WAN Rules
-
Do you think this may be considered as a good practice under WAN Interface:
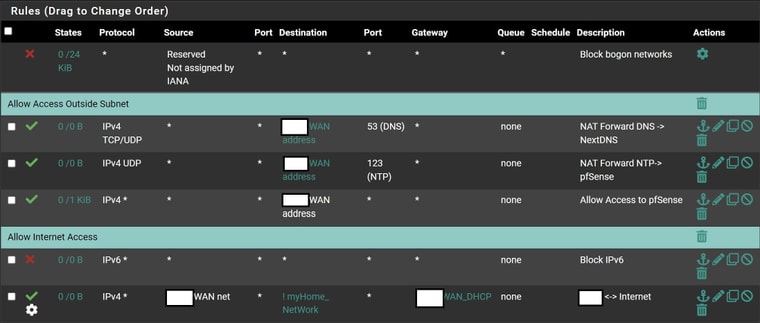
- Hijacks DNS and NTP queries and make sure it goes through pfsense and Adguard
- Prevents ISP from accessing my home network
-
@magikmark no those rules are not good on wan rules, what exactly do you think that would be hijacking?
Why would you all access to pfsense from the WAN? So like any bot or script kiddie, whatever can hit pfsense on any port - that you only have 1 kb hit on that? Is pfsense behind a nat router?
Not sure where you got the idea allow internet access anything would go on the WAN interface?
-
- I just forward all DNS & NTP queries to my Adguard / Next DNS for filtering
What would be a good rule for WAN then?
-
@magikmark The default.. The only reason you should be putting rules on the "WAN" is if you want to allow access to something, via say a port forward.
If you want to intercept dns and ntp - those would go on a LAN side interface..
WAN is internet facing - normally! Is pfsense behind another router and you have devices on this other network? Ie pfsense "wan" ??
If that is the case you need to explain that - those rules make no sense for a typical setup where pfsense wan is the internet.
-
@magikmark said in WAN Rules:
Do you think this may be considered as a good practice under WAN Interface:

- Hijacks DNS and NTP queries and make sure it goes through pfsense and Adguard
- Prevents ISP from accessing my home network
The only thing I can think here is you're thinking backwards.
Rules on the WAN would only apply to devices on the WAN, namely, the internet.
Why you want anything on the internet to use your pfSense for DNS and NTP queries?? Did you mean everything on your LAN maybe? If so, those rules would go on the LAN interface as already said.
Rules are applied to the directly connected network of that interface. So WAN rules only effect WAN devices, LAN rules only effect LAN devices etc.
Delete all WAN rules and leave it that way is the best practice. If you need to access something on your LAN from the internet, use a VPN. -
Thanks for the reminder guys I was just conducting an experiment on how my ISP would respond. So far it doesn't make any differnece
-
@magikmark it shouldn't as those have to all originate from OUTSIDE your network, not inside.