Policy based routing
-
I have two gateways. One is my wan. The other is my vpn (mullvad), which goes out over my wan.
I want certain traffic to egress over the vpn and if the vpn is down I do not want the traffic to egress at all.
I have two rules for computer x. The first rule is a pass rule that says route computer x over the vpn. The second rule is a block rule that says block traffic from computer x. All traffic should from x should be caught and routed over the vpn by the first rule. If the gateway is down I expect the traffic to fail to egress. In the event that for any reason the traffic misses the first rule then the second rule should block the traffic.
When the vpn is online I notice that traffic correctly passes out through the vpn gateway. However, when my vpn goes offline (as shown by the status in the pfsense home page) the traffic goes out over my wan. Moreover, looking at the log, it shows that the traffic is being caught by the first rule (to route via the vpn) but nevertheless is going out over the wan. I do not understand why traffic is egressing via WAN when the rule specifically says egress via the VPN. I cannot think how to investigate this further either, as I can see the right rule is being matched in the logs and the gateway is set to VPN.
I tried deleting the rules and rewriting them and assigned computer x a new IP address for the new rules to pick up. I’ve restarted pfsense and computer x. Can someone see what may be happening or could you suggest how I can investigate the issue further? I do not understand why the traffic is egressing via the wan when the vpn is set as the gateway, to utilise policy based routing.
-
@jeremyj set up a gateway group with the vpn as tier 1 and the wan as tier 2, point the firewall rules that you want to normally go via the vpn then wan to the gateway group you create.
-
Thanks, but I do not want the traffic to egress at all if it cannot egress over the vpn. If I have tiers won’t it just go to tier 2 when tier 1 is down?
-
@jeremyj Oh sorry I misread your post.
-
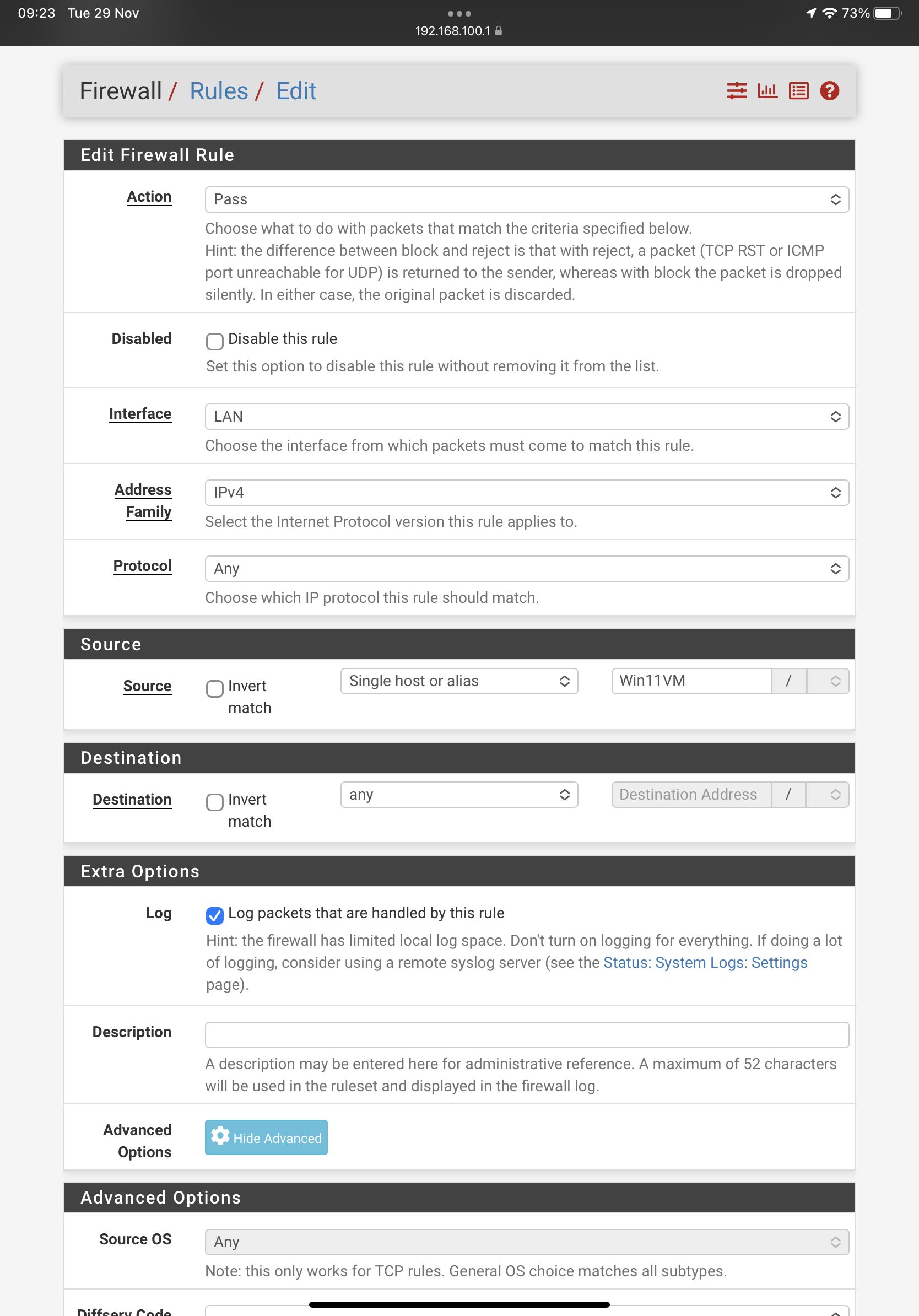
Post a screenshot of your rules.
-
@nogbadthebad
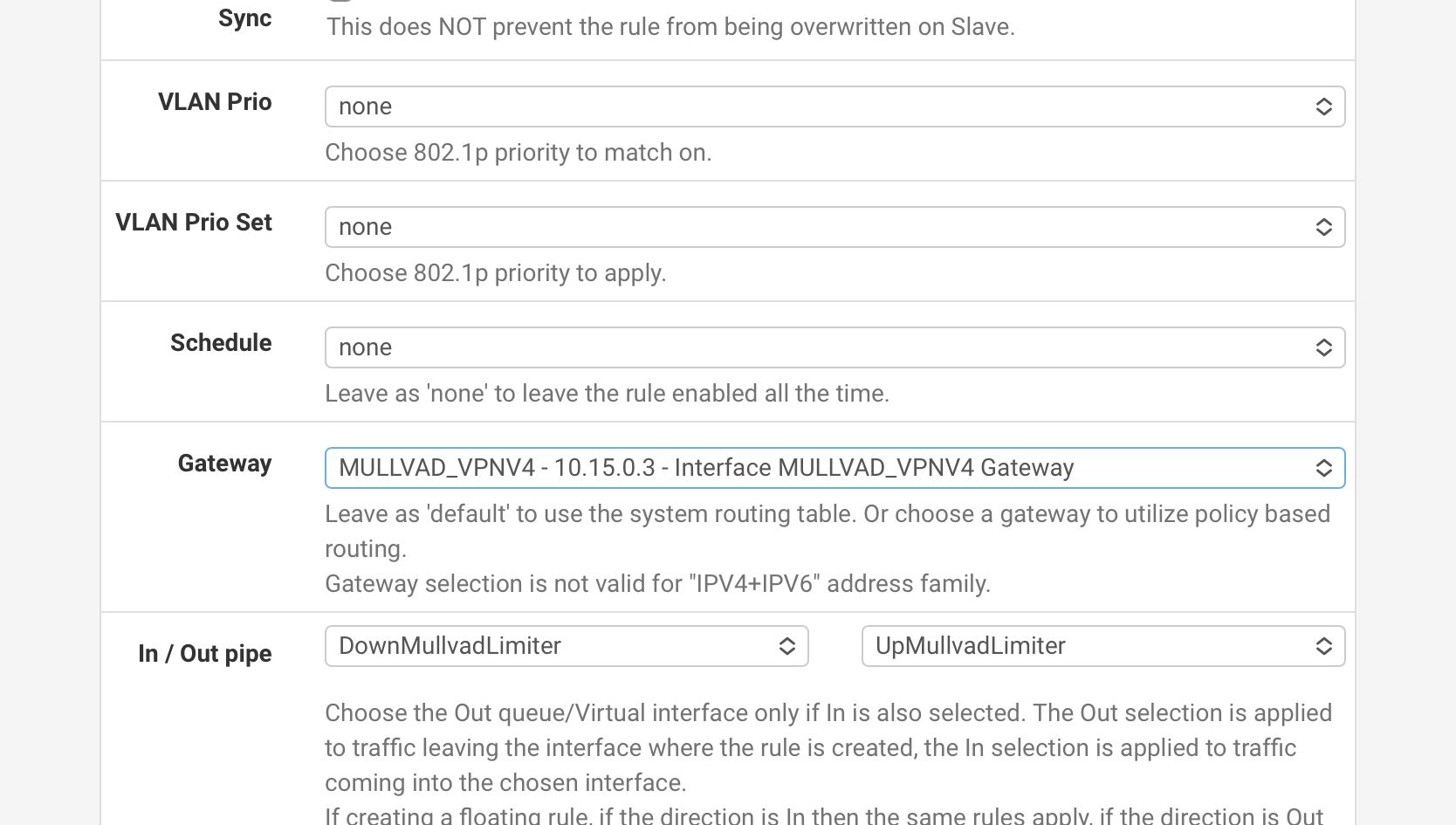
Thanks I’ve added pics to the question above. There are only three options set: the source computer, the gateway, the pipe. Thanks for the help. -
I think it may be that you have to set an advanced option to force the gateway use. I think it is documented here:
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#enforcing-gateway-usePersonally, that seems a really counterintuitive thing to have to set. It rather defeats the purpose of selecting a specific gateway. If failover to another gateway is wanted, that seems the whole purpose of gateway groups.
If I am wrong or right about this being the source of my original problem, grateful if someone could confirm/disconfirm.
-
@jeremyj said in Policy based routing:
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#enforcing-gateway-use
Your link is the answer, per default pfsense want you or your "company" to be able to "work" when a gateway is failing, so you as the admin have to enforce that it doesn't work. At first pfSense is a firewall for businesses and not a VPN-Client for privacyVPNs for homeuser.

-
@bob-dig
Thank you. Appreciate you taking time to confirm.I hope the author manual sees this post! It would be helpful to make that behaviour clearer generally in the routing and gateway terminology employed in the manual as the wording in most places suggests that a gateway “will” be used. But it seems “may” is more accurate, given the default behaviour.
-
@bob-dig But thats a bad excuse for something that shouldnt happen in an enterprise grade FW.
When I DONT state that there is a failover GW, then ALL policy based routing to the failing GW should NOT be rerouted.
This is basic stuff.... This is networking for dummies.
This is a flaw.
-
Yep. It’s also an externally awkward method of enforcing the gateway egress since if you set the advanced option then instead of privately substituting in another gateway, pfsense just disregards the rule entirely! So you have to create a further rule to then block egress. Overly complex and counterintuitive, compounded by lax terminology in the manual around rules and gateways.
-
@jeremyj I don't find it that complex but it is also not a consumer product.
Instead of changing the advanced option you can create a VPN Killswitch via tagging. You would tag packets in your rule and then create a blockrule on WAN watching for those tags and if tagged traffic is reaching WAN that blockrule would trigger. -
In System > Advanced > Misc you need to set
Skip rules when gateway is down.Otherwise the pass rule is still created but without the VPN gateway set when it goes down. Hence the traffic leaves over the WAN directly.
Steve
Edit: What Bob said!
