<Solved> - IPsec IkeV2 Cisco ASA will ony activate first P2 SA
-
To get some experience with pfSense IPsec , i was toying around with pfSense IPsec , and a little Cisco ASA 5506X
I have selected to install an extra pfSense as an "IPsec terminating box", and do static routes to/from the main pfSense via an "Interconnect DMZ" , connected to both fwall's.
I basically followed this guide for the ASA
https://www.petenetlive.com/KB/Article/0001429pfSense setup straight "out of the box" , on both P1 & P2 Setup.
I used most as default ...I have 3 P2's defining 3 different PBX subnets behind the main pfSense.
P1
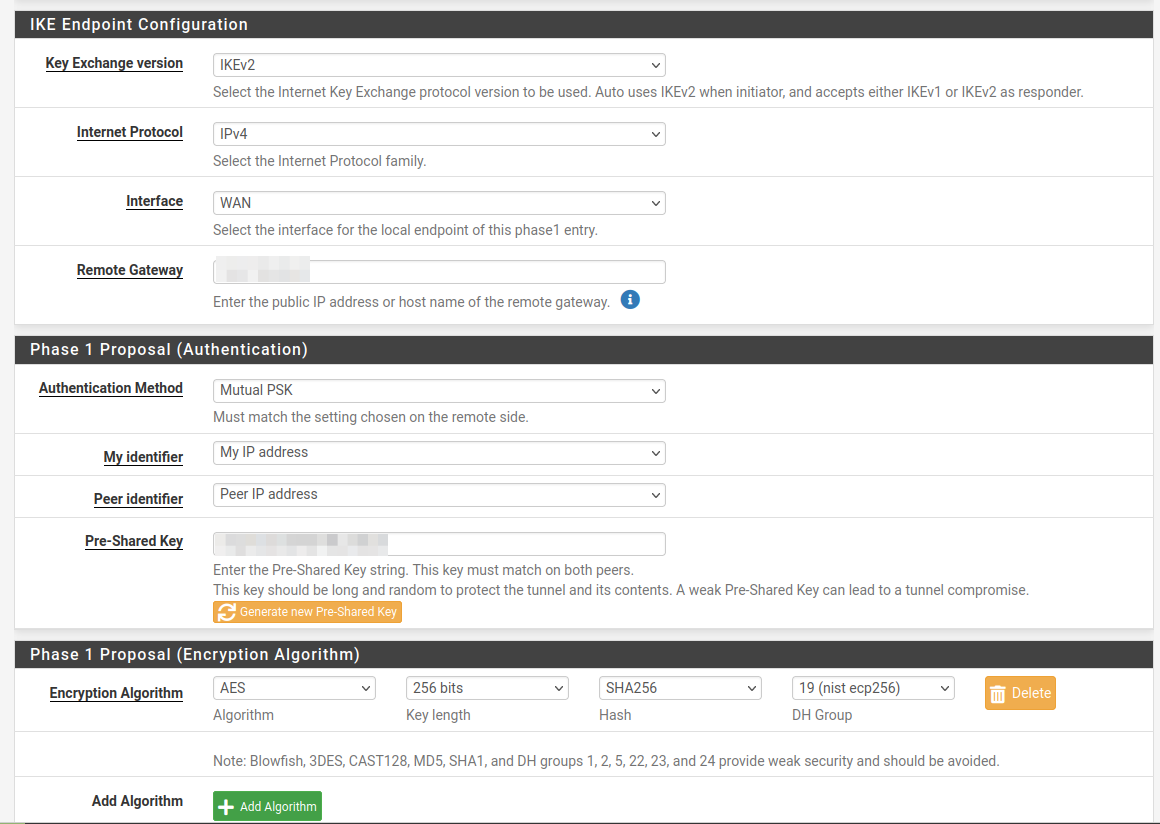
P2
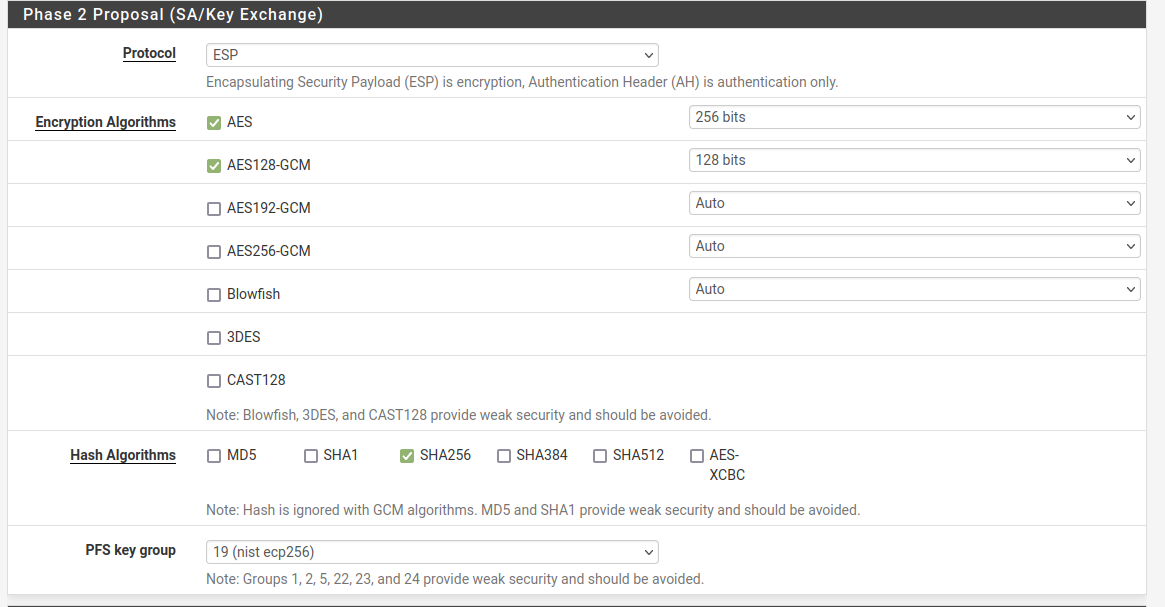
The other two P2's setup same way , just other "Network lan's"
"Everyhing" worked fine for the first P2.
My Cisco phones (behind the ASA) connected to the PBX behind the main pfSense.But i couldn't activate the other P2's.
It turned out that the above ASA example missed one command on the ASA
This one:
crypto map CRYPTO-MAP 1 set pfs group19After adding that one , all 3 P2's would activate.
But why did the first P2 activate without that command ???
Is there some default/special handling of the first P2 ?Working ASA IPSEC commands
! object network partner-local subnet 10.259.2.0 255.255.255.0 object network telelab-remote-cisco subnet 192.168.8.0 255.255.255.0 object network telelab-remote-pbx1 subnet 10.13.6.0 255.255.255.0 object network telelab-remote-avaya subnet 10.13.7.0 255.255.255.0 object-group network telelab-remote network-object object telelab-remote-cisco network-object object telelab-remote-pbx1 network-object object telelab-remote-avaya access-list crypto-to-telelab extended permit ip object partner-local object-group telelab-remote ! ! crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside ! ikev2 local-authentication pre-shared-key ! tunnel-group <remote peer ip> type ipsec-l2l tunnel-group <remote peer ip> ipsec-attributes ikev2 remote-authentication pre-shared-key 0 <super secret key> ikev2 local-authentication pre-shared-key 0 <super secret key> isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-256 ! crypto map CRYPTO-MAP 1 match address crypto-to-telelab crypto map CRYPTO-MAP 1 set pfs group19 crypto map CRYPTO-MAP 1 set peer <remote peer ip> crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside !/Bingo
-
@bingo600 said in <Solved> - IPsec IkeV2 Cisco ASA will ony activate first P2 SA:
But why did the first P2 activate without that command ???
Is there some default/special handling of the first P2 ?Yes, there is.
When connecting, the first P2 SA entry uses DH information from the parent P1, and not its own PFS value. This isn't specific to pfSense, it's part of how IPsec operates.
It will use the P2 PFS value for the additional P2 entries and also when rekeying, so it may have failed to stay established over time as well.
You'll see this sometimes on the IPsec status when a tunnel connects first and it doesn't show the PFS value in the P2 status for the first configured P2 initially, but it will after a while when the tunnel rekeys.