Change DNS server for a set of IPs in ALIAS (DNS Forwarder)
-
Hello.
I'm using pfSense as a DNS Forwarder successfully.
pfSense IP: 192.168.70.3
Network DNS server: 192.168.70.4
PIA DNS server for OpenVPN: 10.0.0.243My pfSense server is the DNS in DHCP server configuration, which forward all DNS requests to my network DNS server.
Now I have also successfully implemented OpenVPN client (PIA) and assigned a set of IP hosts (200+) under alias PIA_ENABLED_HOSTS. But for these hosts in the alias, I would like to assign a different DNS, the one provided by PIA (10.0.0.243).
I have statically made this change by assigning a manual IP for DNS in the DHCP releases, but since there are many hosts, is there a way to make the pfSense to forward DNS requests to 10.0.0.243 instead of the configured 192.168.70.4 only for the IPs in the PIA_ENABLED_HOSTS alias?
I've tried a manual NAT port forward but it doesn't work...
-
@adamitj said in Change DNS server for a set of IPs in ALIAS (DNS Forwarder):
I've tried a manual NAT port forward but it doesn't work...
Cannot think of any reason, why this should not work, as long as the hosts send unencrypted DNS requests on port 53.
If you have created a policy routing rule to direct the concerned upstream traffic to PIA, consider to put a separate rule w/o a gateway stated for allow DNS requests above of it.
-
@viragomann
Guess what? You're tottaly right.
After reading your answer I realized that Google Chrome in my workstations were doing DNS over TLS requests.
Just duplicated the rule to cover TLS and everything is working now.Thanks you for the help!
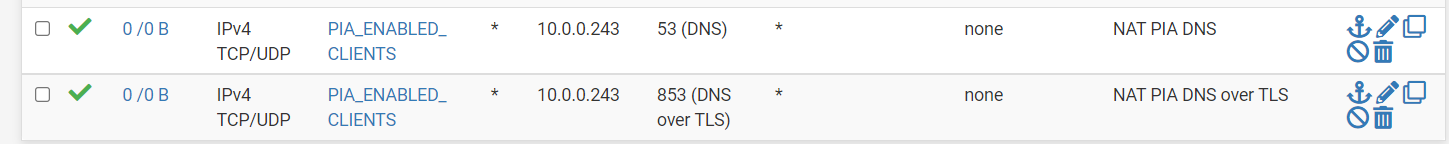
-
@adamitj
DoT requests which are redirected to another server won't work anyway, because the SSL verification will fail.Therefore I simply block all DoT and DoH in my network. Hence the clients have to do unencrypted DNS requests, which I can redirect as needed.