Create firewall rule for specific source / destination
-
I get an ICMP message every two minutes that gets logged, filling it with useless entries. From reading many posts here, I created an entry in /etc/inc/filter.inc that keeps the entry from being logged. However, the next pfsense upgrade will wipe out my fix.
I'm not good at firewall rules, so my question is: how do I recreate the rule in the webGUI so it survives upgrade to upgrade? My Firewall log in the webGUI shows this:
Act Time IF Source Destination
X Dec 21 11:37 WAN 0.0.0.0 224.0.0.1And my rule in /etc/inc/filter.inc is this:
block in quick from 0.0.0.0 to 224.0.0.1 ridentifier {$increment_tracker()} label "Block IPv4 link-local"I'm using pfsense 22.05-RELEASE.
Thanks for your help. -
R rcoleman-netgate moved this topic from webGUI on
-
@ghostnet 224.0.0.1 is multicast traffic. And all traffic on WAN is blocked inbound by default unless you open ports. And those blocks are logged.
You can simply ignore it - I don't pay attention to my WAN logs until I need to troubleshoot why a site-to-site VPN isn't working.
-
I don't pay attention to my WAN logs
Seconding this, we always turn off the "Log packets matched from the default block rules in the ruleset" log setting. Saves a ton of disk writes, doesn't fill the log with spam, and we can turn it on when we need it.
-
I would second turning off logging of the default block. Then create your own rules to log what your interested in - for example I log all SYN traffic to my wan address. And also log common udp ports.
But yeah have no desire to see what amounts to noise..
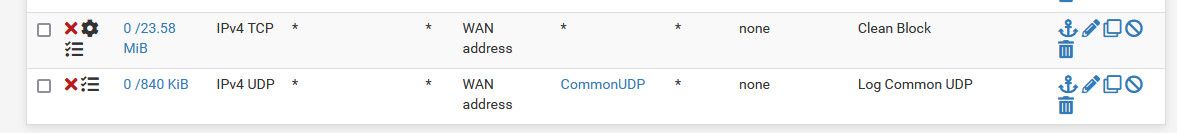
If want to see for some reason - simple click to turn it back on if troubleshooting something for example.
-
That's a reasonable solution for me. However, I don't think there is a default rule to block that (except the kludge I came up with). I was looking for a bit of help constructing the block rule in the webGUI, so the fix would be part of backup / restore and survive upgrades.
-
Looking at the firewall logs from the console, I see that those log entries are marked as blocked, so your solution to disable logging blocked events should work. Thanks for your help.