IPsec overwriting Shared Secret
-
FW in a small office environment is running on the latest version of pfsense.
We have IPsec VPN for our users to connect and work from home (remote access).Yesterday I set up a new Site-to-Site VPN connection for a group of users, who work in the office, so they can access servers at another place. These users are separated in their own VLAN with a separate IP range. This works fine and is only accessible for those people in the separate VLAN.
Today I got complains, that the Shared Secret for those trying to connect from home is no longer valid - VPN connection failed. It made me suspicious, since the two IPsec configurations have different Shared Secret. After changing the Shared Secret on the mobile client to the one which is used for the Site-to-Site VPN, login works as it did before…
Is this a bug or am I making a mistake? Using IPsec as well for incoming as for outgoing tunnels on the same FW should be possible.
Any experience or advice is welcome.
Cheers Peter
-
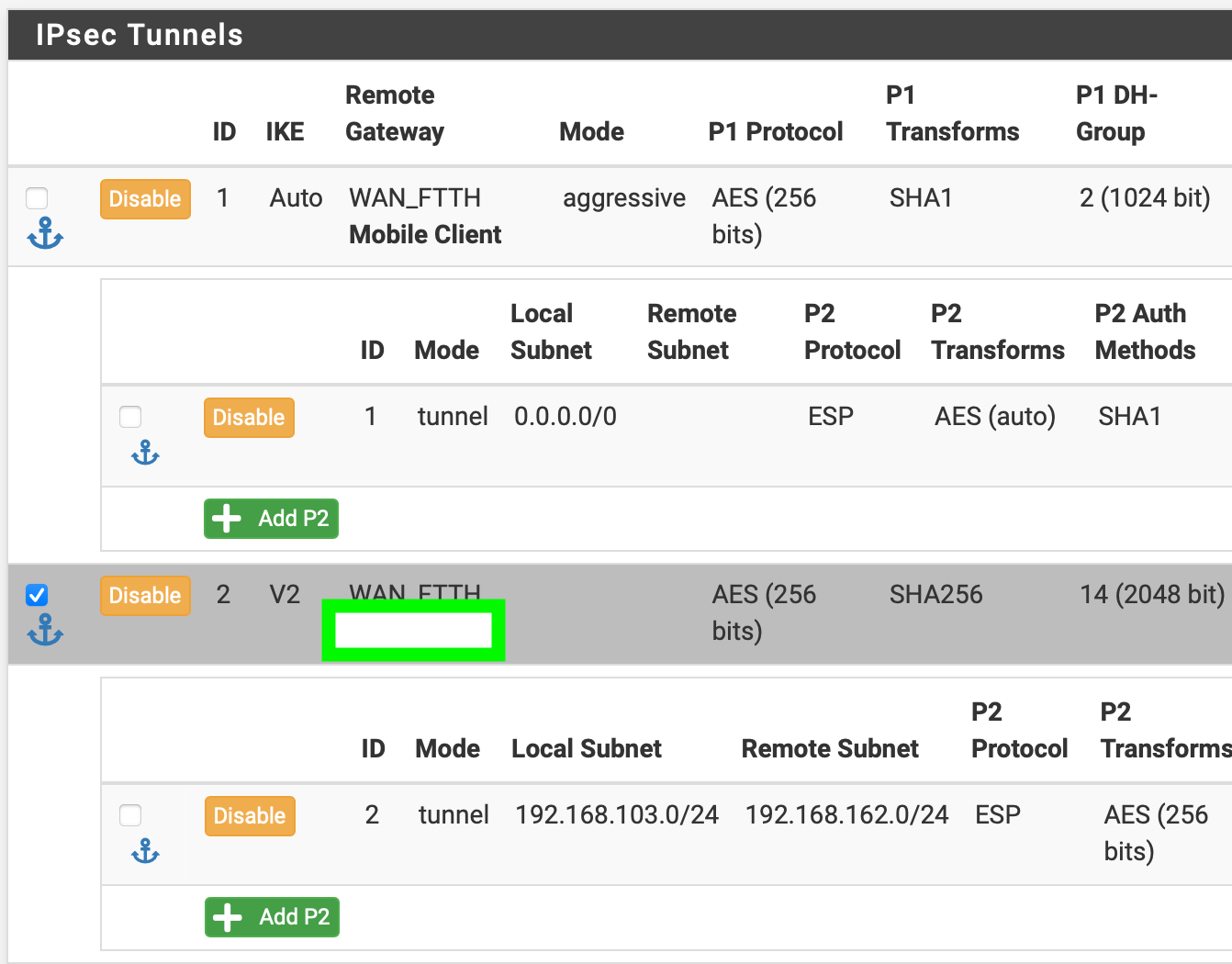
The two are separate and would not interfere with each other, but it's possible that the same P1 is matching the remote mobile clients and the site-to-site. Is your site to site setup for a specific remote address or did you use
0.0.0.0there? If the latter, it's easy for it to get confused since both mobile and the site to site would have to get further in the connection process to distinguish between the P1 entries. -
@jimp must be something else… Site-to-Site has remote address set.
I've checked P2 as well vor both VPNs. They have the correct values for their P1 set.