Starlink with SG6100
-
Hi All,
I've ran into a bit of a snag trying to setup my SG6100 on Starlink. I'm going from pfSense to the Starlink Router since bypass mode was giving me even more issues. So currently, the setup looks like this.
LAN <--> Unifi Switch <--> (LAN) pfSense (WAN) <--> (via Ethernet Adapter) Starlink Router
(No VLANS)
Once everything is connected and fired up the pfSense WAN interface gets an 192.168.1.81 IP Address with a gateway of 192.168.1.1 from the Starlink Router. I can ping 1.1.1.1 from the WAN Interface but not the LAN Interface. The LAN interface is setup with 10.5.11.0/24 and the LAN Interface IP is 10.5.11.1/24
That makes me think something is up with NATing but nothing I've tried has helped, perhaps I'm doing it wrong?
I also doubled checked the GW and Default routes and it has a 0.0.0.0/32 pointing to 192.168.1.1. And I have also turned off "Block Private Networks and Loopback Addresses".
I've got Any Any Firewall rules for both LAN and WAN just to rule that out. Will be fixed later.
I'm fairly new to the nuances of Starlink so any help is appreciated.
-
@xineo Double NAT should work out of the box, for connecting from LAN to the Internet. Can you ping/traceroute from the Diagnostics menu?
-
@steveits From the Diagnostics menu I can ping 1.1.1.1 from the WAN but the LAN side fails. I can ping anything on the LAN side from the LAN interface just nothing WAN Facing.
-
@xineo How far does a traceroute from LAN get?
Is NAT outbound set to automatic?
-
@steveits it is.
-
And do you see an auto outbound NAT rule created for 10.5.11.0/24 on the WAN?
Is your WAN using DHCP to get it's address from the Starlink router?
-
@stephenw10 Yes, wan is using DHCP and is pulling an ip address of 192.168.1.81 from Starlink, since that's a private I made sure to turn off "Block Private Networks and Loopback Addresses".
pfsense is getting the Automatic NAT Rules for WAN. I will be back at the site today to try some more things.
-
@xineo said in Starlink with SG6100:
I made sure to turn off "Block Private Networks and Loopback Addresses".
Just for reference that affects inbound traffic on WAN so wouldn't affect outbound, getting a DHCP address, accessing the Starlink router IP, etc.
Did you try the traceroute?
Out of the box it should just work in this config.
-
@stephenw10
@SteveITS
I'm at the site and went over the config again, everything looks good until I went into the firewall logs and saw this block coming from my address.Jan 11 10:36:05 LAN Default deny rule IPv4 (1000000103)
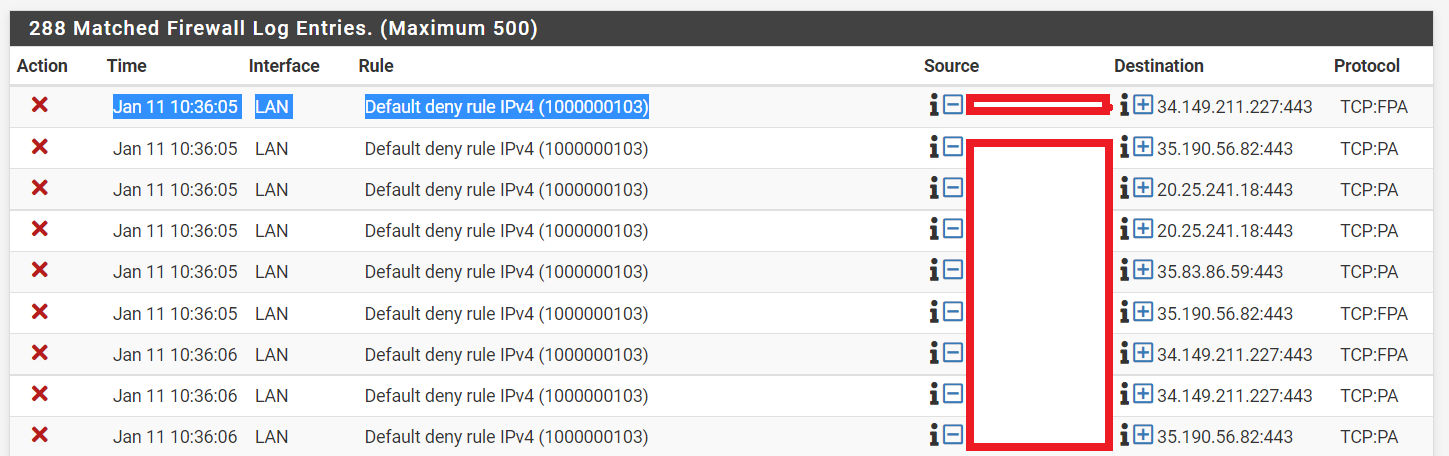
That's really strange because I have a Top Level 'Any Any' Rule on the LAN Interface so nothing should be getting blocked.
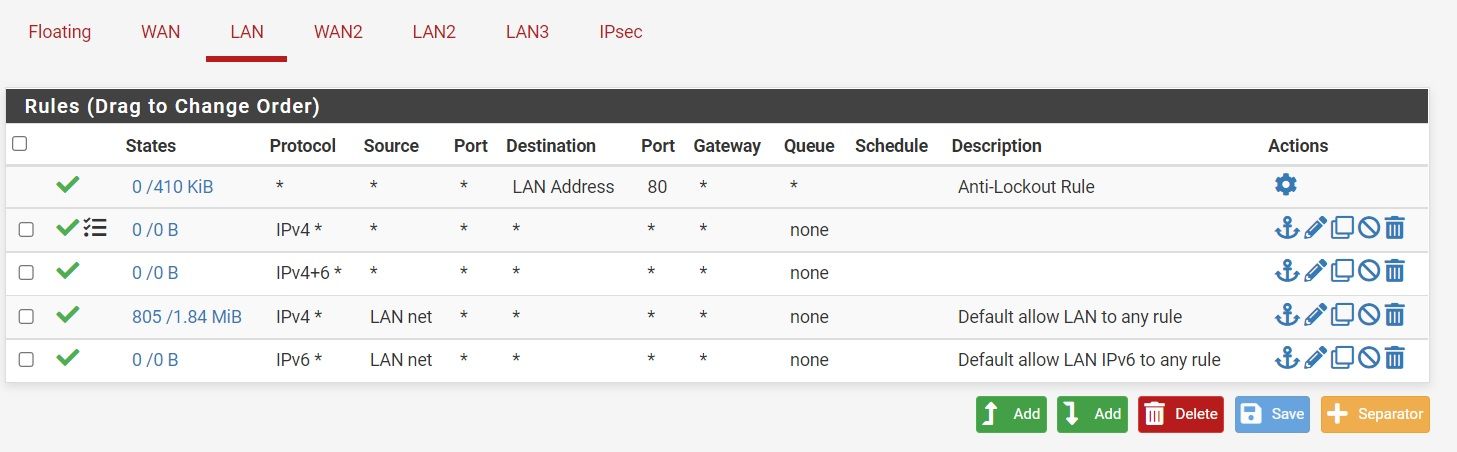
It's also blocking Locals on WAN despite having that turned off.
-
Those blocks with PA and FPA look like some type of traffic that got sent after the firewall had already closed the stateful connection out in its table. It happens sometimes. Or maybe a connection that was dormant too long and the state entry timed out. Probably not really a blocked connection.
-
Those are all TCP ACK packets so they are blocked either because the state has already closed or because you have some asymmetric routing:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.htmlWhat do you see blocked on WAN?
-
@stephenw10 Issue turned out to be a Traffic Shaper that I didn't realize was setup. Thank you all for your help.