Home Lab setup seperating networks
-
Hi I am using proxmox on a BMAX Pro 5 mii PC, it comes with a 1Gb NIC which is connected to my home router. I have added a USB - NIC which I have connected to a 5 port switch.
I want to setup pfSense with 2 LAN connections one will serve my Desktop PC and TV the other will work as an internal LAN for my VM's and Containers in Proxmox.
This is how I have setup my network in Proxmox
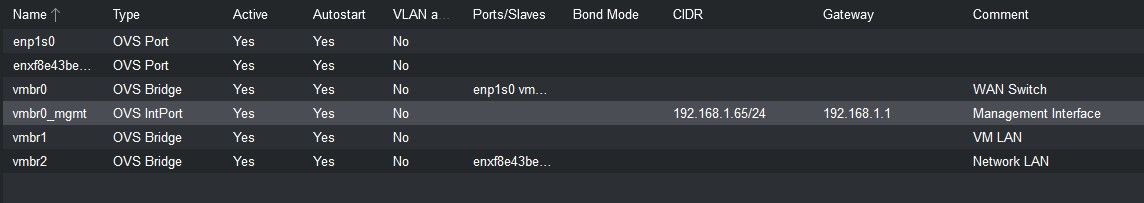
WAN - IP range 192.168.1.1
LAN HOME IP range 192.168.55.1/24
LAN VM IP range 174.0.0.1/24In order for me to access the VM's and Containers I plan to run web services from, what firewall rules would I need to add to pfSense so I can access the services from the VM's / containers on my Home network ?
Containers will run media server Plex, Sonarr, Jackett, InfluxDB2 + Grafana, Nginx PM, organizr
I hope I have provided enough info, any help much appretiated.
-
@techiemike
All depends on what you want to give access to.
If you want your LAN to access anything on the LAN VM, then the default any any rule that will be on the LAN interface does that.
If you want the LAN VM to access anything on the LAN, copy that default rule to the LAN VM interface.If you only want "some" LAN VM devices or services to access the LAN, you would only allow those devices/services.
My point here is, only you can decide what rules you'll need based on what you want.
Keep in mind, rules are applied only to the interface they're on, and only to traffic that comes into that interface from the attached network.
So the default Any Any on the LAN allows all LAN device access to anywhere. By default your LAN VM interface will have no rules on it which will block access to anywhere. -
@jarhead Thanks for the reply, MY TV on the 192.168.55 network would need access to the plex server which is running on the 174.0.0 network, can I just allow the plex port between the two networks
I have setup a vlan as adding another bridge was giving errors - I have set the vlan 888 to use the 174.0.0.1 ip range, I have created a CT which gets an address 174.0.0.24 but it will not connect to the internet to run updates and I cannot ping google.com?
-
@techiemike said in Home Lab setup seperating networks:
@jarhead Thanks for the reply, MY TV on the 192.168.55 network would need access to the plex server which is running on the 174.0.0 network, can I just allow the plex port between the two networks
You would put a rule on the LAN VM interface to allow it to the TV. But I don't see any reason not to allow complete access from what you've posted.
I have setup a vlan as adding another bridge was giving errors - I have set the vlan 888 to use the 174.0.0.1 ip range, I have created a CT which gets an address 174.0.0.24 but it will not connect to the internet to run updates and I cannot ping google.com?
Don't know what a CT is but what rules did you put on the vlan888 interface?
-
Yes, you need rules on the LAN VM interface to pass that, and only that, if you need it.
Steve
-
@stephenw10 Thanks for the reply, I change my configuration - I have my home network/router connected to the 5 port switch (WAN)
I have connected the server to one of the ports with a 192.168.1 IP my PC is also conected to the switch (I will get an additional NIC and create another network at some point) I have then created a LAN with a 192.168.10.1 IP range, which is bridged to the other NIC connected to my TV, this works fine for the media server running on a CT (container) in proxmox.
What firewall rules do I need to create in order to connect to the CT/VM's running in Proxmox, I know the general rul is not to connect from the WAN to LAN but in my case they are both behind a router.
I would like to run several web services that are only accessable to me on my home network, I do not need to have any remote access, only while I am at home, most of the guides refer to opening ports 80/443 etc.
I would like to be able to browse the web services from my home pc on the 192.168.1 range to the servers running on the 192.168.10 range. (or whatever my ip range is when I add a new NIC to seperate the PC)
-
@techiemike If I am being honest, not too sure what you want to archive here however I will make a little bit of a guess. I run a similar setup but, on the VMware/vcenter side.
Not trying to feed you eggs here so please do bear with me.
To access my web servers from the WAN, I use a reverse proxy so in your case, just turn of the reverse proxy if you have it installed and turned on.
Put your servers behind your "Server VLAN" you want and just to be sure, put a rule on the VLAN to stop anything from your WAN interface.
My guess is you will be accessing your "server VLAN" from your LAN. If that case also put a rule on the "server VLAN" to allow connectivity from your LAN.
If your switch is a managed switch, you can do some well funky stuff. If you dont have a managed switch, I will recommend getting one. Cisco 3850 or any of the juniper ones but they are loud so you may want to setup in a garage or something. You should be able to pick them up on ebay, amazon as they are EOL and cheap. Otherwise netgear has a few desktop managed switches out there. Only stated these are these are what I know and use. For home networks, they are perfectly fine
You probably already know but a managed switch is a beauty.
I hope this helps. Keep it simple.
-
In that sort of setup you just need to add port forwards in pfSense to whatever you need to access.
You can't just route between them because your clients are using the ISP router as their gateway. I doubt you can add vlans or static routes to that router.
Steve