From WAN to LAN issue
-
Hello,
I'm using pfSense since some time and I've never been doing anything very specific... until lately. :-)
I would say that I have a basic understanding of networking.Context:
I'm using pfSense 2.5.1 and I have 2 interfaces configured, one LAN (10.10.1.x/24) and one WAN (192.168.1.x/24). Actually the WAN is rather a LAN but ok... :-)
And pfSense is between WAN and LAN.Here is how the network looks like:
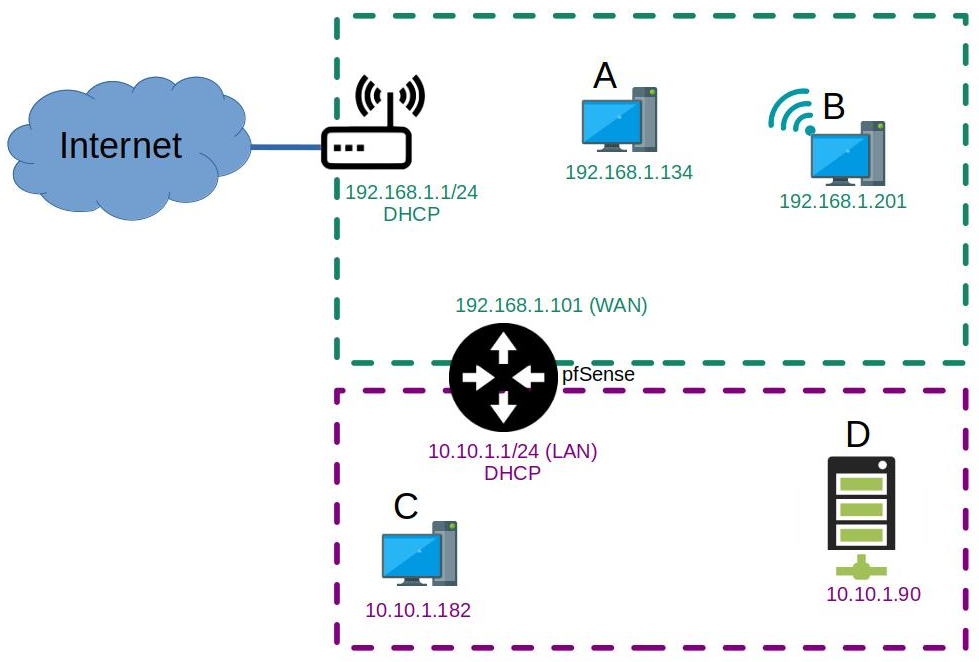
I have a modem that provides connection to the internet and acts as a DHCP server on the WAN (what I call WAN from pfSense's perspective), and as well as a gateway to internet on the address 192.168.1.x/24,
On that network I have one of pfSense's interface (WAN) at 192.168.1.101.Then I have a second network (LAN) on 10.10.1.x/24 where pfSense acts as a DHCP server (with the LAN address 10.10.1.1) and as a gateway for this network.
All works fine, the WAN network can not access to the LAN network but has access to internet through the modem.
The LAN network can reach the WAN network and also internet.Issue:
Now I would like the computer B on the WAN to be able to reach server D on the LAN (note that B is connected on the wifi of the modem but I don't think that is an issue).So I gave B a static IP, with the gateway address on 192.168.1.101 and I thought I would use a NAT rule to send connections from B to D.
Here is the rule in pfSense:
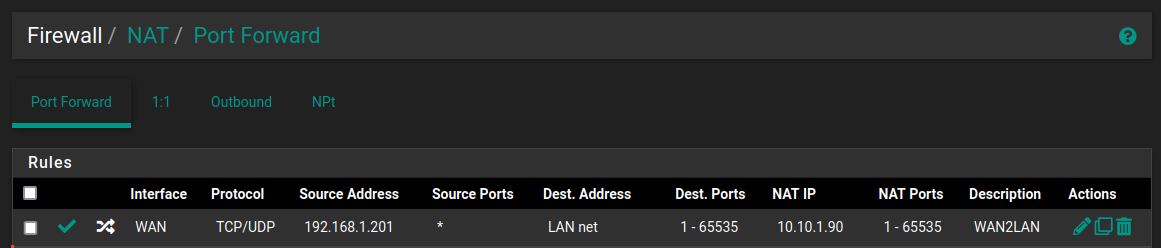
In the destination address I tried several options (single host, LAN net, LAN address) none of them worked.Question:
I'm getting a bit lost here.- Not sure I have to use NAT?
- And not sure how to get it to work because I don't understand where it is blocking.
When I disable the firewall, it works (I can ping D from B), so it is hanging somewhere there. - Am I missing something obvious here?
I suspect I'm missing something in the understanding of how pfSense is working (and networking or firewalls in general)?
Thanks for your feedback...
-
@plypo if you want a device on your 192 network to get to stuff behind pfsense then you need to do a port forward.
And you wouldn't change the gateway of this device on the wan, it would still point to your wifi router as its gateway.
If you want B to access D.. Then B would hit the pfsense wan IP 192.168.1.101 on the port you forward to 10.10.1.90 on the port your trying to access.
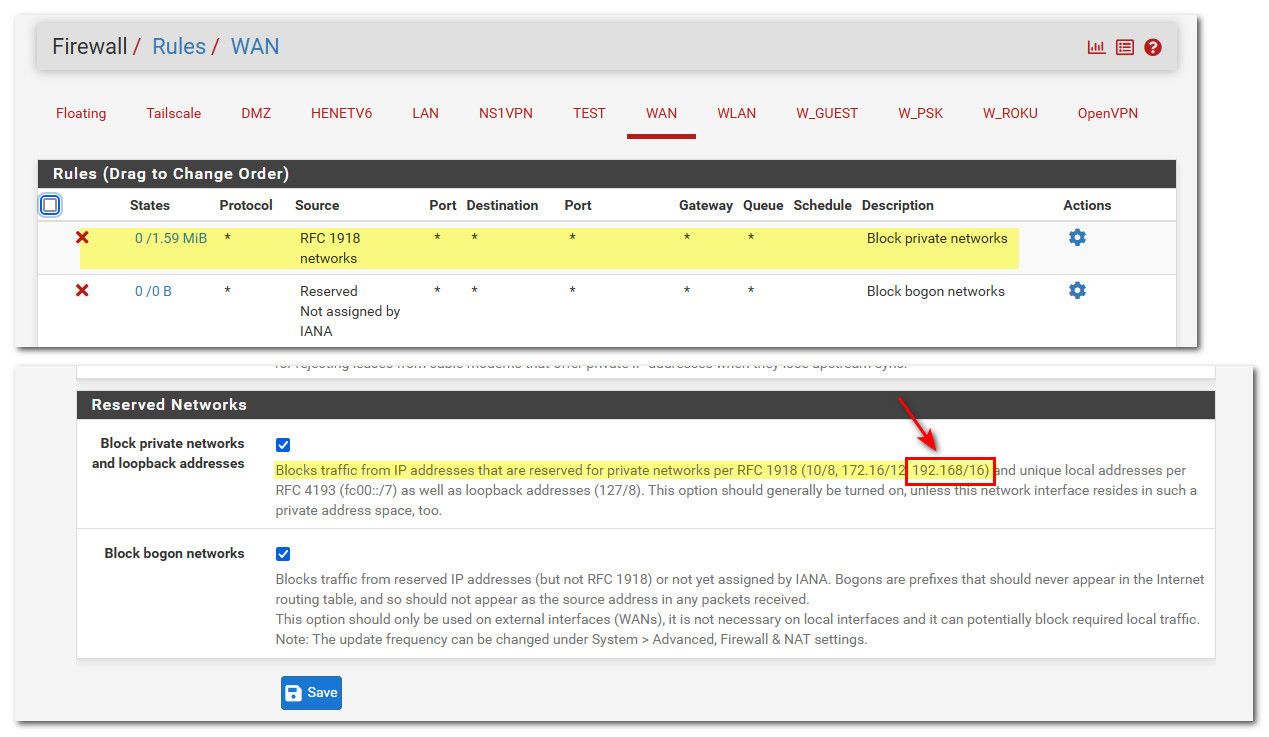
BTW on your pfsense the default block rfc1918 would have to be disabled. Or no 192.168 is never going to get to anything behind pfsense because the wan rule of blocking rfc1918 would always block that traffic no matter what port forward you setup.
Curious why don't you replace your wifi router with pfsense, and then just your wifi router as AP on whatever network you want behind pfsense.
-
Thank you for the answer.
I thought, since I'm in the "port forward" section of the NAT configuration, that in the configuration I made (see screenshot in previous post), I already do port forward (of all ports 1-65535, that was the lazy option to test first since I don't know exactly which ports I need)?
As source I have the WAN computer (B) and as destination the LAN computer (D).
In the port forward configuration, what I don't quite understand is the difference between "Destination" and "Redirect target IP"? I tried several combinations with no success.@johnpoz said in From WAN to LAN issue:
the default block rfc1918 would have to be disabled
Thanks for the hint, I had seen the option in the WAN interface but wasn't sure what it was about. I unchecked "Block bogon networks", but it didn't change a thing.
@johnpoz said in From WAN to LAN issue:
Curious why don't you replace your wifi router with pfsense
The wifi router is the ADSL modem and I need it to get the internet connection, so I can't really bypass it.
-
@plypo said in From WAN to LAN issue:
As source I have the WAN computer (B) and as destination the LAN computer (D).
In the port forward configuration, what I don't quite understand is the difference between "Destination" and "Redirect target IP"? I tried several combinations with no success.WAN and LAN are separated. The computer B cannot access devices on the LAN directly, because he has no route to the network. B can just access the WAN IP of pfSense. So he has to send the packets to the WAN IP and you have to forward them on pfSense.
Hence the origin destination of the packets is the "WAN address". So you must use this one at destination in the NAT rule. The redirect target is the IP, where the packets should get forwarded, i.e. the IP of D.
Hint: You can assign additional virtual IPs to the WAN interface, which can be used as destination in NAT rules, so you are able to forward the same port numbers to different hosts on the LAN.
-
@plypo said in From WAN to LAN issue:
I unchecked "Block bogon networks"
When did I mention bogon??
Forwarding all ports is not the way to do it either. You don't know what service you want to access on this server?
-
@viragomann Thanks for the feedback.
Do I understand it right that the NAT configuration should look like:- Source address would be 192.168.1.201
- Destination address would be 192.168.1.101
- NAT IP would be 10.10.1.90
@johnpoz said in From WAN to LAN issue:
When did I mention bogon??
Oh right, yes, sorry my bad, I was a bit too eager! :-O
I assumed since "Block private networks and loopback addresses" was not checked and "Block bogon networks" was... and I didn´t read carefully!About all ports forwarding, a bit more on the context: I'm using a micro controller to send some data over wifi to the server (D) and I am not sure which port it is using exactly so for simplicity (and to try it out first) I selected all ports.
Thanks for your feedback, I'll have to look deeper in to this topic.
But I feel I'm missing some understanding here on NAT and routing between two networks. Would you have some pointers for me? Any documentation I can look into to get a better understanding (instead of trying poking around... :-P)? -
@plypo said in From WAN to LAN issue:
Do I understand it right that the NAT configuration should look like:
Source address would be 192.168.1.201
Destination address would be 192.168.1.101
NAT IP would be 10.10.1.90Yes.
But as @johnpoz mentioned, you should also restrict the rule to the ports you really need. -
@plypo Since your doing this rfc1918 to rfc1918 you could do it without a port forward because you don't need a nat. But you would need to create a route on the 192.168 device.
And then allow the traffic just on the wan interface via a rule, no nat or port forward needed.
And you would have to setup a no nat outbound rule so that when devices on your 10 network are talking to your 192. network they don't nat..
I would never in a million years set it up like this.. I would turn your isp device into just a modem, turn off its wifi and get a real AP for my local wifi. And put everything behind pfsense. Worse case just turn off wifi on your isp device and just double nat, etc.
But there are few different ways to skin this cat. One being your typical port forward scenario, the other is just setting up routes on your devices in 192.168 to point to pfsense wan IP to get to the 10 network. And allowing via wan firewall rules, and disable nat outbound on pfsense when talking to anything other than your 192.168.1.1 gateway.