Trouble with Meraki behind pfsense--NAT rules?
-
It looks like documentation is pretty spotty and folks have not quite documented working solutions very well. (I found a link above, but couldn't quite figure out the rule.)
I have pfsense as my home router/FW. My work has given me a Meraki MX64W to VPN back to our work network. I have the MX64W behind my pfsense (on VLAN 80, internal IP 192168.80.11).
I know that the Meraki has to connect to the Cisco cloud for some operations and it has to connect to my company's Meraki concentrator at a public IP. Meaki ports are UDP 7351, 9350-9351.
This is what I have on my pfsense today, but it doesn't seem to work.
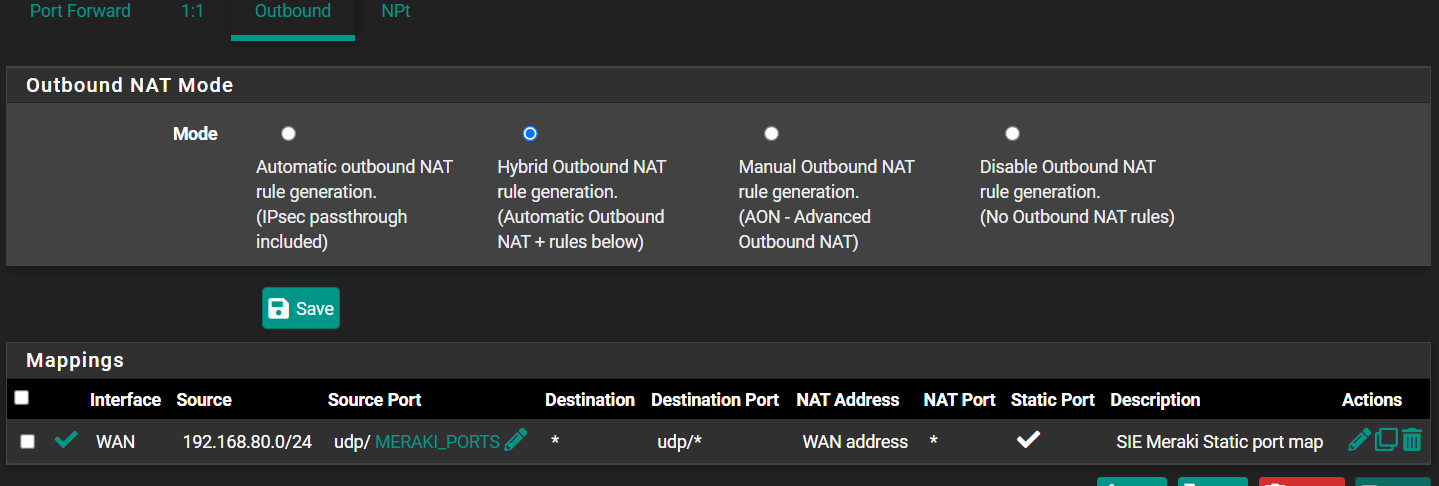
Does anyone know how to connect a Meraki from behind a pfsense? What NAT, 1:1, Outbound, etc. need to be configured?
edit: the white light is on (status okay indicator) on my device and my IT department can see my device, but they see an error that says "NAT type unfriendly".
-
@laplacian Nothing with Outbound NAT.
You just need it on your LAN or if you have it on a new interface make sure you pass those ports on the interface Rule.First thing I would do is delete those outbound rules you made and go to the Firewall
-
I think there needs to be some NAT-ing rules in place on the Merkai.
The Meraki documentation says this, but is unclear on what needs to be mapped exactly. See here.
Also, others have had success with various outbound (or 1:1?) NAT rules. See here and here.
But no one has documented exactly what they did or provided a screenshot! I promise I will do that if I get this figured out...
-
@laplacian If you are pushing the Meraki out a specific way and through a specific route, sure but to get it online? Just plug it in to LAN.
-
@rcoleman-netgate Unfortunately, this stupid device is not that simple. I have allow all out to the internet on that VLAN. Reading through various posts, it seems that folks are saying it needs special NAT-ing (static ports, 1:1, ...?).
Just so you can check, here are my (very permissive) outbound rules on that interface:
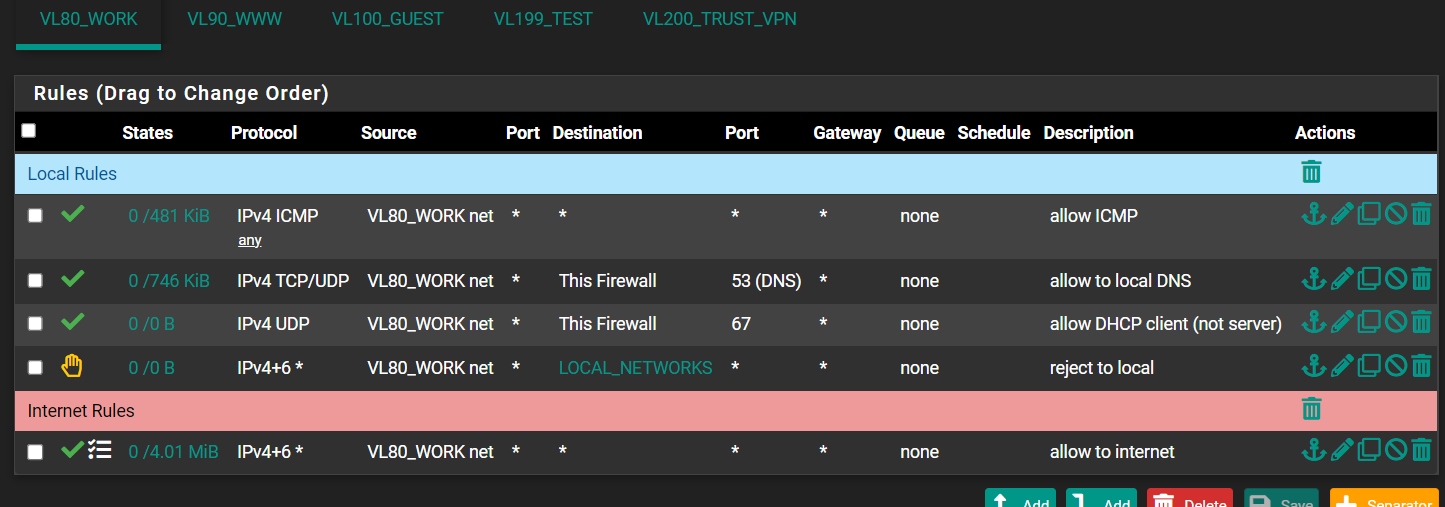
-
@laplacian No special NATs unless the VPN has to come in to connect. If it dials out it just needs the ports open on the interface to get out, that's it. You could give it the one IP an any/any rule and it would work.
-
@rcoleman-netgate said in Trouble with Meraki behind pfsense--NAT rules?:
You could give it the one IP an any/any rule and it would work
As you can see, that's what I basically have. Again, my IT department can see my Meraki device on the cloud dashboard so it is successful in dialing out to whatever cloud service Cisco has. However, I get no network access. It may be dialing back and need a static port, who knows. Does someone here have experience with Merakis like this?
-
@laplacian Is the Meraki set up as a second WAN?
If so you would want to treat it like a PBR - route through it. Yes, ONAT would probably be used then. I presumed you just had the work device connected directly to it and it into your LAN. -
@laplacian Meraki needs no special rules or NATs to connect into the cloud. It is designed to work when plugged into the dumbest of ISP provided routers, so don't over-think the config.
You indicated that your IT department can see that it is "connected" to the Meraki cloud, so they should be able to see both the actual IP assigned to the device, a 192.168.80.x address, as well as your public IP address that it is NATted behind on the device's "Uplink" status page.
However, they need to make sure that NAT Traversal is enabled in the Cloud dashboard under the VPN settings for the device. -
@awebster this is why I think it's set up as a second WAN -- PBR is what they want in that case...
-
@awebster said in Trouble with Meraki behind pfsense--NAT rules?:
However, they need to make sure that NAT Traversal is enabled in the Cloud dashboard under the VPN settings for the device.
Yup, verified. "NAT traversal: Automatic, Connections to remote peers are arranged by the Meraki cloud."
@rcoleman-netgate said in Trouble with Meraki behind pfsense--NAT rules?:
I presumed you just had the work device connected directly to it and it into your LAN.
Meraki -> managed switch -> pfsense -> cable modem
My managed switch puts the Meraki VLAN 80 and you see the internet permit rules that I have on that VLAN above.
@awebster said in Trouble with Meraki behind pfsense--NAT rules?:
so they should be able to see both the actual IP assigned to the device, a 192.168.80.x address, as well as your public IP address that it is NATted behind on the device's "Uplink" status page
Yes, the Merkai dashboard shows my LAN address and my ISP-given public IP address. It shows an active connection. However, the dashboard shows the following error:
NAT type: Unfriendly. This security appliance is behind a VPN-unfriendly NAT, which can be caused by upstream load balancers or strict firewall rules.
-
@awebster said in Trouble with Meraki behind pfsense--NAT rules?:
It is designed to work when plugged into the dumbest of ISP provided routers, so don't over-think the config.
In another post (here) a Netgate admin stated this:
@stephenw10 said in pfSense and meraki z3:
The reason it works behind some other firewall is that most SOHO style so not randomise the source port for NAT'd connections. pfSense does that to increase security and to prevent multiple outbound states all using the same port which could conflict. For some reason the remote Meraki device is unable to cope with more than one source port.
I am using the info in that thread as reference, but am not getting the config/outbound NAT quite right.
-
bump
Does anyone else have an idea for how to solve this? I tried plugging my Merkai directly into my cable modem and it worked perfectly.I think I need a better understanding of how to do a static NAT configuration. I want my source and dest ports to stay the same, per my company's IT team.
Meraki reference here.
-
***** Solution *****
Okay, after reading through the pfsense documentation more thoroughly, and exercising some patience to let Cisco/Merkai establish the correct links, I have a working setup.As stated previously, pfsense randomizes ports for security/stability reasons. This is something that regular consumer-grade routers don't do, apparently. Per the pfsense documentation here:
- By default, pfSense software rewrites the source port on all outgoing connections except for UDP port 500 (IKE for IPsec VPN traffic). Some operating systems do a poor job of source port randomization, if they do it at all. This makes IP address spoofing easier and makes it possible to fingerprint hosts behind the firewall from their outbound traffic. Rewriting the source port eliminates these potential (but unlikely) security vulnerabilities. Outbound NAT rules, including the automatic rules, will show fa-random in the Static Port column on rules set to randomize the source port.
Per Cisco documentation (and my IT team), I gleaned that the Meraki doesn't like the source ports to be changed.
So to fix this, you need to create an outbound NAT rule for the Meraki device. Go to Firewall->NAT->Outbound.
Select "Hybrid outbound NAT" as the mode. Create a new rule/mapping as follows...
Interface: WAN
Address family: IP4+6
Source: your internal subnet (I just targeted mine to the /32 that my Meraki is assigned)
Source port: (blank)
Destination: Any
Dest port: (blank)
Static Port: be sure to check this box!I suppose you can whittle this down to the specific Merkai ports (7351, 9350-9351), but this is a single-purpose VPN device and I just figured I'd avoid future problems by just setting this to any port. Same for the destination...you could probably set this to your company's Meraki IP, but again, this is a security device (router/firewall/VPN) that only talks to the Cisco cloud and to the VPN concentrator, so that should be unnecessary. Here is what the rule should look like.
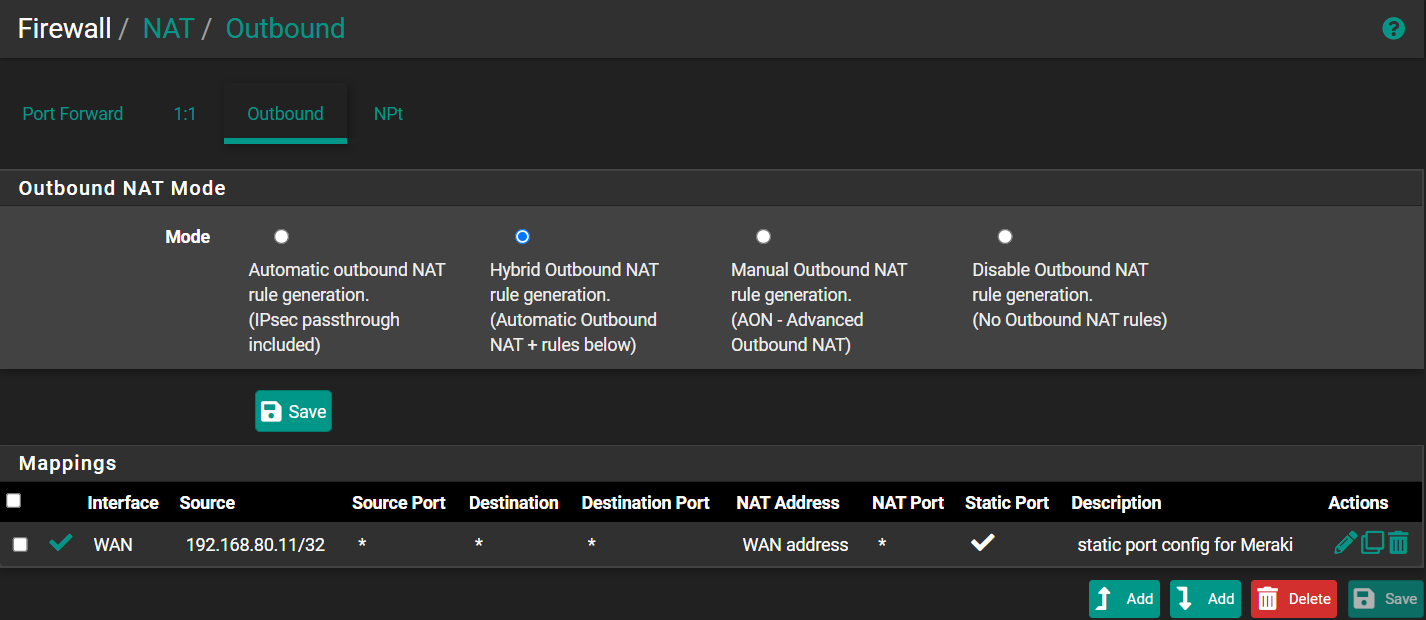
Again, my company uses Auto NAT traversal and has our Merakis in site-to site mode and this worked for me. If they used manual NAT traversal, then you'd probably have to set a couple of different rules mapping the home Meraki to the company concentrator.