New COD MWII Blocked By pfSense
-
@johnpoz said in New COD MWII Blocked By pfSense:
You most likely filled up your sniff before you even started anything because you didn't change the limit from 100 to 0
right, i forgot to change the 'count' to 0. changed it now and running another pcap while trying to connect to COD..
-
@emjeezy make sure you flushed the clients local dns cache as well - so we can see if any dns queries it asks for are not being answered.
-
copy. will do.
-
@johnpoz So fighting the pcap size, too large to upload here. Set count to a thousand packets and ran. Hopefully it captured some useful traffic. updated pcap attached.
-
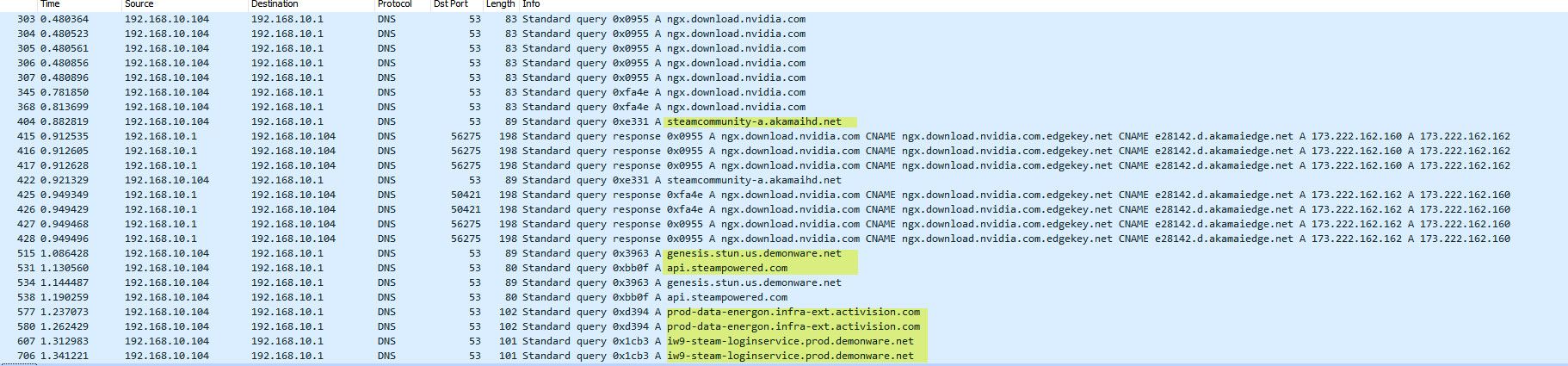
@emjeezy well can see no dns responses for stuff being asked for
-
@johnpoz humm..yah thats my machine asking my firewall for dns..thats normal. Wonder why my firwewall would fail to answer. I have 8.8.8.8 set as primary and 9.9.9.9 as 2ndary dns server.
-
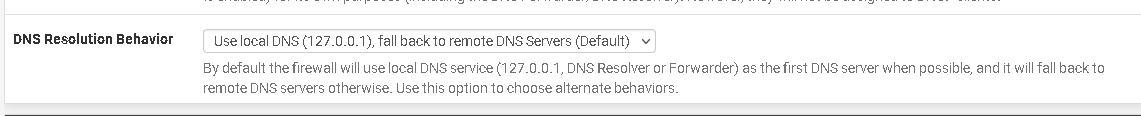
@emjeezy What is DNS Resolver set up for?
And System->General for the DNS calls?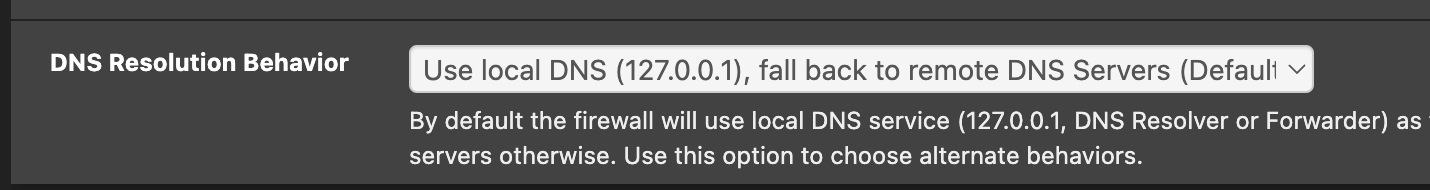
-
-
I didn't find any that didn't have a record.. From the ones that he showed no response for. I queried for them and they all responded.
But like that one with loginservice.prod in the name - if that doesn't get an answer, it highly unlikely to be able to login ;)
-
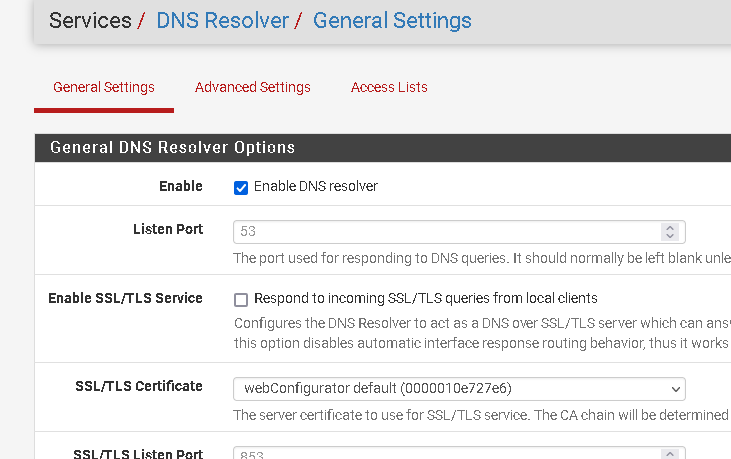
@emjeezy Is DNS resolver running? Check Status->Services
-
-
@rcoleman-netgate he got a response for the ngx nvidia one - even though did seem delayed..
But don't see any other responses - maybe they were delayed as well, and the sniff stopped before they came in? But yeah checking to make sure they do respond would be step 1 in trying to figure out what is going on.
-
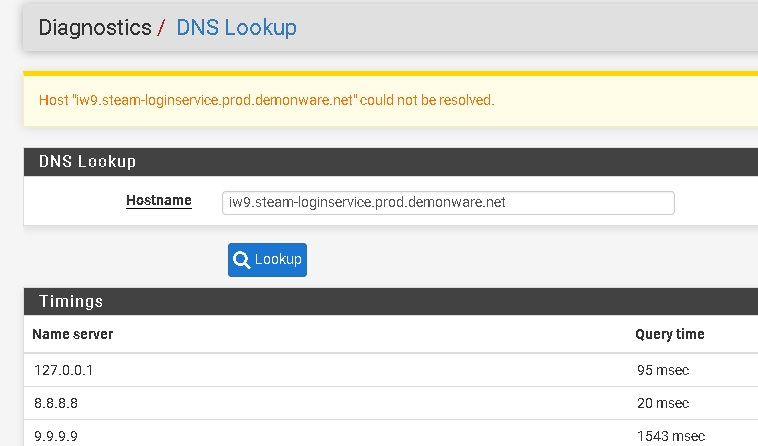
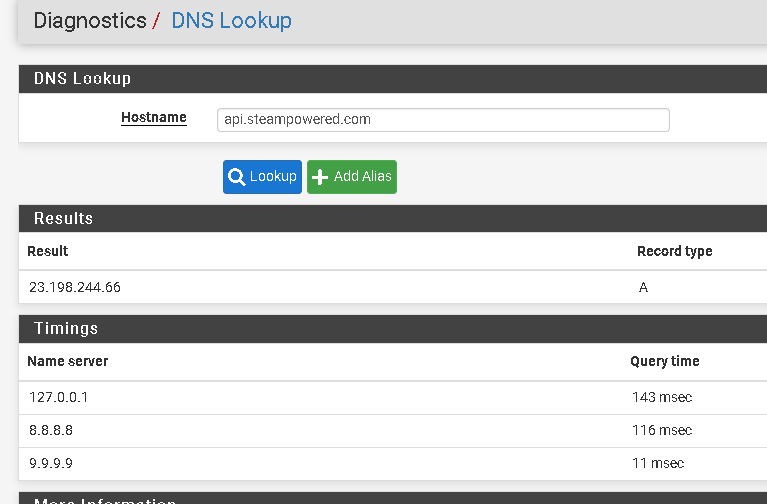
How about going to Diagnostics->DNS Lookup and running a few of those?
I couldn't get the ergeron one to resolve but I did get steampowered to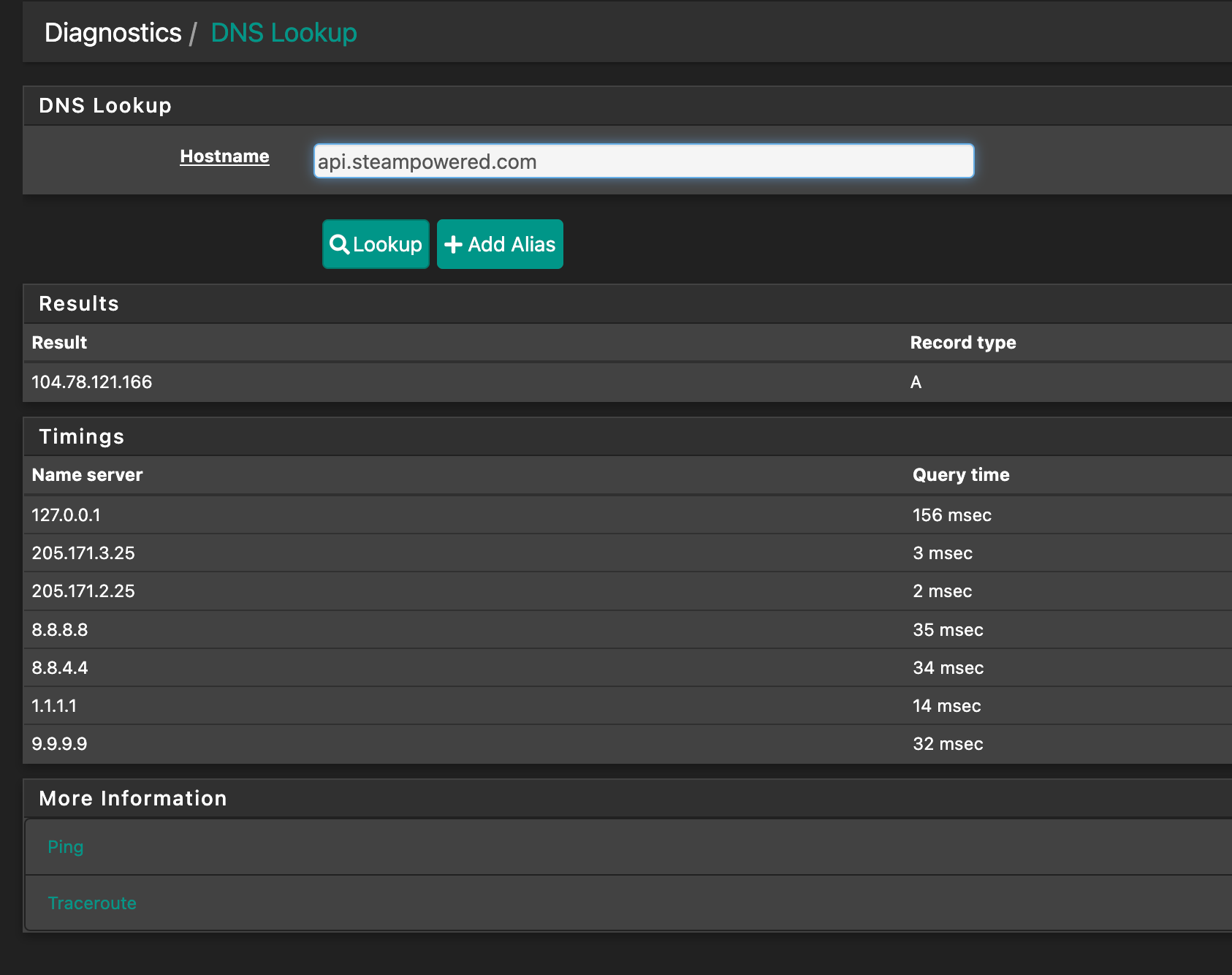
-
@johnpoz just tried to resolve this from my pc with a simple nslookup + a ping 'iw9.steam-loginservice.prod.demonware.net'..nothing.. are you able to resolve that on your end..?
-
-
Also set a static google dns on my pc, flushed dns cache and tried sigining into COD, same issue...
-
@emjeezy said in New COD MWII Blocked By pfSense:
'iw9.steam-loginservice.prod.demonware.net
Yeah no problems here
; <<>> DiG 9.18.1-1ubuntu1.2-Ubuntu <<>> iw9-steam-loginservice.prod.demonware.net @192.168.9.253 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21888 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;iw9-steam-loginservice.prod.demonware.net. IN A ;; ANSWER SECTION: iw9-steam-loginservice.prod.demonware.net. 1608 IN A 185.34.106.26 ;; Query time: 0 msec ;; SERVER: 192.168.9.253#53(192.168.9.253) (UDP) ;; WHEN: Mon Oct 31 13:27:17 CDT 2022 ;; MSG SIZE rcvd: 86Make sure you didn't typo it.. you have a . in there vs -
Do a query on pfsense directly with +trace, and could show you were its failing in resolving.
[22.05-RELEASE][admin@sg4860.local.lan]/root: dig iw9-steam-loginservice.prod.demonware.net +trace ; <<>> DiG 9.16.26 <<>> iw9-steam-loginservice.prod.demonware.net +trace ;; global options: +cmd . 59493 IN NS i.root-servers.net. . 59493 IN NS j.root-servers.net. . 59493 IN NS k.root-servers.net. . 59493 IN NS l.root-servers.net. . 59493 IN NS m.root-servers.net. . 59493 IN NS a.root-servers.net. . 59493 IN NS b.root-servers.net. . 59493 IN NS c.root-servers.net. . 59493 IN NS d.root-servers.net. . 59493 IN NS e.root-servers.net. . 59493 IN NS f.root-servers.net. . 59493 IN NS g.root-servers.net. . 59493 IN NS h.root-servers.net. . 59493 IN RRSIG NS 8 0 518400 20221113050000 20221031040000 18733 . nYRaOu1wLMKLz7qtu6iyVbQdbCptnVf2aQb2/iNS9Eh9fnKJY/4Gj14e k7kC2Mwrfi304rbrv128fD9sJ6EX26LHOXt4lYTKI0abzYHtYNwCx17d wm1MA/oiaA7C9lLj5OdF0DraMl6go2FF0F9DtNdnOksSW1AjNlAX3R7T BTRzLiDxEf0123vW4oS8vO0dCVmK+dZ72RqPycUY2cGj5m4bXrKdcfdZ c2I/dV3761SILlh9yIw/ujo3HzFe5cHT5yZ+x/cBecdO+I9/DqoOUOq9 T2Cw/olYIMG+Jghaul5/ETfSUZ8p736KTQPOiZfRsaI/LsPABlNvTZ/2 IYxPuQ== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 1 ms net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS m.gtld-servers.net. net. 172800 IN NS l.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 86400 IN DS 35886 8 2 7862B27F5F516EBE19680444D4CE5E762981931842C465F00236401D 8BD973EE net. 86400 IN RRSIG DS 8 1 86400 20221113170000 20221031160000 18733 . b2QFjzsdbjugDaHMb0z6E/Gi/21nGXkcHiyeAnDBJvyBf8Oc9O5iErBh Dm/ItjC/ZVVaI6DtqbkFuCBtW4OqD9nVMfZl1kppln7Wy1y/5PuyQAFV Xts9PyDLZYcAk10XmSe50m0FRp15NBupiNLepPYbRSSm7l866MqMmsd1 1T7Hx8Y51oqLELb5RRRkJ0kGyV8Al4yhFg9oZtimprT4KUouoKTGgMTl vWI2JeOv5MISdys6Fvc/zaViW9CTzRrR4iP2OQv9XA6T4jzyHKP94xwD QskihTM23cO08ZKOc1zD2FjGYbja3iNtlS2pjnMsm/kx7TvoXAkJF5Fk EZgTSQ== ;; Received 1204 bytes from 202.12.27.33#53(m.root-servers.net) in 61 ms demonware.net. 172800 IN NS dns3.easydns.org. demonware.net. 172800 IN NS dns1.easydns.com. demonware.net. 172800 IN NS dns2.easydns.net. demonware.net. 172800 IN NS dns4.easydns.info. A1RT98BS5QGC9NFI51S9HCI47ULJG6JH.net. 86400 IN NSEC3 1 1 0 - A1RTLNPGULOGN7B9A62SHJE1U3TTP8DR NS SOA RRSIG DNSKEY NSEC3PARAM A1RT98BS5QGC9NFI51S9HCI47ULJG6JH.net. 86400 IN RRSIG NSEC3 8 2 86400 20221107073404 20221031052404 57635 net. r5UTHe04CrX84rlUl5E5k4gB+bFPj1vBcci0HHNgHgf0mS5SZaYRmzEq aZBAM1cAvrsMaOx28mjDz10RuOvu+RE2RpfGTIELjn94ymxvZUPPRCZ6 g4RS+89e04YijkQlMw9go4/7ZKkDA3LT+LgxX+LCisYlBoS8GFKyWQfX ZVLiglsGRvAbpKUsc1oAfnZ+yYn/2g3yx1VchAqsAd7YHw== TA25FU84S76EUD659DBEH1SFOASD4VL7.net. 86400 IN NSEC3 1 1 0 - TA288SAGQ250LBG11JFBMGCLUPT84FCJ NS DS RRSIG TA25FU84S76EUD659DBEH1SFOASD4VL7.net. 86400 IN RRSIG NSEC3 8 2 86400 20221105062652 20221029051652 57635 net. W7omB+op6WqcUFXhA5Jbh/hYqAyKy+MYUbNAyh/4DJJ4QNgQLA039kbW /Jdi/DYiBG2XbzU4kVDrTNL/7HamJ+FvtH0YqewH5HuZcF4DqQ9822/K EO9PsrMeXEHh7VuFRf4rKxn72EY9tGLzj4jKN5yM+YQUjY2Yczl62alQ JPThd8cT4y9Iks7s+eF/E5UOaq805OSm0SnaM1NisGSjIA== ;; Received 781 bytes from 2001:503:eea3::30#53(g.gtld-servers.net) in 50 ms iw9-steam-loginservice.prod.demonware.net. 300 IN A 185.34.106.26 ;; Received 114 bytes from 2620:49:3::10#53(dns3.easydns.org) in 200 ms [22.05-RELEASE][admin@sg4860.local.lan]/root: -
Ok, my pfsense is resolving it successfully. My fault for having that '.' in there on the domain ->
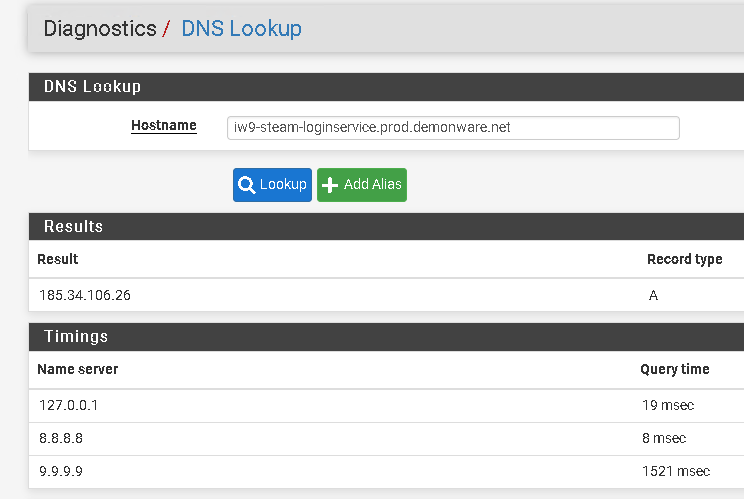
-
So check this out. Hit the firewall log to check for blocks (status>system logs>firewall). First cleared the firewall so i could start with a fresh empty log. Fired up COD and started banging at the 'retry' connection/login button ->
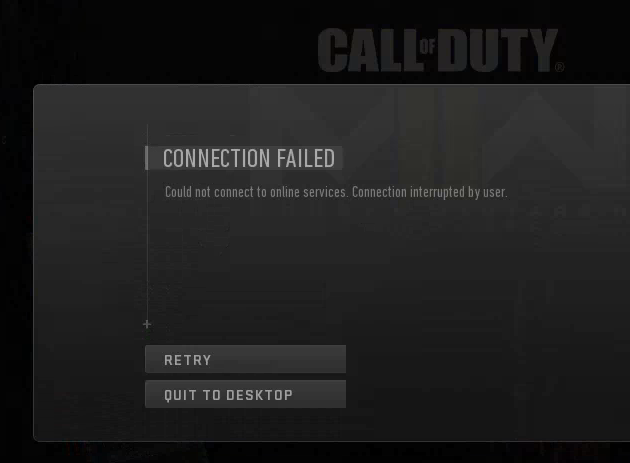
Refreshed firewall log. Right away I can see some unexpected related blocks on 3075 ->
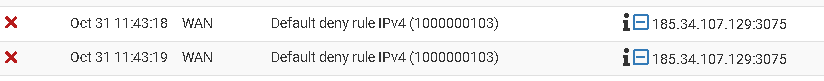
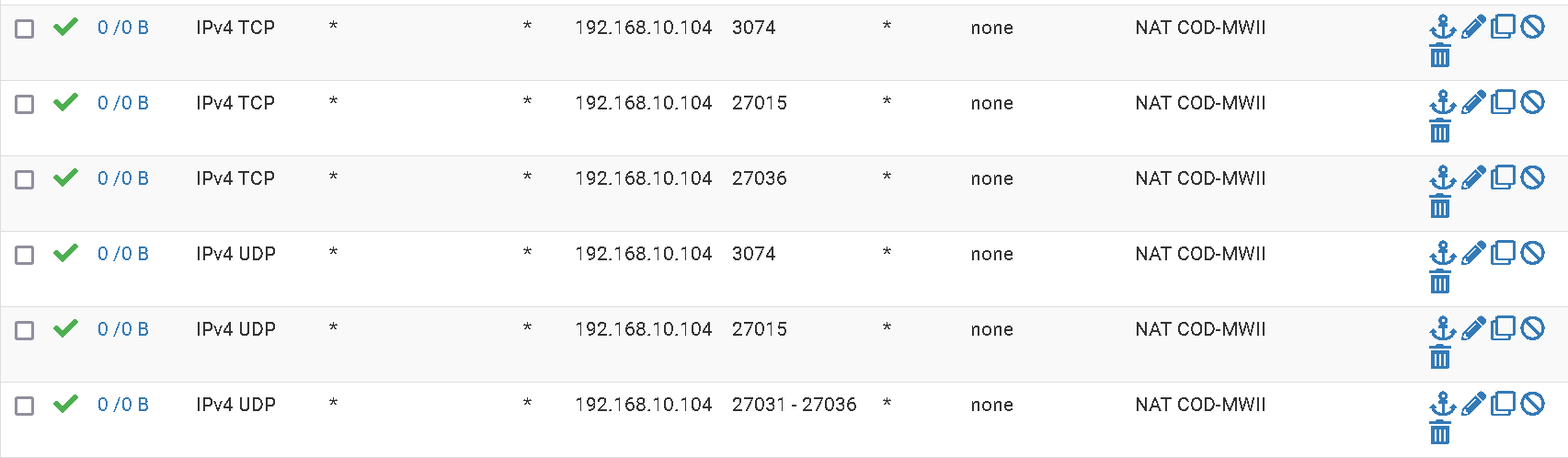
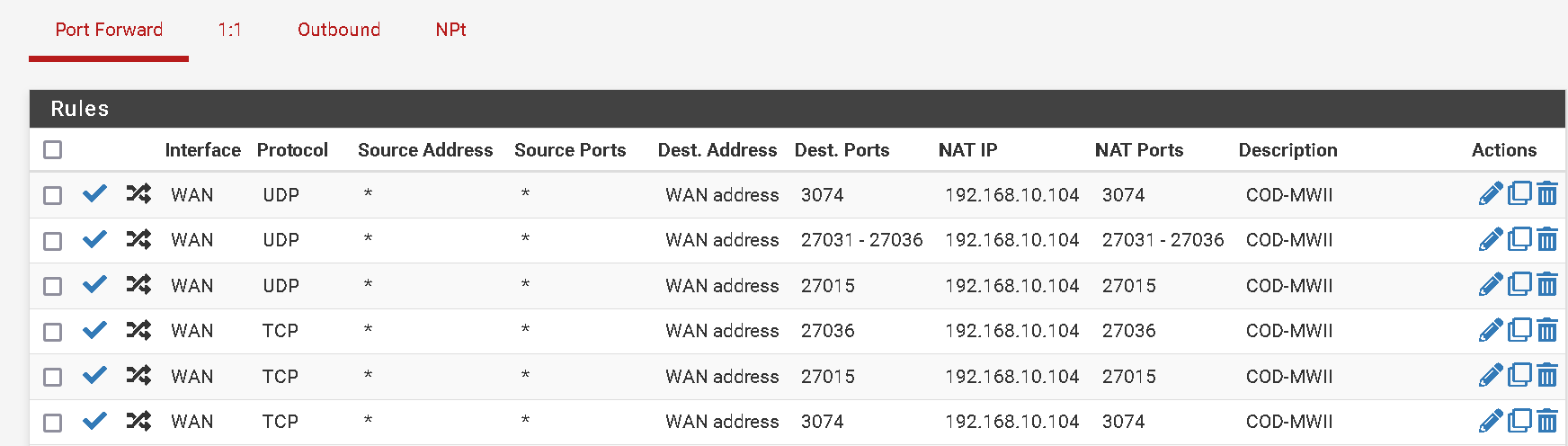
Despite 3075 being open on my firewall, NAT and firewall rule (both udp and tcp) ->
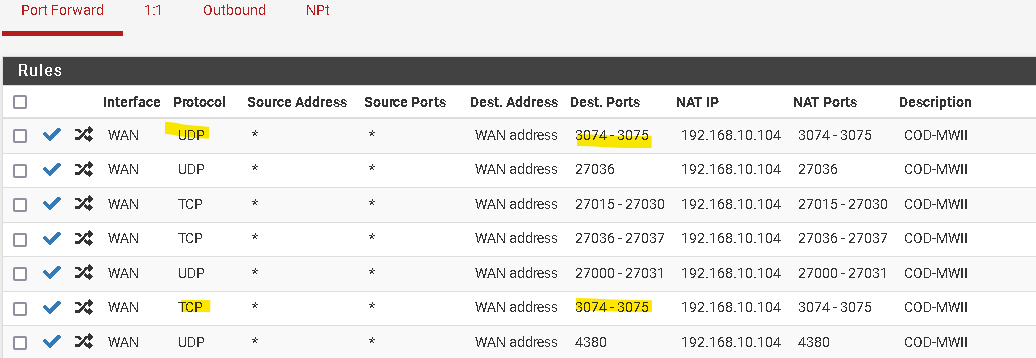
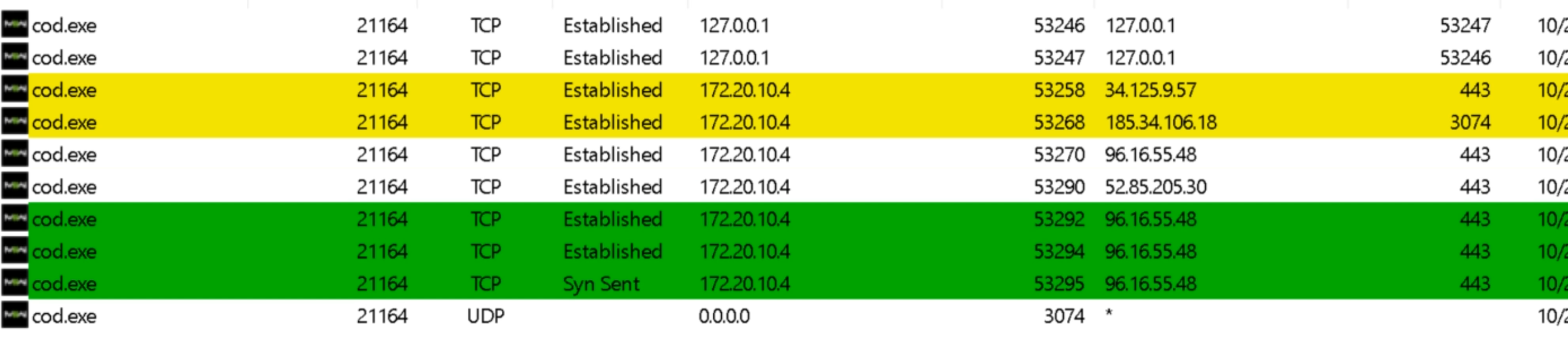
albeit 3075 is not a listed port activision mentioned to open however, if you look at the connection baseline I took while successfully connected to COD over my hotspot, you'll notice an ip that if im not mistaken lives in the same subnet as the COD IP shown in my successful connection. That 185 address should be a COD ip is what i'm saying.This is everything COD was connected to when the connection was successful ->
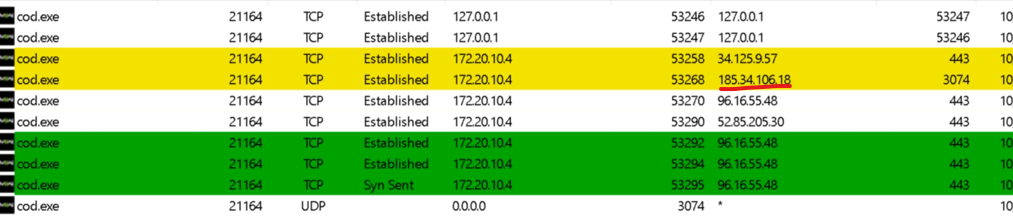
This makes me feel like something still may be blocking on the firewall side..
-
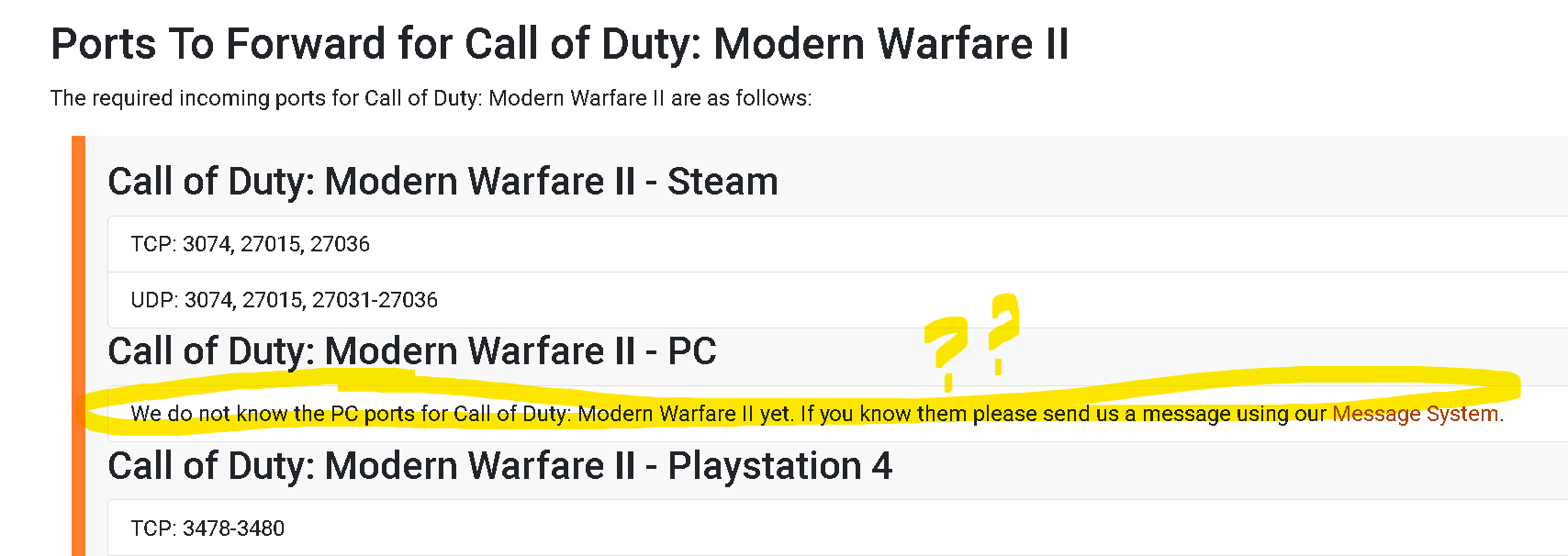
Also does it strike anyone else as odd, looking at the successful connection baseline, the connected ports are none of what activision has advised to open for COD...