23.01.b.20230106.0600 IGMP proxy stops TV stream
-
@michiel nee dat is te complex als je niet zelf de TV beidend. Ik wil wel 1 poging doen, dan moet je een packetcapture maken op de VLAN interface waar je TV op kijkt. Full aanvinken en Count op 0 en dan de juiste TV interface selecteren.
Daarna kan je die file delen met mij, niet te lang wachten met zappen want het wordt dan een (te) groot bestand.
Net getest en als ik live tv pauzeer dan druk ik op play, en dan start hij na een seconden of 6 foutloos.
Je kan ook nog in je firewall logs kijken of daar iets wordt geblokkeerd vanuit de source interface van je TV interface.
-
@michiel I dove into the issue and I think I might have found a solution.
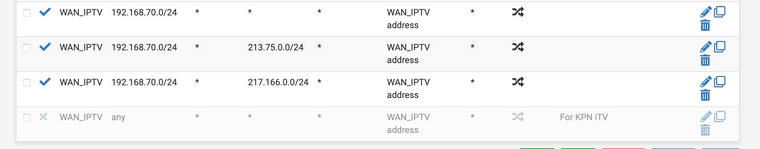
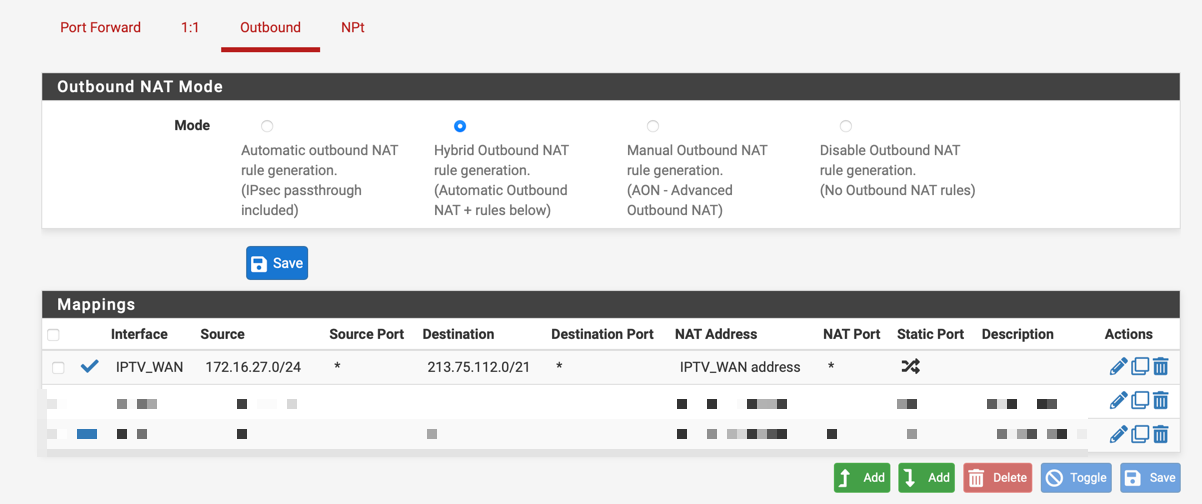
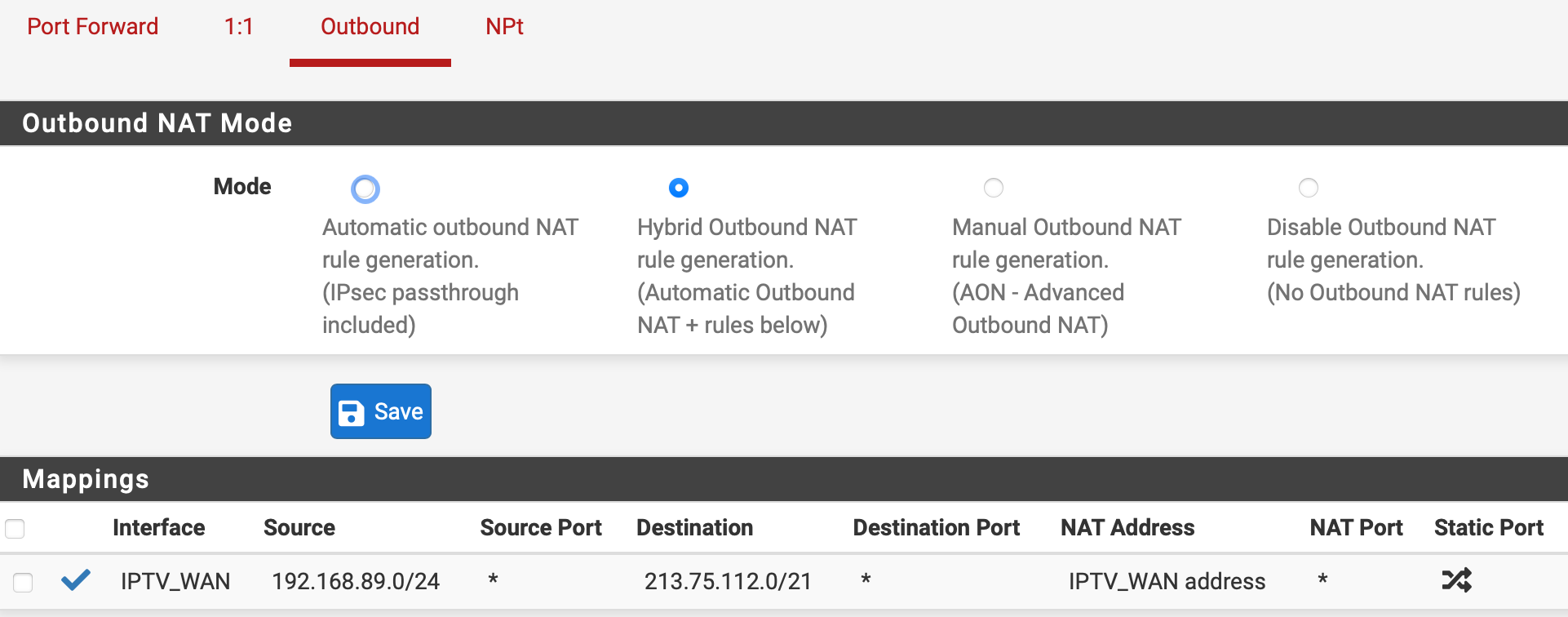
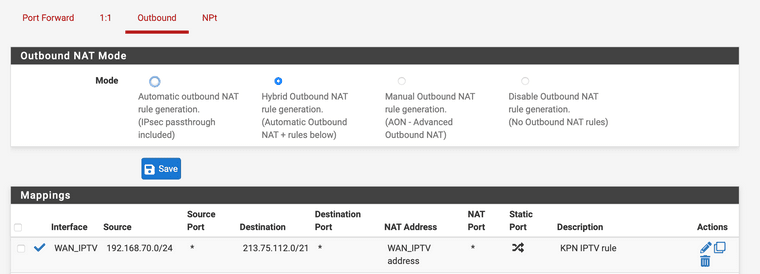
These are my adjusted mappings under NAT --> Outbound based on the blogpost I found from the travelling tech guy, where his NAT rules were different than mine.
https://travellingtechguy.blog/using-your-own-pfsense-router-with-kpn-fiber-and-kpn-itv/
Initially I had only the bottom mapping. I disabled it, and replaced them with the three topmost rules based on the blog post. Until now this seems to have fixed the issue for me, but I need some more testing. Can't do too much testing now as the Misses is also watching tv with me
 .
.Obviously you should replace 192.168.70.0/24 with your specific subnet.
-
@haraldinho indeed the NAT is wrong in the first guide, that's what I mentioned with reversed engineered...everyone is making a guide for the clickbait with good intentions.
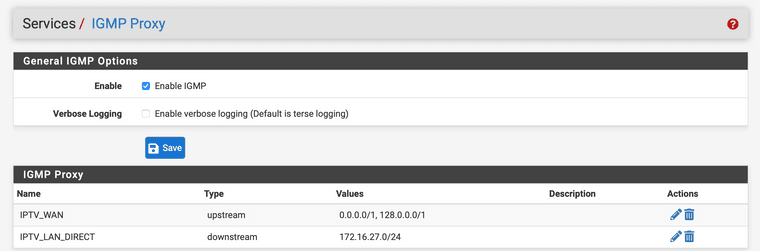
Still the second guide is not 100% correct, in that guide are the commonly used proxy upstream address used in the NAT config. The correct configuration for the proxy is the one from the first guide (in fact 0.0.0.0/0 splitter over two subnets).
The correct NAT rule is the one below, you only need to NAT the traffic to the route you receive from the DHCP advertisement from KPN. And that's a single subnet.
With these both configuration parts you are more persistent to future changes from the ISP side.
-
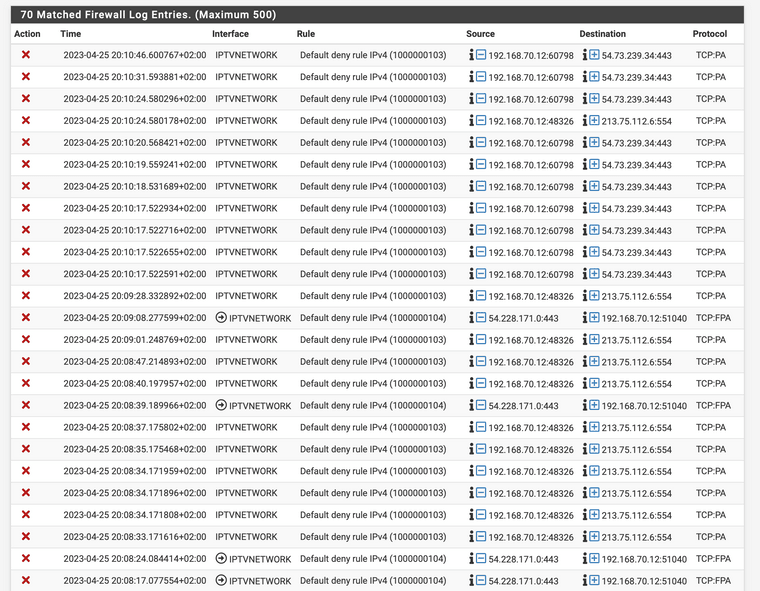
@haraldinho Thank you for diving into this. I added these rules to NAT --> Outbound, but still have the same issue. So I tried the option of @thebear but also that is not working. Live TV pauses and restarts. Recorded programs don't.
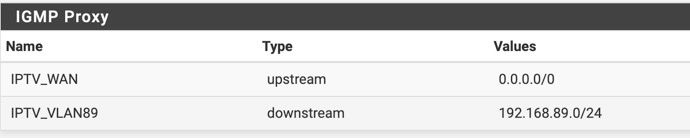
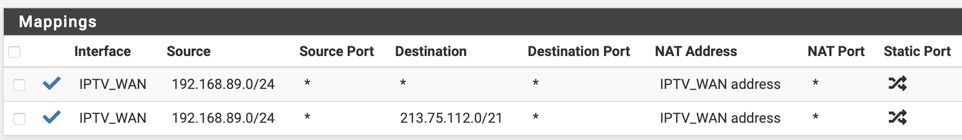
I do see these entries in my logging....
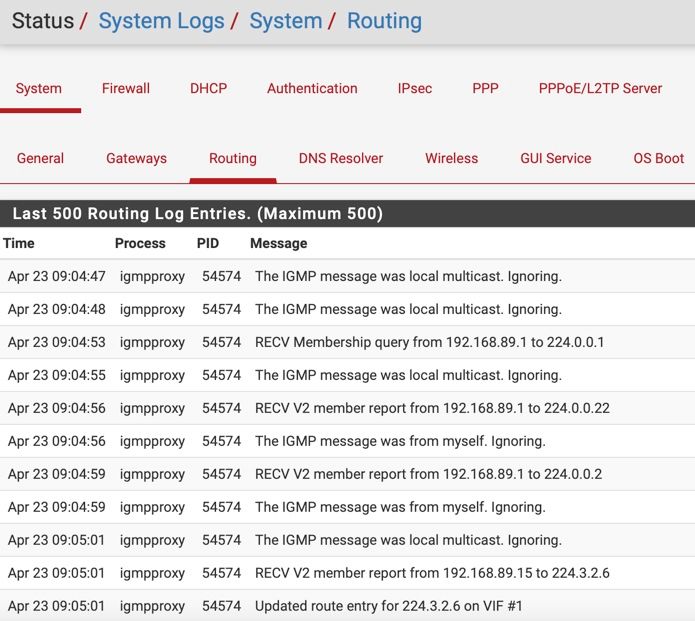
-
-
Now what I did not do yesterday evening because the family was watching tv, I did do this morning: reboot the firewall. But first I changed my settings to those of @thebear from his previous post. And guess what: it appears to work now. I did three tests: pause 5 seconds, pause 5 minutes and pause for 10 minutes. All successfully restarted the recorded stream. @michiel did you do a reboot after changing your settings and if not, can you try that?
-
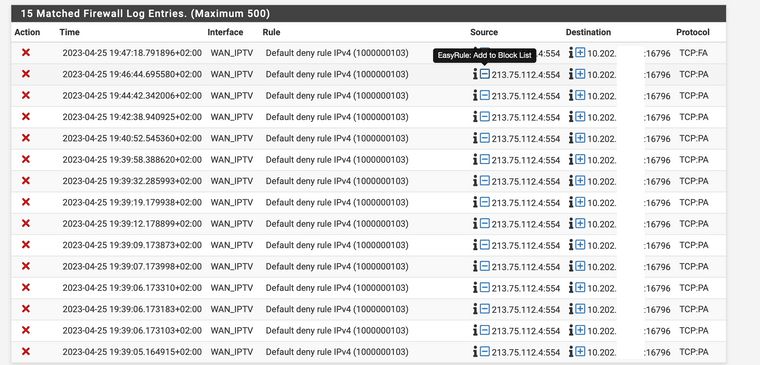
Found some more evidence of what went wrong in the firewall logs:
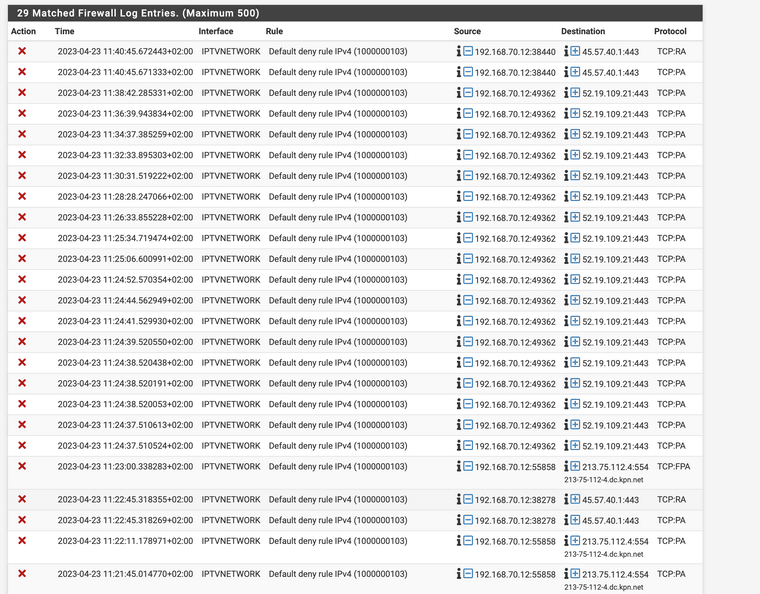
I rebooted my device around 11:21. Before the reboot, you see that some address in the 213.75.112.x range is getting blocked. After the reboot, this block does not appear anymore. I was doing my testing after this period.
Unfortunately and in all honesty, I don't fully grasp all the settings that are required for IPTV, but it appears that the changes I made based on @thebear's settings made a change after the reboot.
I wonder though what the https request are that the box is trying to do and that get blocked... What functionality does this block? Anybody any clue?
-
Ok, pasting 45.57.40.1:443 into a browser leads to a site with a blocked Netflix certificate. So that gives some idea into what the box tries to do. The other IP, 52.19.109.21:443 does not reveal any information as far as I can see.
-
@haraldinho I did several reboots. I noticed earlier that reboots help in applying the firewall rules. I think (not sure) that is has to do with the stating tables?
However, reboot did not solve it. I just applied the exact same settings as @thebear and will reboot later this day. Kids are online now :).You did change the IP addresses to your own VLAN? So where the bear says 127*, you are using 192* in outbound rules and downstream proxy?
-
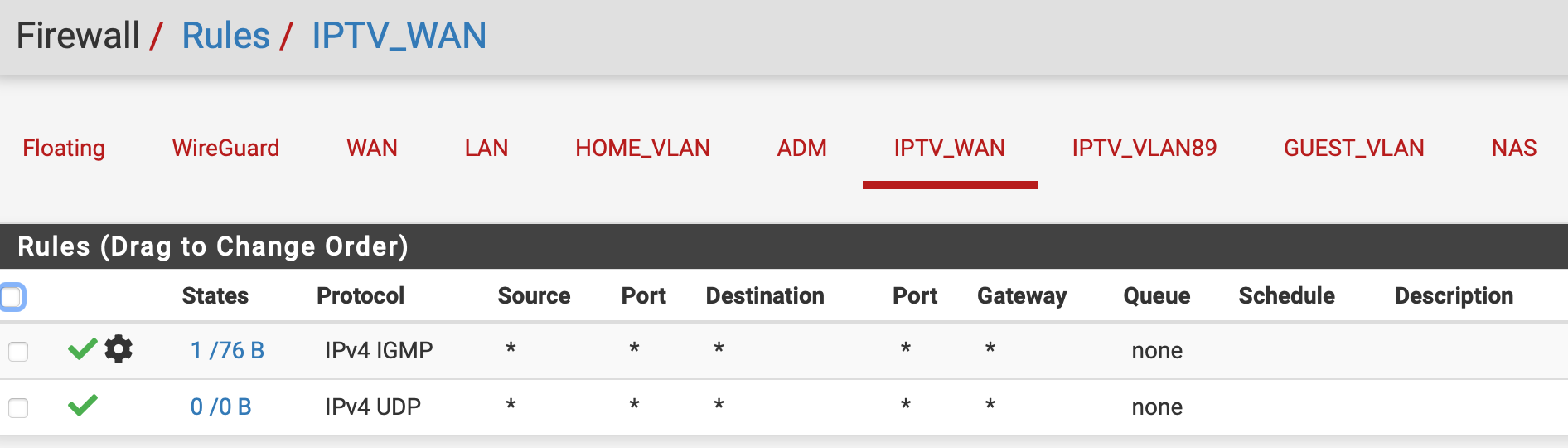
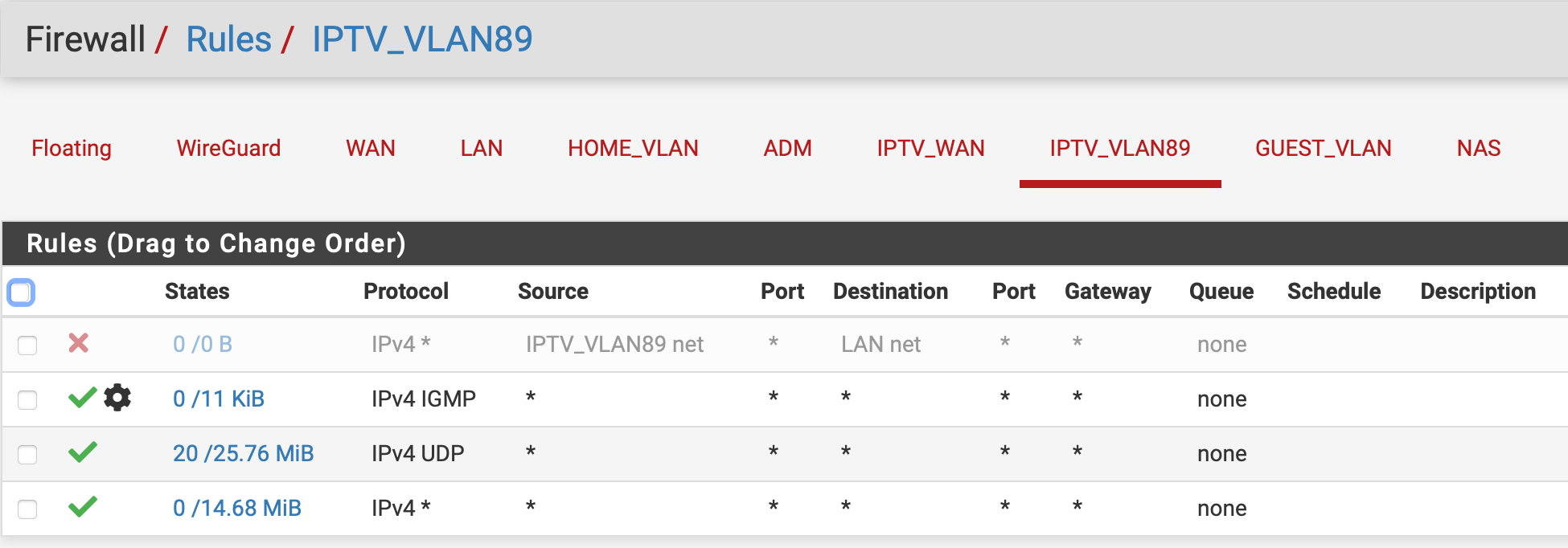
Can you guys build the firewall rules like this:
IPTV_WAN
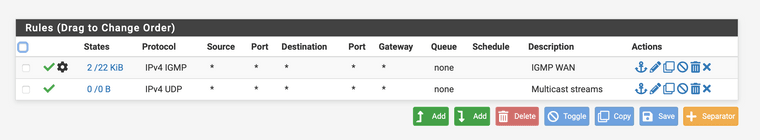
IPTV_LAN
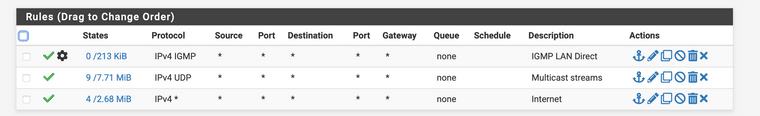
The screenshot showing that regular internet traffic is blocked, so also your DNS and TCP traffic which is needed to communicate with the streaming platform.
-
@michiel said in 23.01.b.20230106.0600 IGMP proxy stops TV stream:
@haraldinho I did several reboots. I noticed earlier that reboots help in applying the firewall rules. I think (not sure) that is has to do with the stating tables?
You can press the X next to a FW rule, to release the current state and rebuild the traffic without a reboot.
-
@haraldinho said in 23.01.b.20230106.0600 IGMP proxy stops TV stream:
Ok, pasting 45.57.40.1:443 into a browser leads to a site with a blocked Netflix certificate. So that gives some idea into what the box tries to do. The other IP, 52.19.109.21:443 does not reveal any information as far as I can see.
Indeed see my post above where I ask you to use my FW rules and delete all other rules for these two interfaces. You are blocking too much traffic which causes different issues. NTP, DNS issues but also proven by the logs that Netflix traffic is denied.
-
@thebear @haraldinho
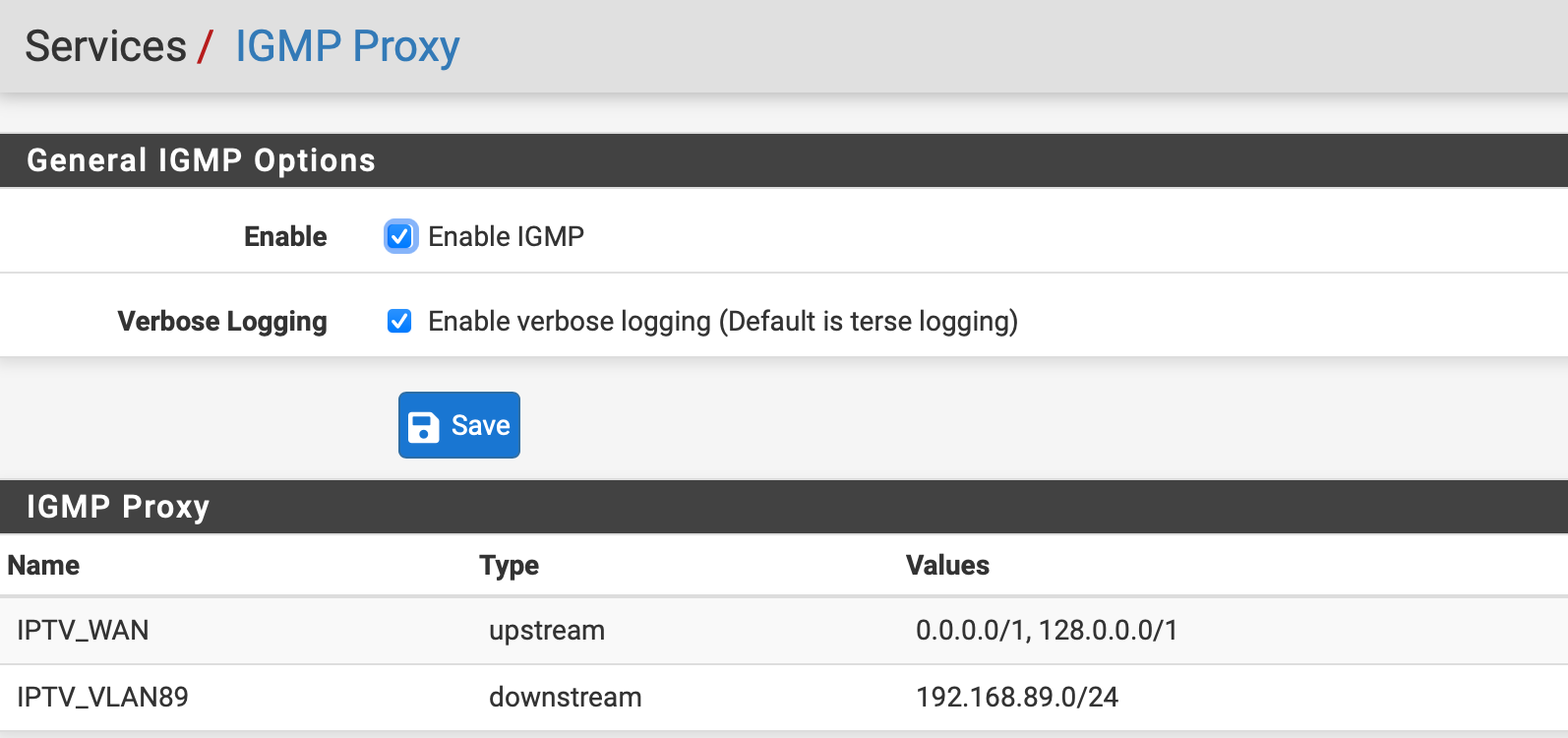
It seems I got it to work; both live TV and recordings can be paused now! See the screenshots of my settings. I will keep these settings, and see if they remain working :).I disabled the rule in IPTV VLAN to LAN net. Can I put that back, and only grant access to "This firewall" and ports 53 (DNS) and 123 (NTP)?
-
@thebear Thanks for the settings! I was busy in the past days, but this afternoon I changed my settings to match the above. I struggled a bit with the "IP Options": it took me some time to realise I had to enable those for the lines with the settings wheel in front of them to get it to work. I am currently testing to see if this resolves my issue that after some time you cannot unpause paused recordings. And I am monitoring my logs to look out for blocked calls.
Question for @thebear: it seems to me the way you have set your rules up is allowing basically all IGMP and UDP traffic into the IPTV_WAN interface, rather than from specific IP ranges? I understand it is more future proof but isn't that a security risk? -
-
Is the 213.76.112.0/21 too limited?
-
@haraldinho firewall and nat are two separate things.
Can you post your FW rules for IPTV WAN and IPTV LAN?
Via IGMP is the box requesting streams, the streams could be source from multiple subnets. Therefore its way to complex to filter on the sources, software updates comes from 10.a.b.c. and streams from other sources.
Regarding security, it's not the internet. It's a private IPTV vlan within your ISP. That reduces the risk for an attack with a million percentage. But yes hack could occur always, every minute your pfSense instance is attacked on the WAN internet interface.
-
@haraldinho My logs are clean now, no IPTV WAN and VLAN anymore. Pausing of live TV and recorded programma is working. But not at home (holidays...) so no recent experience to share.
The "cat sitter" is mostly streaming YT :). -
-
@haraldinho Same as my settings. Are your settings at NAT and IGMP also like mine (I posted them a few days ago).