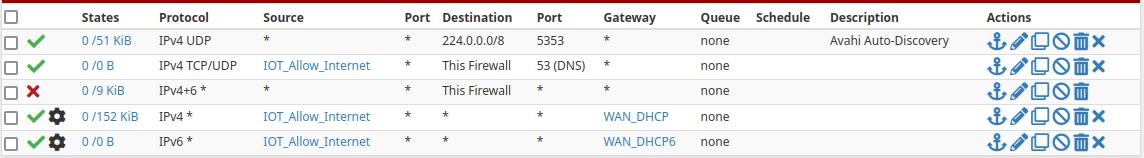
I did remove the RFC1918 rule since it's redundant; if it's not getting routed out to the gateway then it's definitely not local. Overall I'm happy how it looks and it solves both issues I mentioned in the OP.- Allow internet access only from certain networks, and
- Blocking cross-network IPv6 with the prefix DHCP assigned.
While also having the same level of security on the WAN side where you want to explicitly allow something instead of allow any-to-any.
@jknott said in Allowing Internet for (V)LAN, Advice for DHCP IPv6:
How big is the prefix you get from the ISP? You just have to use a unique prefix ID for each interface.
Comcast Business is letting me upto a generous /48 but I'm being kind and requesting a /56 prefix since it's sufficient; enough for me to use the relevant VLAN tag as a crude prefix ID.
Also, you don't want to use DHCPv6 if you don't need it. SLAAC & RDDNS should provide all you need. If you need more, you can enable stateless DHCPv6.
BTW, Android devices won't work with DHCPv6.
I'll enable stateless DHCPv6, since I don't have a reason to not have it. But thanks for the Android mention.
Edit: For clarification I don't have a whole lot of experience with IPv6 as I do with IPv4 and admittedly the macro-level of IPv6 has left me confused at times. I know enough to administer rules and treat it as IPv4 but bigger. However I still want to support it on principle.
-
@jarrodsfarrell Did fix the DNS IPv4+6. Post filter is getting tripped so I can't edit my post.