IPSec - tunnel acces over tunnel
-
Hello everyone,
i have a smart question and i hope its not to difficult to get an answer.
I have 2 PFsense and a local fritzbox
One with 10.0.0.0/22 and one with 10.0.4.0/22
On my office, i have an IPSec tunnel from 192.168.2.0/24 to 10.0.0.0/22 - works fine.
From 10.0.0.0/22 to 10.0.4.0/22 is an IPSec tunnel, works fine.
Traffic from local network (10.0.0.0 to 10.0.4.0 and 10.0.4.0 to 10.0.0.0) works fineNow i want to access the ip adresses from 10.0.4.0 from the network 192.168.2.0 over 10.0.0.0/22
So, how is this possible to setup?
Thanks all for your help!
-
@berndrisch said in IPSec - tunnel acces over tunnel:
I have 2 PFsense and a local fritzbox
One with 10.0.0.0/22 and one with 10.0.4.0/22
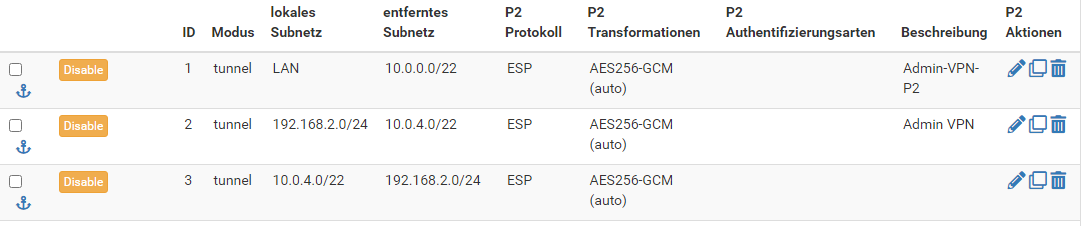
On my office, i have an IPSec tunnel from 192.168.2.0/24 to 10.0.0.0/22 - works fine.May I presume, the 10.0.0.0/22 and 10.0.4.0/22 are behind the two pfSense and 192.168.2.0/24 behind the Fritzbox?
As far as I know, FB IPSec only supports a single phase 2?
-
@viragomann Hey, right, so is it.
But the traffic had to be routet from fritzbox to pfsense 10.0.4.0 over the 10.0.0.0.
The network from fritzbox to 10.0.0.0 is a 10.0.0.0/8
So, the Fritzbox knows where to send the traffic if the action is coming from a PC or anything else -
@berndrisch said in IPSec - tunnel acces over tunnel:
The network from fritzbox to 10.0.0.0 is a 10.0.0.0/8
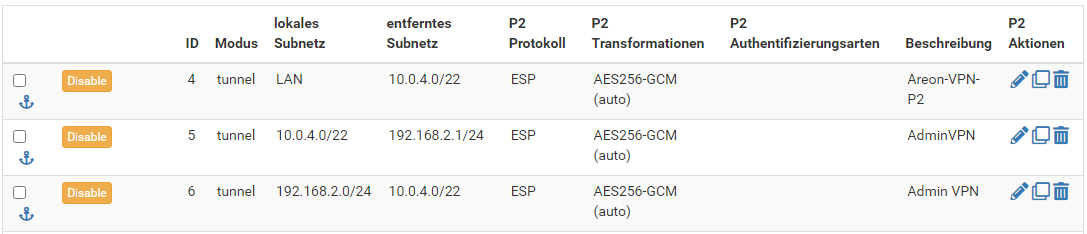
So you have also on pfSense set the local network to 10.0.0.0/8 in p2, I guess?
However, 10.0.0.0/21 would be even sufficient. You should occupy the whole 10.0.0.0/8.Then you also need to add an additional p2 to the connection between the both pfSense with 192.168.2.0/24 as local and 10.0.4.0/22 as remote on the box in 10.0.0.0/22. And on the other box the other way round.
-
-
@berndrisch
Seems to me if all P2 are in a single P1, which cannot be the case.Apart from that, on 10.0.0.0 you have to correct the second tunnels remote network. .1 is not a network address.
And on 10.0.4.0 the second tunnel is useless.
-
@viragomann thanks now it works fine.
Only one thing, the fritbox network is availabe from the 10.0.4.0 network.
So i have to block it with the firewall -
@viragomann hey again, sorry!
We have now the Problem, that one "Customer" had the same ip range on his site as we on our own. (Screenshot)
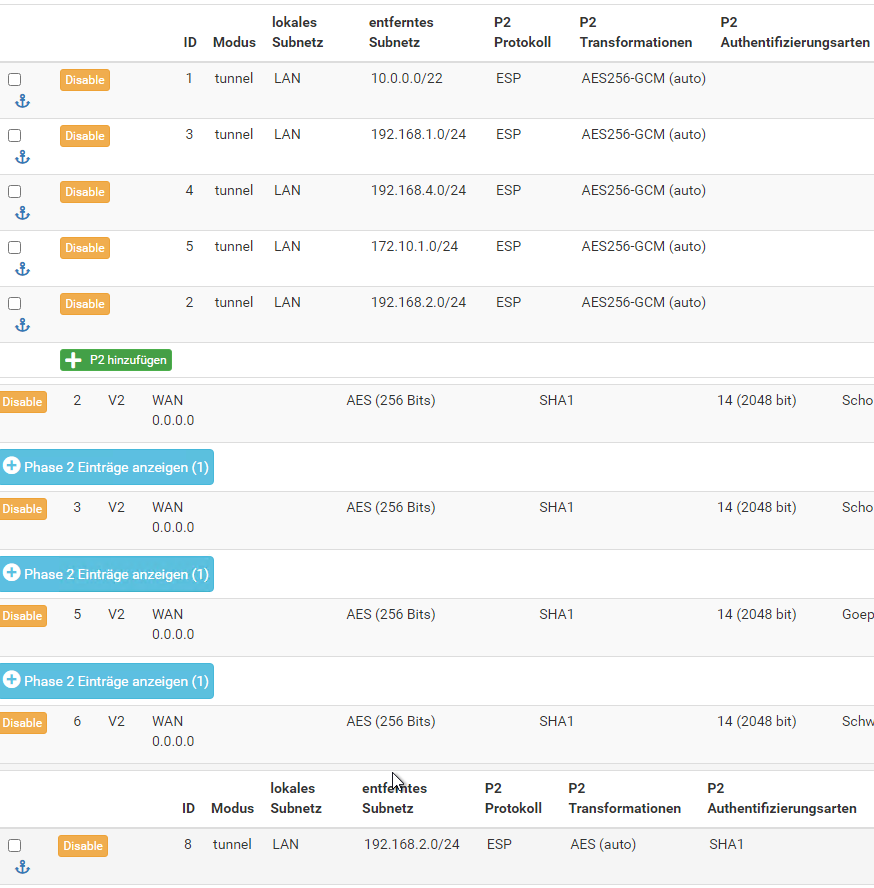
When we start the IPSec tunnel from the Customer, we cannot connect anymore anything from the 10.0.8.0 netzwork (local network pfsense)
Any ideas?
-
@berndrisch said in IPSec - tunnel acces over tunnel:
We have now the Problem, that one "Customer" had the same ip range on his site as we on our own. (Screenshot)
I cannot see any overlapping remote networks in the screenshot.
When we start the IPSec tunnel from the Customer, we cannot connect anymore anything from the 10.0.8.0 netzwork (local network pfsense)
Also not clear, who 10.0.8.0 is involved here. That is neither part of your local networks as you stated above, nor one of the shown remote networks.
In general if there are any overlaps in IPSec involved networks you can nat one of them as a workaround.
-
@viragomann Hi
10.0.0.0 is connected over ipsec to 10.0.8.0
And our local destination 192.168.2.0 is connected over ip sec to 10.0.0.0
The location of the customer with 192.168.2.0 ist connected to 10.0.8.0
When the customer starts vpn, then wen cant connect from 192.168.2.0 over 10.0.0.0