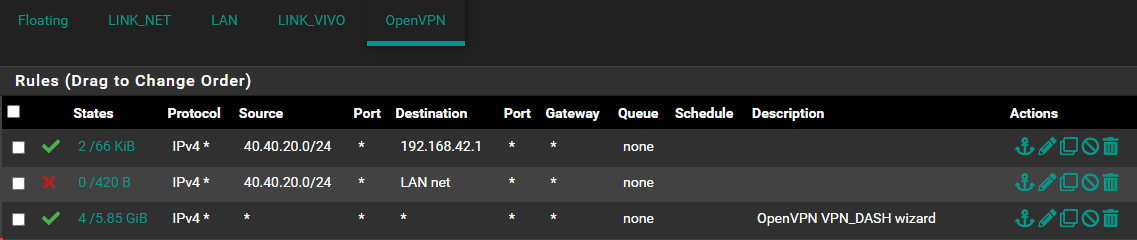
openvpn connections block and allow specific rule
-
I have a user authenticated by OPEN VPN on an OPENVPNserver with a specific tunnel for this guy.
it only needs to be on the local network after connecting accessing a specific server on a specific port which is the database.
How do I make the rule in PFSENSE to prevent this guy who is in this VPN tunnel from this server from being able to ping or give a // to the other local servers.
I wanted to block everything from that source and accept only the connection on the port of the db in a server specific.
is it possible to do that ???
-
@rafaelvilelacosta94 adding to make it clearer
Next, I have the following problem.
We had to release VPN access to a specific provider, we created an OPENVPN server for him
local network 192.168.42.55/24 tunnel network 40.40.20.0/24this provider only needs access from this local network when logged into the vpn the DB server 192.168.42.55 on port 61433.
However, as we provide him with the VPN, he is on the local network where the server is located.
I wanted to know if it is possible for me to block all his traffic and create a specific rule only: RELEASE FOR HIM ONLY ACCESS TO THE SERVER 192.168.42.55 AT DOOR 61433
This guy will probably use some tool to work in the Bank so he would basically use the vpn just to be able to see the server on the local network and point the tool at the db port.
but I can't let him free to give a //, drip other things.
it's possible ?
-
@rafaelvilelacosta94 if I declare to drop without determining the origin the employees who are in another vpn server in another tunnel the rule will apply to them and drop everything, I need it to be just specific for this tunnel created for this guy's access.
-
@rafaelvilelacosta94
You can simply state the respective OpenVPN tunnel network as source in firewall pass rules on the OpenVPN tab for each server and allow destination IP and port as desired. -
@viragomann
 ```
```
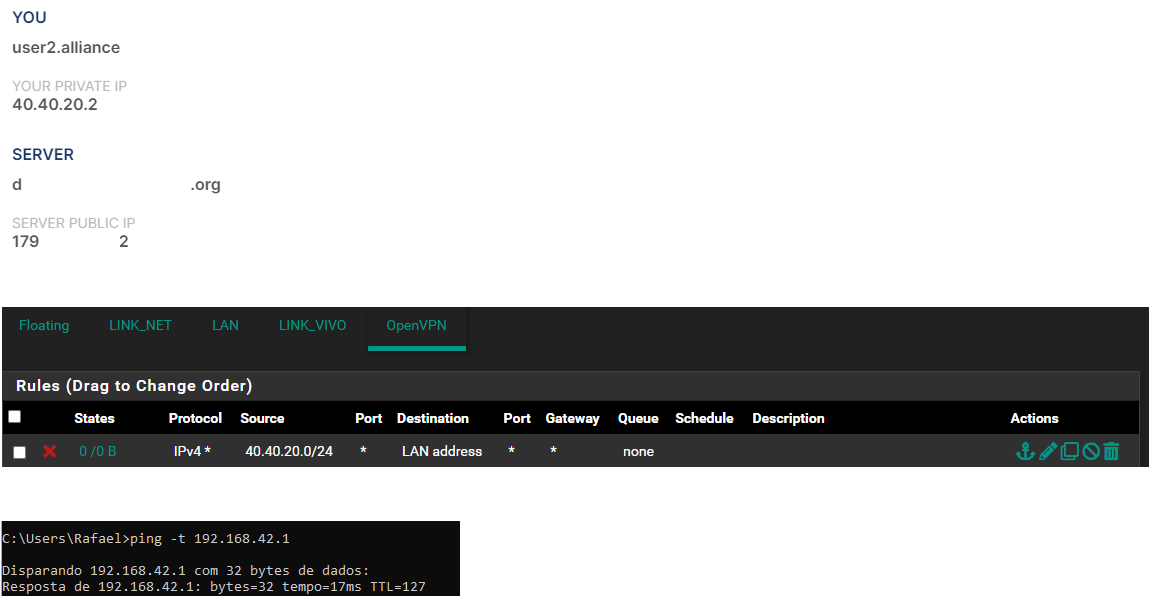
code_textwhat is wrong? As I mentioned there are two different OPENVPN servers in my pfsense in different tunnels, but it seems that pfsense doesn't understand the rule. -
Is that his LAN address or his public address? Remember he is coming in through a tunnel.
-
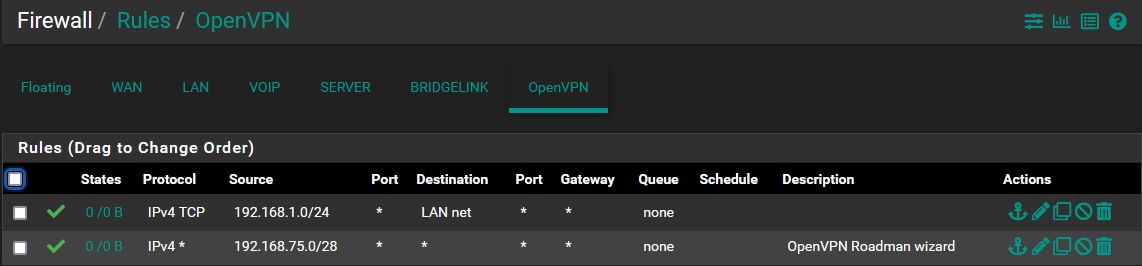
Remember the OpenVPN tab applies to all OpenVPN traffic so you need to tailor rules appropriately. If you assign the servers as interfaces you can apply rules to them separately.
But that block rule is destination LAN address and it probably should be LAN net unless unless you only need to block access the pfSense LAN IP specifically.
If that ping had already been running a state might have existed before you added the rule and would not have been cleared.
Steve
-
192.168.42.0/24 LAN IP
40.40.20.0/24 TUNNEL NETWORK -
@stephenw10
now it worked thanks to everyone the rule was like this, blocking only the origin of the virtual network to which the guy will connect in the case 40.40.20.0/24the other openvpn server of the company's employees accesses everything normally via VPN.
Thanks!