DNS OVER 443?
-
Hello fellow Netgate Community Members,
I just noticed that there is an increasing amount of protocol hopping going on with DNS and an attempt to utilize port 443 to bypass DNS servers and or DNS based firewalls.
The Internet Assigned Numbers Authority IANA has DNS set for 53 and 853, not for 443.
Please see attached something is no longer following the IANA protocol rules.
chrome.cloudflare-dns.com
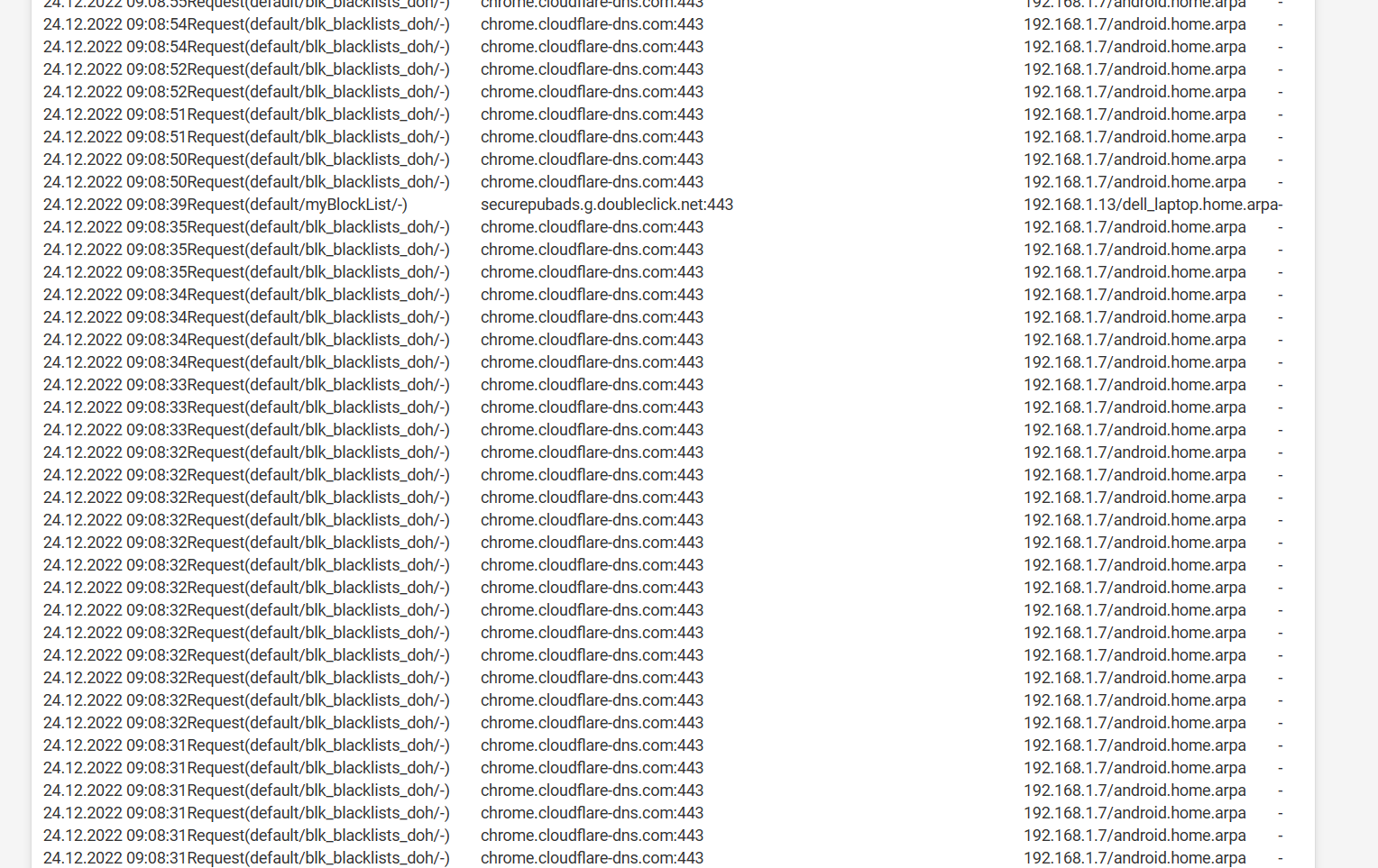
Reference:
"DNS over HTTPS
Similar to DNS over TLS, clients may also use DNS over HTTPS (DoH). This is harder to block as it uses port 443. Blocking port 443 on common public DNS servers may help (e.g. 1.1.1.1, 8.8.8.8).Some browsers automatically attempt to use DNS over HTTPS because they believe it to be more secure and better for privacy, though that is not always the case. Each browser may have its own methods of disabling this feature. Firefox uses a “canary” domain use-application-dns.net by default. If Firefox cannot resolve this name, Firefox disables DNS over HTTPS."
https://docs.netgate.com/pfsense/en/latest/recipes/dns-block-external.html
If you use packages that relay on DNS this may be something of concern.
-
-
@provels I just learned about DOH, is this used to bypass DNS servers I have never seen it in action attempting connections until today. I am glad that Squidguard can spot that HTTP get request for me.
-
@provels
IANA lists DNS over QUIC. They do not list it as DNS over HTTPS however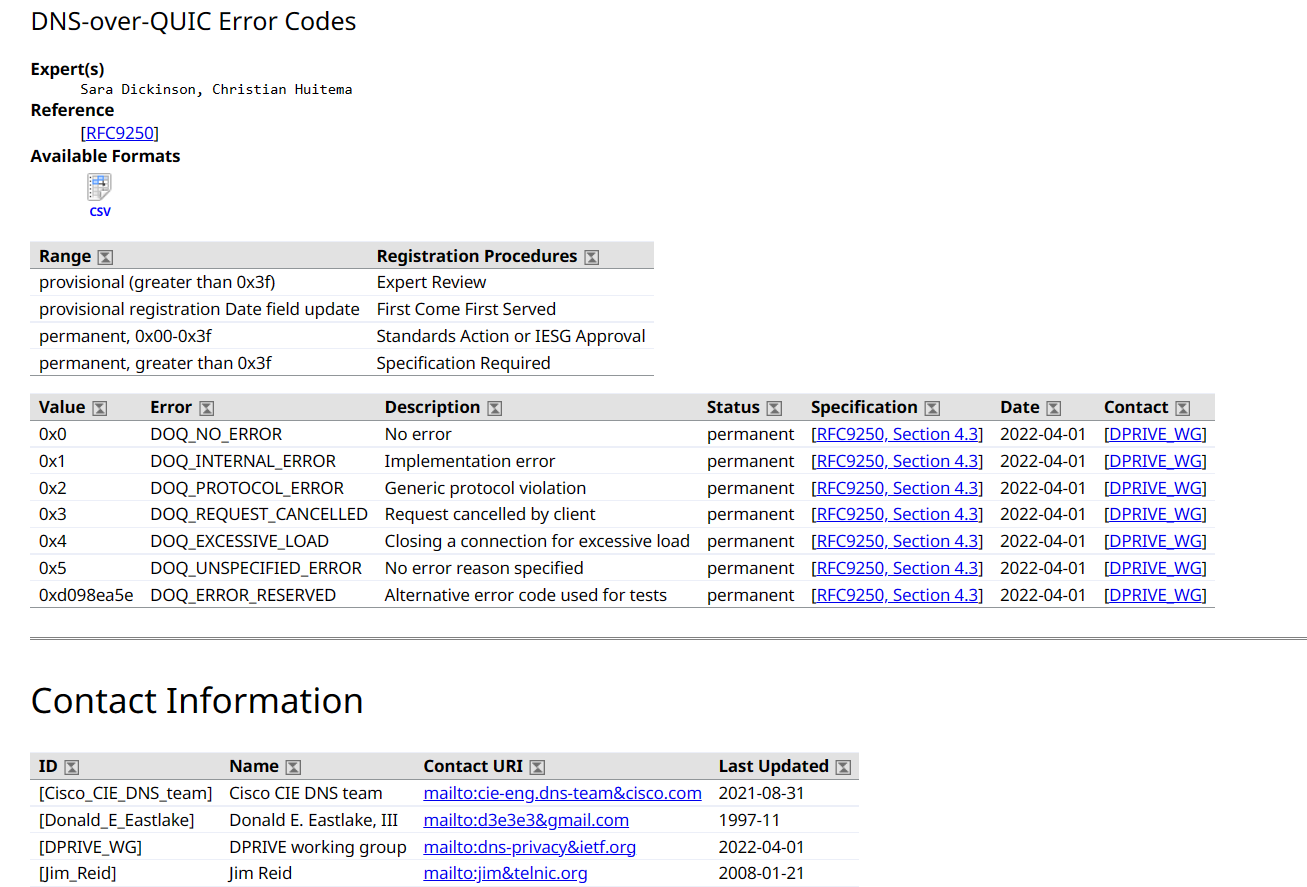
-
@jonathanlee Very difficult to block w/o killing all Internet. I use pfBlockerNG with several DoH blocklists. Can't say I get them all, but some. I think a lot of phones use DoH hardcoded.
-
@provels I just started blocking 443 from accessing DNS servers, This is one of the reasons why I use Squidguard, because even with DNS over https you can see the get requests. The URL filter works great with or without DOH. It's still new to me this type of protocol hopping. It seems as soon as the firewall starts to see items like cdn. and urls that end with .io the backend does anything they can to avoid being logged and spotted with SSL intercept, that is with approved certificates installed. For a while Palo Alto requested that configuration be set to block QUIC. Again now they are finding ways to block out specific QUIC issues, there is a post I seen last week where a PfSense user blocked a URL with QUIC it was really amazing to see the expanding security measures.
-
@provels do you possibly have a list of those known DOH servers that you block?
-
https://raw.githubusercontent.com/bambenek/block-doh/master/doh-hosts.txt https://gist.githubusercontent.com/ckuethe/f71185f604be9cde370e702aa179fc2e/raw/53fe52046836ac3009e9505b7b8b8b5de42d84e3/doh-blocklist.txt https://raw.githubusercontent.com/oneoffdallas/dohservers/master/list.txt https://raw.githubusercontent.com/Sekhan/TheGreatWall/master/TheGreatWall.txt -
@provels Thanks!! Happy Holidays I created two text files from the above URLs to use with Squidguard without the # and the text
DNS over HTTPS "DoH" server text files for use with Squid Guard:
Smaller Lists made from URLS above: dnsdoh.txt
Large List from bulk URL list: DoH DNS List.txt
Combined Lists: CombinedDOHlist.txt
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on