Latest Radius server on Synology NAS no longer working with PFSense
-
Hi,
since the last update on my Synology Nas I'm no longer able to login to my PFSense using my domain account.
I can see that the class attributes are set (using Wireshark) but the PFSense told me that there are no class attribute is set.
Is there a way to debug that function in PFSense to see where the problem is? (I don't see any problems in the logs from PFSense)
Or maybe this is the wrong subtree in this forum and someone can help me where I can ask for help. Thx for you help.
Cheers
Marco -
@marco42 Does the radsniff command exist in your nas ?
If it does invoke run radsniff -x and try and connect to your pfsense box it might give you some clues to why its failing.Just installed the package and radsniff is in the /var/packages/RadiusServer/target/bin directory.
andy@nas:/var/packages/RadiusServer/target/bin$ ./radsniff -help
Usage: radsniff [options][stats options] -- [pcap files]
options:
-a List all interfaces available for capture.
-c <count> Number of packets to capture.
-C Enable UDP checksum validation.
-d <directory> Set dictionary directory.
-d <raddb> Set configuration directory (defaults to /var/packages/RadiusServer/target/etc/raddb).
-D <dictdir> Set main dictionary directory (defaults to /var/packages/RadiusServer/target/share/freeradius).
-e <event>[,<event>] Only log requests with these event flags.
Event may be one of the following:
- received - a request or response.
- norsp - seen for a request.
- rtx - of a request that we've seen before.
- noreq - could be matched with the response.
- reused - ID too soon.
- error - decoding the packet.
-f <filter> PCAP filter (default is 'udp port <port> or <port + 1> or 3799')
-h This help message.
-i <interface> Capture packets from interface (defaults to all if supported).
-I <file> Read packets from file (overrides input of -F).
-l <attr>[,<attr>] Output packet sig and a list of attributes.
-L <attr>[,<attr>] Detect retransmissions using these attributes to link requests.
-m Don't put interface(s) into promiscuous mode.
-p <port> Filter packets by port (default is 1812).
-P <pidfile> Daemonize and write out <pidfile>.
-q Print less debugging information.
-r <filter> RADIUS attribute request filter.
-R <filter> RADIUS attribute response filter.
-s <secret> RADIUS secret.
-S Write PCAP data to stdout.
-v Show program version information.
-w <file> Write output packets to file.
-x Print more debugging information.
stats options:
-W <interval> Periodically write out statistics every <interval> seconds.
-T <timeout> How many milliseconds before the request is counted as lost (defaults to 5200).Andy@nas:/var/packages/RadiusServer/target/bin$ ./radsniff -a
1.eth0
2.ovs_eth0
3.docker0
4.eth1
5.ovs_eth1
6.docker6d4825c
7.lo
8.any
9.eth2
10.ovs_eth2
11.eth3
12.ovs_eth3
13.nflog
14.nfqueue
15.dbus-system
16.dbus-session
17.sit0
18.ovs-systemYou'll need to su to run it.
-
I have Additional RADIUS Attributes (REPLY-ITEM) set to:-
Class := "admins",|Service-Type := "Administrative-User"
Class := "admins" is used for pfSense and Service-Type := "Administrative-User" is used for my Linksys switches, I'm using freeRadius on my pfsense box.
The odd thing is pfSense wouldn't have worked previously if the Class missing, maybe Sinology have mangled the data being returned to pfSense.
-
Hi Andy,
many thx. I can try this.
Please don't missunderstand me. I managed it to work in the past and my class string look like:
Domain Users;Users_R;Domain Admins;Denied RODC Password Replication Group;Users_RW;PfSenseGroupand I had added PfSenseGroup to PFSense.
After the last update of my Synology I can see that same class string in the radius response but the PFSense show that the asuthentication works but don't show goups.
Strange thing is that I didn't see any parsing error or any other authentacing error in the logs of the PFSense.
Cheers
Marco -
@nogbadthebad said in Latest Radius server on Synology NAS no longer working with PFSense:
radsniff
this is not available on Synology NAS :(
-
@marco42 said in Latest Radius server on Synology NAS no longer working with PFSense:
@nogbadthebad said in Latest Radius server on Synology NAS no longer working with PFSense:
radsniff
this is not available on Synology NAS :(
Try changing to the following directory and running it there:-
/var/packages/RadiusServer/target/bin
Its there when I installed Radius on my DS1821+ running DSM 7.1.1-42962 Update 2.
-
Ok, I can see that the class attribute is there...like in wireshark....but do you have any idea how I can figure out why PFSense don't show them when I try to test it with
Diagnostics -> Authentication
There I only see that
User xxx authenticated successfully. This user is a member of groups:and the group resonse is empty.
Somthing must fail on PFSense side...but nothing is in the logs. -
Ok, just found that there is a function in: /src/etc/inc/auth.inc
that called
function radius_get_groups($attributes) witch handled the attributes.
Here is the code:function radius_get_groups($attributes) { $groups = array(); if (!empty($attributes) && is_array($attributes) && (!empty($attributes['class']) || !empty($attributes['class_int']))) { /* Some RADIUS servers return multiple class attributes, so check them all. */ $groups = array(); if (!empty($attributes['class']) && is_array($attributes['class'])) { foreach ($attributes['class'] as $class) { $groups = array_unique(array_merge($groups, explode(";", $class))); } } foreach ($groups as & $grp) { $grp = trim($grp); if (strtolower(substr($grp, 0, 3)) == "ou=") { $grp = substr($grp, 3); } } } return $groups; }I would like to debug this one and log all attributes like this
foreach ($attributes as $att) { log_auth(sprintf(gettext('Attribute: '), $att)); }But this shows me only this:
Nov 3 16:35:45 router php-fpm[5433]: /diag_authentication.php: Attribute:
Nov 3 16:35:45 router php-fpm[5433]: /diag_authentication.php: Attribute:
Nov 3 16:35:45 router php-fpm[5433]: /diag_authentication.php: Attribute:
Nov 3 16:35:45 router php-fpm[5433]: /diag_authentication.php: Attribute:
Nov 3 16:35:45 router php-fpm[5433]: /diag_authentication.php: Attribute:
Nov 3 16:35:45 router php-fpm[5433]: /diag_authentication.php: Attribute:So maybe someone can help me with this, please?
Btw. I'm sure that there are attributes:
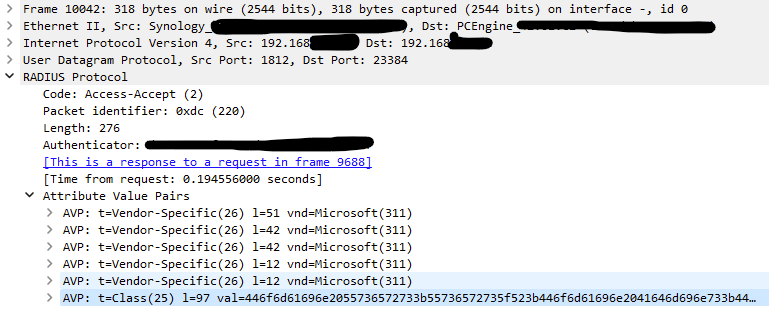
Cheers
Marco -
Ok, found the problem. Synology is now sending the Groupe name in CamelCase.
In the past the Groupe name was lowercase and the check in PFSense is case sensitive.

Cheers
Marco -
Ooof! Nice catch.
