pfSense Plus can't work with Google LDAP
-
Google recently changed to require SNI for LDAP, and the OpenLDAP client on pfSense Plus didn't support that yet (#11626).
The client in the upcoming 23.01 release has been upgraded so it should work again there. If you are comfortable running a snapshot, you could try out the latest 23.01 beta snapshot and see if it works for you there.
-
@jimp Thanks!!!
I will try update to 23.01 beta.
Another question: pfSense 23.01 will be run over FreeBSD 14.0?
https://docs.netgate.com/pfsense/en/latest/releases/versions.html
Regards
-
@marceloengecom said in pfSense Plus can't work with Google LDAP:
Another question: pfSense 23.01 will be run over FreeBSD 14.0?
It's built on FreeBSD main, currently 14.
23.01-BETA (amd64) built on Fri Jan 06 06:04:43 UTC 2023 FreeBSD 14.0-CURRENT -
Hello,
I updated it to 23.01-BETA, but the same error remains.
"Could not connect to the LDAP server. Please check the LDAP configuration."
-
I just double checked again with a packet capture and the LDAP client is definitely sending SNI in its SSL requests now so if yours isn't working then it isn't related to the Redmine issue I linked above.
You might try taking a packet capture of the LDAP attempt and opening it up in Wireshark, you might notice something off in the exchange that may give you a hint.
Or it might be a mismatch of some sort between the client certificate you've picked in the LDAP settings and what Google expects. Hard to say from the error it gave. Google has a bunch of docs on how it all works, though.
We have some debug options in for LDAP now but they are more focused on the query part, not the connection part, so they are probably not too helpful. You can still try, though, by going to Diag > Auth in the GUI, pick the Google LDAP entry, enter a user/pass, check debug, then click Test. Afterward, look in the main system log and see what it shows.
-
Hello!
The Authentication field (Diag > Auth in the GUI), don't show anything on the system logs.
The packet capture, after tryed connect with unsucess, return the folowing image:
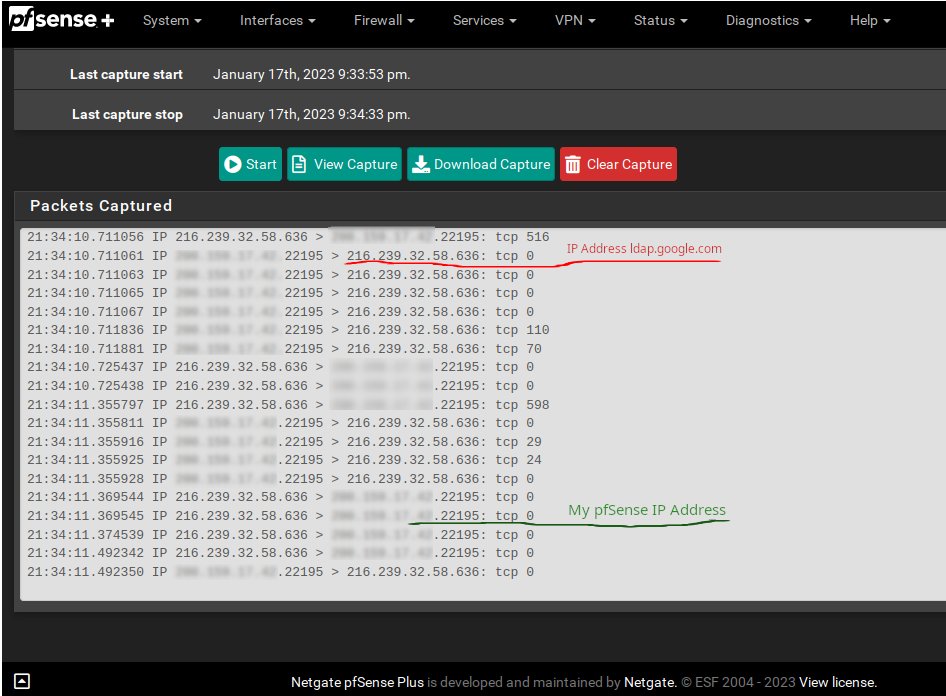
-
Hi @jimp
This is work with stunnel. Now I can authenticate in pfSense and Captive Portal, but dooes not work with my Proxy Squid.
Squid Authentication General Settings:
Authentication Method: LDAP
Authentication Server: 127.0.0.1
Authentication server port: 1636Squid Authentication LDAP Settings
LDAP version: 3
Transport: TCP - Standard
LDAP Server User DN: UserBindGoogleCredentials
LDAP Password: PasswordBindGoogleCredentials
LDAP Base Domain: Base DN: dc=MyDomain,dc=com,dc=br
LDAP Username: uid
LDAP Search Filter: uid=%sCan I help me?
Regards,
-
Since it didn't work in Squid, I'm trying again whith pfSense 23.01-BETA native authentication.
The following error are showed in logs:
/system_authservers.php: ERROR! ldap_get_user_ous() could not bind to serverRegards,
-
@jimp I Just had this issue.
pfSense Plus 23.05.1 would not connect to Google LDAP following the documented pfSense Plus configuration: https://docs.netgate.com/pfsense/en/latest/recipes/auth-google-gsuite.html
Followed the CE/Community edition instructions using Stunnel worked first time!
-
Was that the first time you tried to configure it? Was it working in 23.05 and then fail when you upgraded for example?
-
@stephenw10 Yes, that was the first time. I did not try using Google LDAP until after I upgraded to 23.05.1.