Problems with pfSense IPV6 DNS function (does it exist!?)
-
I still can't reproduce this here. Fresh install, DHCPv6 WAN / Track6 LAN, it boots up and has the prefix for LAN allowed in Unbound, and a client on LAN gets an address and can query it properly.
If that doesn't work I suggest first checking your WAN to make sure you have the correct settings there for DHCPv6 (especially the delegation size), and check to see what is present on the LAN interface(s) and in
/var/unbound/access_lists.conf.There could be some kind of timing issue where the address gets added to LAN but unbound doesn't reload after that, but I'm not aware of anything that would have changed in that scenario specifically.
-
I seem to be running into this REFUSED query response issue as well—or at the least a very similar issue—on the current pfSense Plus
23.01-RCbuild running on my Netgate 6100.Refused IPv6 query output:
Arashi ~ % dig @2600:1700:2320:5fcf:92ec:77ff:fe21:3f06 dns.google. AAAA ; <<>> DiG 9.10.6 <<>> @2600:1700:2320:5fcf:92ec:77ff:fe21:3f06 dns.google. AAAA ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 46011 ;; flags: qr rd ad; QUERY: 0, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; Query time: 57 msec ;; SERVER: 2600:1700:2320:5fcf:92ec:77ff:fe21:3f06#53(2600:1700:2320:5fcf:92ec:77ff:fe21:3f06) ;; WHEN: Mon Feb 13 13:26:40 PST 2023 ;; MSG SIZE rcvd: 12Working IPv4 query output:
Arashi ~ % dig @10.13.1.1 dns.google. AAAA ; <<>> DiG 9.10.6 <<>> @10.13.1.1 dns.google. AAAA ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46994 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1432 ;; QUESTION SECTION: ;dns.google. IN AAAA ;; ANSWER SECTION: dns.google. 900 IN AAAA 2001:4860:4860::8844 dns.google. 900 IN AAAA 2001:4860:4860::8888 ;; Query time: 484 msec ;; SERVER: 10.13.1.1#53(10.13.1.1) ;; WHEN: Mon Feb 13 13:18:02 PST 2023 ;; MSG SIZE rcvd: 95From what I can tell so far, the issue seems to be that expected
access-controllines for the LAN interface are not auto-added the lines for the IPv6 parts of the LAN interface and only generatingaccess-controlentries for the IPv4 LAN network.IPv4 queries function as expected on the LAN, and IPv6 DNS queries on the LAN interface are answered with a
REFUSEDstatus. I checked to see confirm that IPv6 DNS packets were reaching the router past the firewall rules. I further confirmed that by adding in an explicit firewall rule to allow it at the top of the LAN list to confirm that again.uname -voutput:FreeBSD 14.0-CURRENT #0 plus-RELENG_23_01-n256016-ee43ebe4124: Wed Feb 8 14:43:16 UTC 2023 root@freebsd:/var/jenkins/workspace/pfSense-Plus-snapshots-23_01-main/obj/amd64/B5BT22YU/var/jenkins/workspace/pfSense-Plus-snapshots-23_01-main/sources/FreeBSD-src-plus-RELENG_23_01/amd64.amd64/sys/pfSenseCurrent pfSense settings:
- My WAN interface is using
DHCP6for IPv6, and my LAN is in theTrack Interfacetype withWANset as the IPv6 Interface to track. - The
Disable Auto-added Access Controlfor the DNS Resolver is not checked. - The DNS Resolver (unbound) daemon is configured to listen on ALL interfaces.
- DHCPv6 Server is enabled on the LAN with a delegated prefix length of 64, and the Router Advertisements mode is set to
AssistedandUse same settings as DHCPv6 serveris enabled/checked. - Looking at the generated
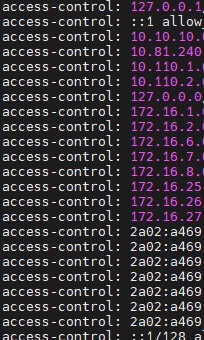
/var/unbound/access_lists.conffile, it appears to have only generated IPv4access-controllines. I do not see any lines for the LAN IPv6 delegated prefix.
[23.01-RC][root@pfSense-ng6100.home.arpa]/root: netstat -an | grep -E '\.53\b' tcp4 0 0 *.53 *.* LISTEN tcp6 0 0 *.53 *.* LISTEN udp4 0 0 *.53 *.* udp6 0 0 *.53 *.*[23.01-RC][root@pfSense-ng6100.home.arpa]/root: cat /var/unbound/access_lists.conf access-control: 127.0.0.1/32 allow_snoop access-control: ::1 allow_snoop access-control: 10.13.1.0/24 allow access-control: 127.0.0.0/8 allow access-control: ::1/128 allow - My WAN interface is using
-
Is there a way I can enable/view logs for the generated auto-added access control items?
For now, I can workaround the missing IPv6
access-controllines for the DNS access lists by adding a customAllowaccess list entry in the DNS Resolver settings to cover my current/64LAN delegated prefix, but that workaround is brittle and would break if my delegated prefix changes at any point.[23.01-RC][root@pfSense-ng6100.home.arpa]/root: cat /var/unbound/access_lists.conf access-control: 127.0.0.1/32 allow_snoop access-control: ::1 allow_snoop access-control: 10.13.1.0/24 allow access-control: 127.0.0.0/8 allow access-control: ::1/128 allow #Custom IPv6 Allow Workaround access-control: 2600:1700:2320:5fcf::/64 allowWorking query with workaround:
Arashi ~ % dig @2600:1700:2320:5fcf:92ec:77ff:fe21:3f06 dns.google. AAAA ; <<>> DiG 9.10.6 <<>> @2600:1700:2320:5fcf:92ec:77ff:fe21:3f06 dns.google. AAAA ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6924 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1432 ;; QUESTION SECTION: ;dns.google. IN AAAA ;; ANSWER SECTION: dns.google. 900 IN AAAA 2001:4860:4860::8844 dns.google. 900 IN AAAA 2001:4860:4860::8888 ;; Query time: 378 msec ;; SERVER: 2600:1700:2320:5fcf:92ec:77ff:fe21:3f06#53(2600:1700:2320:5fcf:92ec:77ff:fe21:3f06) ;; WHEN: Mon Feb 13 13:31:02 PST 2023 ;; MSG SIZE rcvd: 95 -
 B Bob.Dig referenced this topic on
B Bob.Dig referenced this topic on
-
@jimp I was triggered by your DHCP-PD size. My ISP provides a full /48 within PPPoE.
Then it should be configured as SIZE: 48?
More screenshots here https://forum.netgate.com/topic/177863/23-01-unable-to-answer-dns-queries-after-upgrade/26?_=1676570089641
@jimp said in [Problems with pfSense IPV6 DNS function (does it
If that doesn't work I suggest first checking your WAN to make sure you have the correct settings there for DHCPv6 (especially the delegation size)
-
I was finally able to find a box in my lab that hit this, so I was able to find out what was happening there. I reopened https://redmine.pfsense.org/issues/13851 for it.
I don't know how/why I wasn't hitting it on more things, but apparently most of the boxes I was checking for IPv6 had specific local bindings and were not set to "all" for the local network interface.
You can install the System Patches package and then create an entry for
46b159032fef8c78783aa1a749d2238cfed7ac0dto apply the fix. -
@jimp said in Problems with pfSense IPV6 DNS function (does it exist!?):
I was finally able to find a box in my lab that hit this, so I was able to find out what was happening there. I reopened https://redmine.pfsense.org/issues/13851 for it.
I don't know how/why I wasn't hitting it on more things, but apparently most of the boxes I was checking for IPv6 had specific local bindings and were not set to "all" for the local network interface.
You can install the System Patches package and then create an entry for
46b159032fef8c78783aa1a749d2238cfed7ac0dto apply the fix.Thanks for the quick fix that looks way better!
-
@jimp said in Problems with pfSense IPV6 DNS function (does it exist!?):
46b159032fef8c78783aa1a749d2238cfed7ac0d
That fix worked for me too, took some seconds after the reboot that I did.
PS C:\Users\Bobby> nslookup reddit.com fd7b:97bf:48b9:100:192:168:100:1 Server: pfSense.home.arpa Address: fd7b:97bf:48b9:100:192:168:100:1 Non-authoritative answer: Name: reddit.com Addresses: 2a04:4e42:200::396 2a04:4e42::396 2a04:4e42:600::396 2a04:4e42:400::396 151.101.193.140 151.101.129.140 151.101.65.140 151.101.1.140 -
 B Bob.Dig referenced this topic on
B Bob.Dig referenced this topic on
-
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on
-
@jimp said in Problems with pfSense IPV6 DNS function (does it exist!?):
46b159032fef8c78783aa1a749d2238cfed7ac0d
If we're using 2.7 should we apply this patch?
-
@jimbob-indiana said in Problems with pfSense IPV6 DNS function (does it exist!?):
@jimp said in Problems with pfSense IPV6 DNS function (does it exist!?):
46b159032fef8c78783aa1a749d2238cfed7ac0d
If we're using 2.7 should we apply this patch?
You can for now, once we have dev snapshots building again you can just upgrade to the latest snapshot and get the fix. Or you could gitsync, but that's more risky.
-
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on
-
I applied the
46b159032fef8c78783aa1a749d2238cfed7ac0dcommit patch and can add my own confirmation to the group that the generated DNS access lists are working as expected.I want to personally thank you @jimp for the work you put into this. :D I'm sure you've been busy with more higher-priority work related to the 23.01 release with how monumental of a change it really is. Changing both the PHP major version platform and language differences at the same time as re-basing work with skipping the entire FreeBSD 13.x series and going straight to the FreeBSD 14 code branch. That's no small feat to change both of those in a single release target, so bravo!
-
N netgate_etagten referenced this topic on