Looking for advice on how to "securely" expose a personal minecraft server on the internet
-
Hi All,
I am quite new so apologies in advance if some of the questions are simple or outright silly.Requirement:
Setup a Minecraft server that is exposed to the internet in a secure manner. The server will only be used by friends and family.My existing setup
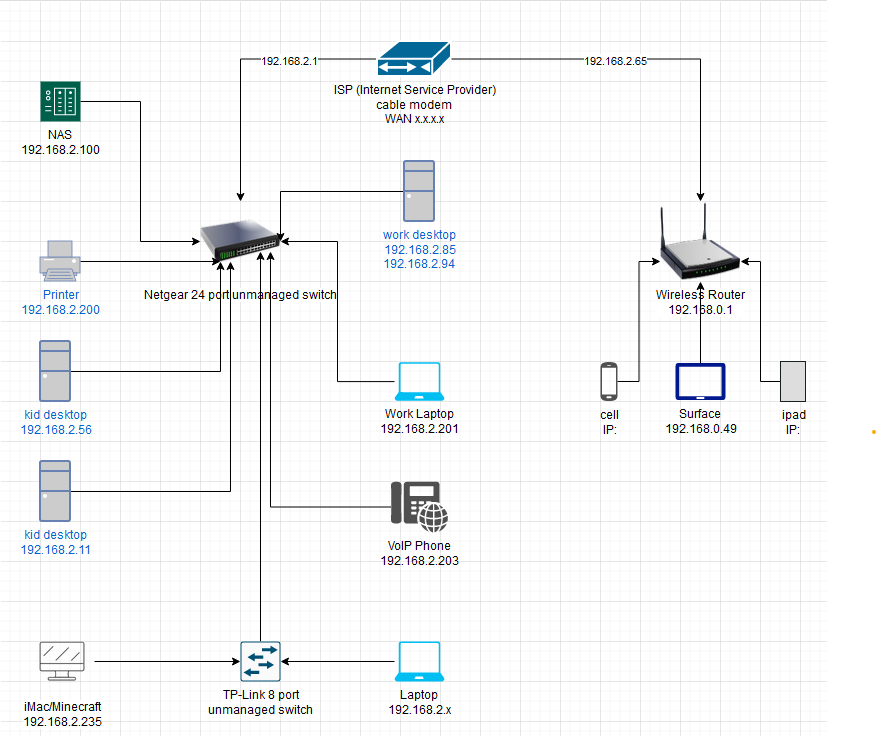
To begin, I did some research and settled on the Netgate 2100. I bought the base model with 8 GB of storage and will be upgrading it to 256 GB.
Experimental setup after installing the Netagate 2100
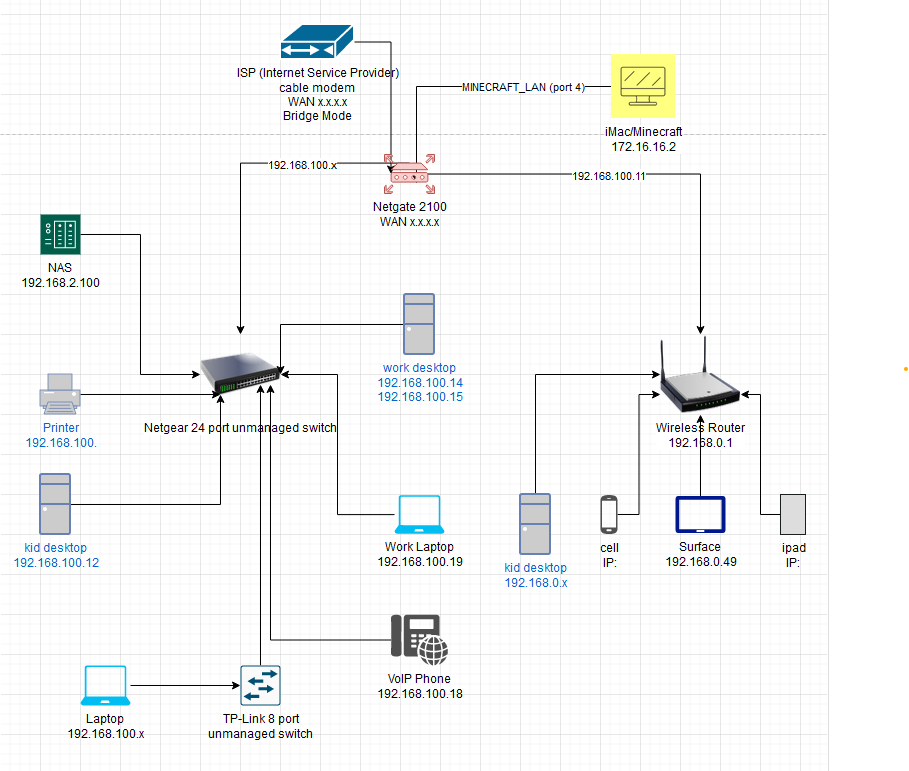
My approach
- Create a new segregated network MINECRAFT_LAN (used port 4) using the instructions in the video Configuring Netgate Appliance Integrated Switches on pfSense 2.4.4
- Connect the iMac/Minecraft machine directly to the MINECRAFT_LAN (Netgate port 4)
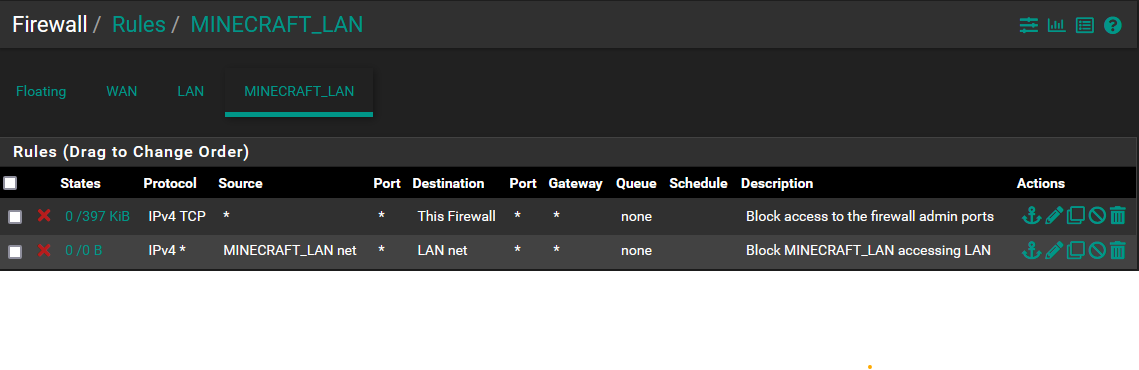
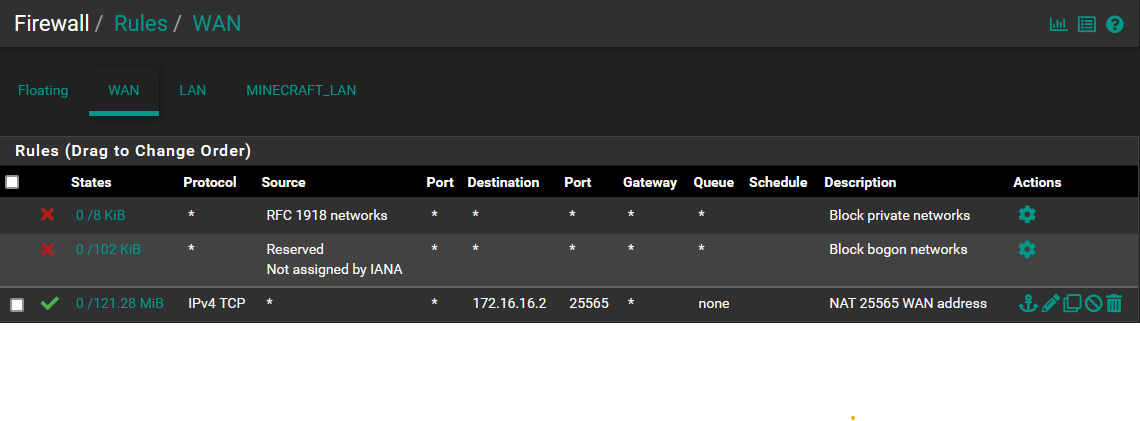
- Setup firewall rules to block all traffic from MINECRAFT_LAN to all other networks (Port 1, 2 and 3) using the video Basic Setup and Configuring pfsense Firewall Rules For Home . Rules for the network 192.168.1.0/24 NSFW_LAN were applied to MINECRAFT_LAN
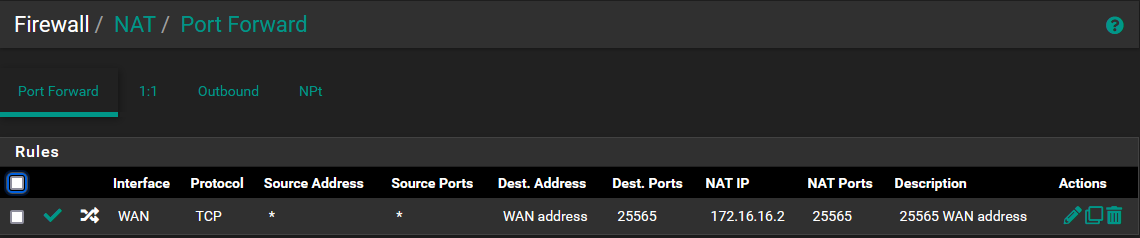
- Setup Port Forwarding (Netgate 2100 --> Firewall --> NAT --> Port Forward) so that traffic will only be sent to a single host 172.16.16.2:25565
Testing
- Successfully connected to the Minecraft server (offline mode) from the 192.168.100.x network. In offline mode, the Minecraft server does not authenticate the user joining the server.
- Successfully connected to the Minecraft server (offline mode) using the WAN IP. This works because I have turned on NAT reflection. (Netgate 2100 GUI --> System --> Advanced --> Firewall & NAT --> Network Address Translation --> NAT Reflection mode for port forwards --> Pure NAT)
- Successfully connected to the Minecraft server (offline mode) from the internet
Issues
- Minecraft server is not able to the connect to the Microsoft/MOJANG authentication server
Questions:
- Is my approach secure enough so that even if the Minecraft host is compromised, it will not impact the other network?
- Will creating a DMZ and putting the Minecraft server in the DMZ a better approach?
- How do I debug the issue of the iMac/Minecraft server not being able to authenticate to the Microsoft/Mojang server?
Reference:
iMac/Minecraft server: 172.16.16.2:25565
Minecraft: Minecraft Java edition version 1.18.2
pfsense version: 22.05-RELEASE (arm64)
Router: Netgate 2100
WAN Firewall rules:
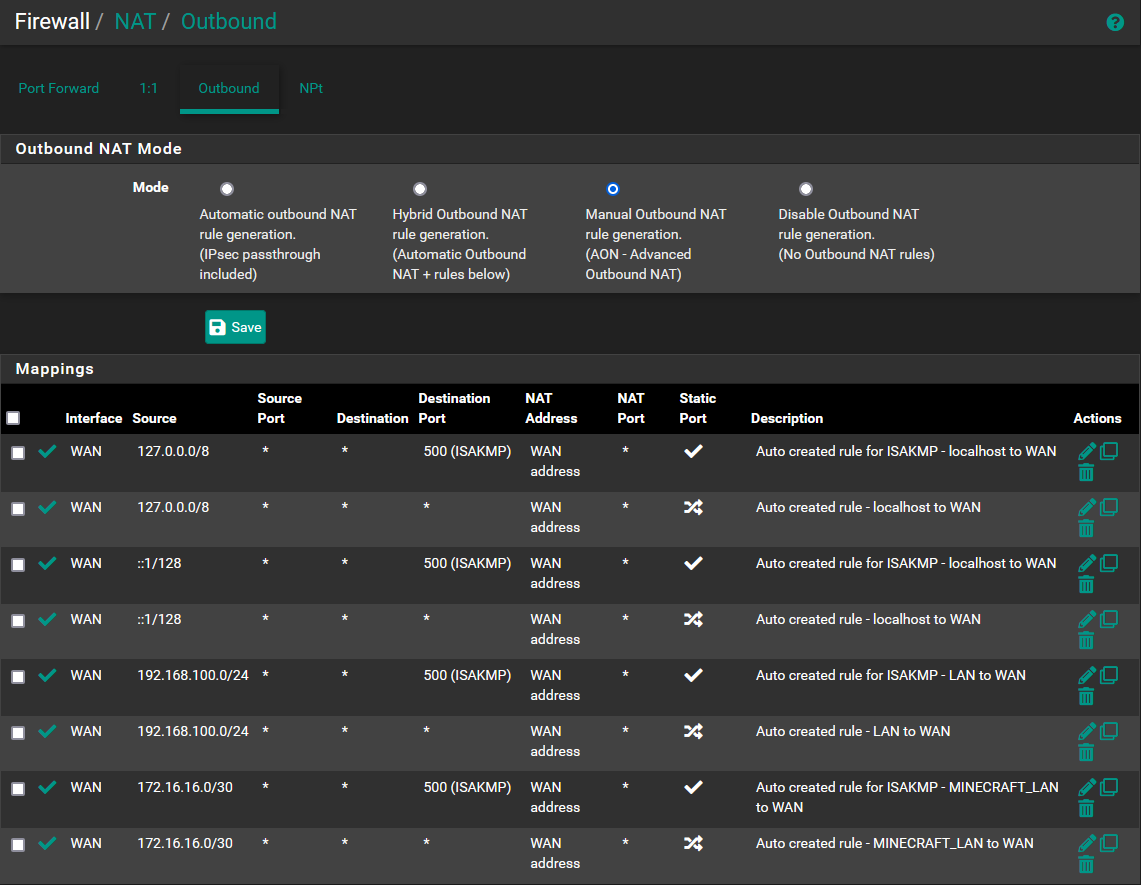
Firewall --> NAT --> Outbound rules:
-
@backspacemild said in Looking for advice on how to "securely" expose a personal minecraft server on the internet:
Setup a Minecraft server that is exposed to the internet in a secure manner. The server will only be used by friends and family.
- Put it on it's own /29 or /30 network segment
- Do not allow it to talk to anything BUT the internet directly
- Allow only things on your network that need to talk to it.
That's the only real way to secure it AND be able to use it from your network.
Emphasis on #2. If you tell the interface rules to not allow that interface/network to talk to anything that is an RFC1918 address (an alias you would make) then it cannot initiate any requests over the network. Putting it into a small subnet means you can lock it's broadcast domain to itself and the firewall without worrying about it finding the info of it's IP neighbor.
-
@backspacemild Thank you.