DNS Leak with VPN
-
I have configured an OpenVPN tunnel to Surfshark. Than I configured Google DNS in my pfsense General settings and configured the pfsense DNS Resolver to use my VPN as "Outgoing Interface". All LAN devices use the pfsense resolver.
Now I did a DNS Leak Check on the Surfshark Website. The test says I have a DNS Leak. Is this a false positive? Is my configuration secure?
-
@thisisme Try it on https://www.dnsleaktest.com/ and tell us, what it says.
-
@bob-dig First I have to admit I made a issue in My description: Google is defined for my WAN Interface and Quad9 for my VPN Interface (General settings DNS section)
The response from the leak test is:
Google Frankfurt am Main, Germany
This is a bit strange, but I still wonder what out going interface was used or what source IP is shown to the DNS
-
@thisisme
The DNS Resolver use the stated servers in general settings only if you enable the forwarding mode.Also you should not state gateways at the DNS servers in general settings.
-
@thisisme said in DNS Leak with VPN:
Is my configuration secure?
That's a rabbit hole question.
Its open to debate if sending all DNS requests to Google (8.8.8.8) is 'secure'.
Is sending data to Google meant to be secure ?
Do we really know what Google does with your data
Let's say OPENVPN is my OpenVPN client "WAN" interface.
Selecting only OPENVPN (see image) would limit unbound to use only OPENVPN for its outgoing connection.The outgoing interface unbound uses :
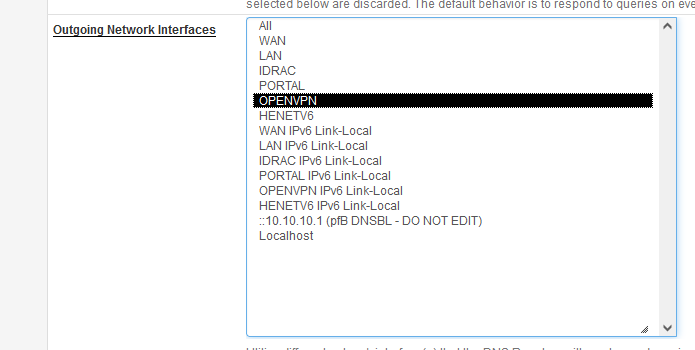
But ... when the system boots, unbound probably starts up earlier as the OpenVPN client.
So, the OPENVPN interface doesn't exist yet / isn't usable yet at that moment.
When the OpenVPN connection is established, an 'interface' events happens, as there is now a new WAN type interface : OPENVPN. unbound gets restarted, now it find OPENVPN, it was told to use that interface, and you should be good.
If, for some reason, the OpenVPN client doesn't come up, what is then the status of unbound ? What outgoing connection is used ?I know, these are questions, not answers.
But I advise you to test and document these situations. -
@viragomann said in DNS Leak with VPN:
@thisisme
The DNS Resolver use the stated servers in general settings only if you enable the forwarding mode.Also you should not state gateways at the DNS servers in general settings.
Not? I don't fully understand what this option does but it says "When using multiple WAN connections there should be at least one unique DNS server per gateway." Do I misunderstand this?
-
-
@thisisme said in DNS Leak with VPN:
Not? I don't fully understand what this option does but it says "When using multiple WAN connections there should be at least one unique DNS server per gateway." Do I misunderstand this?
The DNS servers are used as listed. The first one has higher prio. But stating the gateway forces pfSense to send out the the DNS to it.
-
@viragomann
This is what it says in documentation:When using the DNS Resolver in forwarding mode or the DNS Forwarder, the firewall uses its routing table to reach the configured DNS servers. This means without any static routes configured, it will only use the WAN with the default gateway to reach DNS servers. Gateways must be selected for each DNS server defined on the firewall. This forces the firewall to use a specific WAN interface to reach a given DNS server. At least one gateway from each WAN should be selected where possible.https://docs.netgate.com/pfsense/en/latest/multiwan/interfaces-and-dns.html#multiwan-dns-servers-and-static-routes
Does this behaviour apply to unbound or only to lookups from the FW itself? Because I want unbound to not use default route. How does this correlate with outgoing interface settings in inbound?
-
@thisisme
I did some tests and these are the results:Unbound will look up all configured DNS Server in parallel. So it also uses the DNS Server configured with the WAN Gateway.
If I use package capture there is no traffic for port 53 on my WAN Interface.
If if disable forwarding mode in unbound I pass the dns leak test.
Can I assume that's still safe to use forwarding mode, because the traffic seems to be on VPN Interface only?
