Routing Wireguard Clients via VPN Gateway.
-
Wasn't sure of the best category for this as it covers a few areas...
Ok, so I currently have a Wireguard server set up in PfSense which allows me to access my home network as well as use my home internet connection while away from home using my phone and/or laptop. All runs fine.
I also run 2 OpenVPN and 1 Wireguard Client, all connected to NordVPN in a Gateway Group (WG being Tier 1 and OpenVPN being Tier 2). I have an Alias list set up for clients that I want to use this Gateway group as well as rules on each interface to route this Alias list via the Nord Gateway group. All runs fine.
What I would like to set up, is when connecting to my home network via Wireguard, instead of just using my Home internet connection, I'd like to route the traffic from my phone also via the Nord Gateway Group. In this way I get the best of both worlds, access to my home network, but also internet access via Nord, all through a single VPN connection.
I had assumed this would just be as easy as adding my Phone's Wireguard IP address to the Alias list and add the same rules to the WG0 tab the same way as I do on any other interface. Unfortunately, after having tried this, my Phone still appears to be connecting to the internet via the Default Gateway.
Has anybody done anything similar? Any ideas where to begin diagnosing my issue? Thanks in advance :)
-
@neodude You need to do the outbound NAT on the OpenVPNs clients now for the WG Subnet too.
-
If your policy routing rule on the Wireguard interface is correct I would expect that to work. Make sure it's actually matching the traffic there and not on some other rule.
Steve
-
Managed to get this running. I noticed that I also had a "Wireguard" Tab under firewall rules. I moved my rules from "WG0" to "Wireguard" and everything works perfectly. Still confused as to why there are 2 tabs though. '"WG0" shows in Interface Assignments but "Wireguard" does not.
-
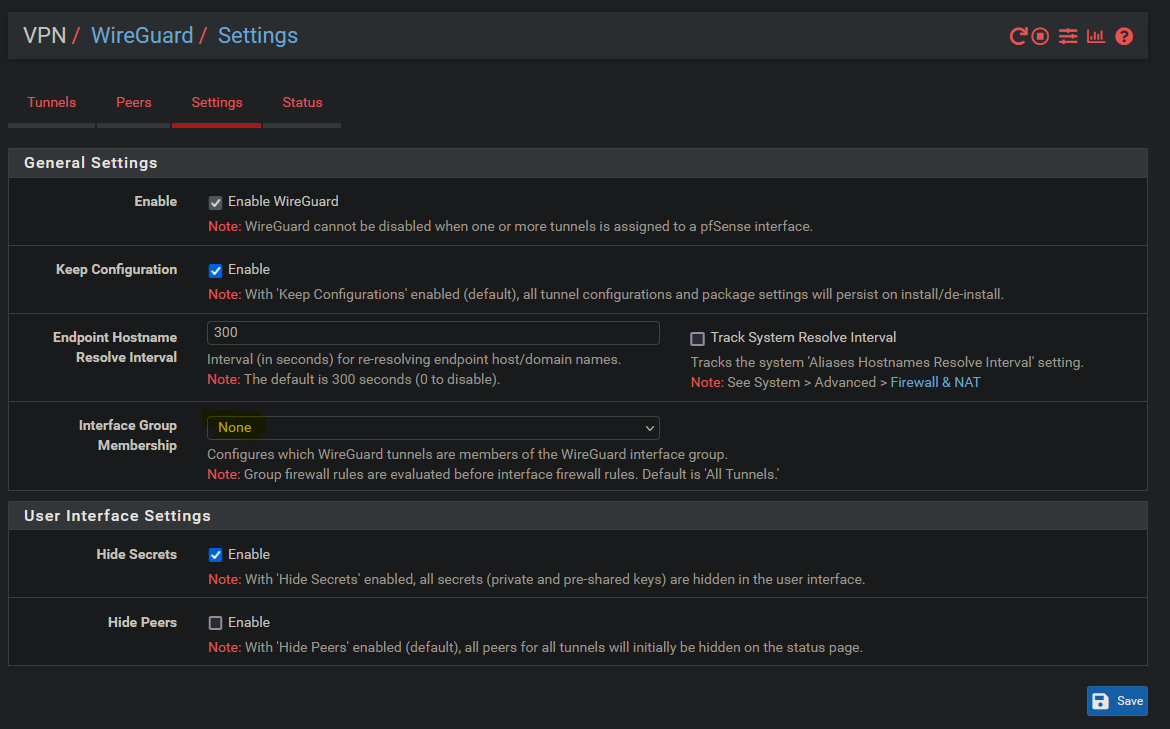
'Wireguard' is an interface group. WG0 is a member of that group. Firewall rules on interface groups are parsed first.
Steve
-
Yep, I see it now in interface groups. Is this created automatically when a Wireguard interface is created? It doesn't show as having WG0 as a member, despite acting like it does.
-
@stephenw10 said in Routing Wireguard Clients via VPN Gateway.:
WG0 is a member of that group.
Not necessarily

@NeoDude For OpenVPN there is also a group, since forever.
-
Yes, that^. It's not quite the same as a user created interface group but, yes, it is created automatically and, yes, all Wireguard tunnels are always a member of that.
https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/rules.html#tunneled-traffic
Steve
-
@stephenw10 said in Routing Wireguard Clients via VPN Gateway.:
and, yes, all Wireguard tunnels are always a member of that.
Wait a minute...
-
Huh, interesting I missed that.
